Method and device for protecting program memory space through precise partitioning
A technology of program storage and storage space, which is applied to multi-program devices, specific access rights, transaction processing, etc. It can solve problems such as system resource waste and user program failure to run normally, and achieve the effect of avoiding waste
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
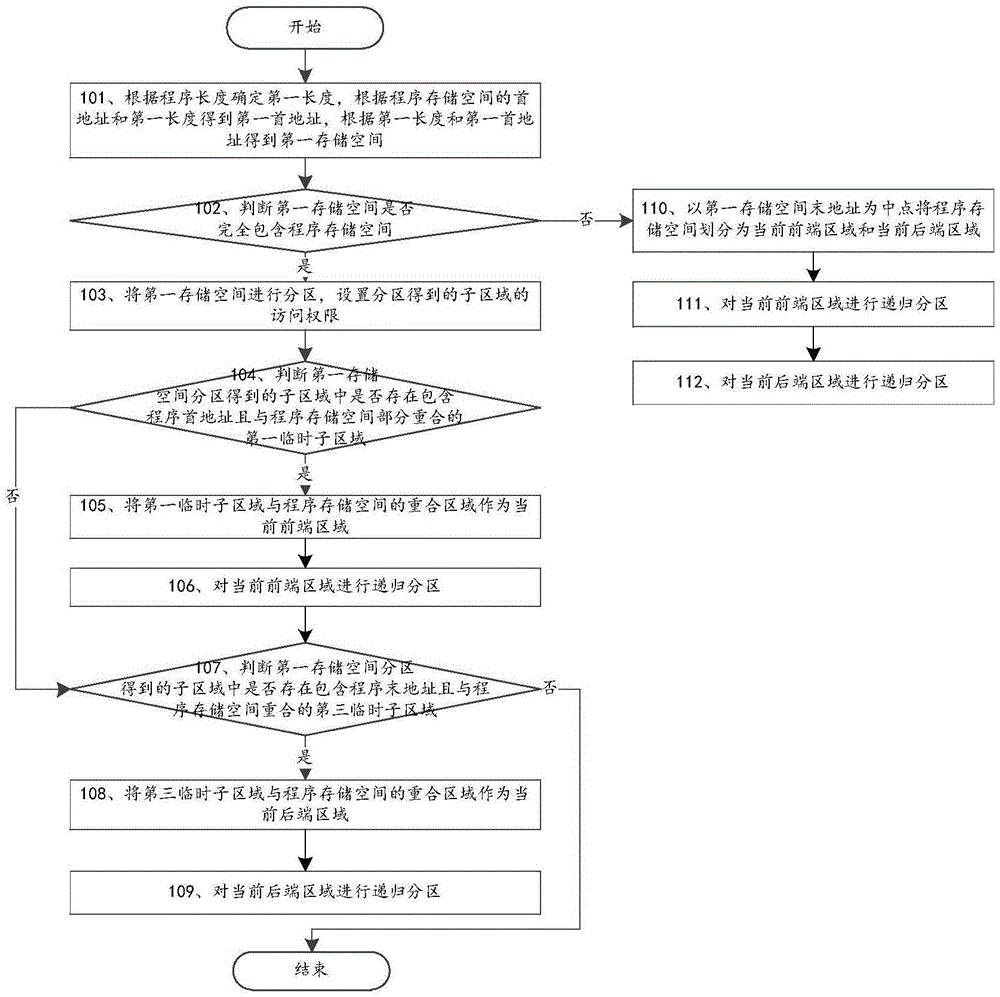
[0034] see figure 1 , a method for protecting program storage space through precise partitioning provided by the present invention, the specific steps are as follows:
[0035] Step 101: Determine the first length according to the program length, obtain the first head address according to the head address of the program storage space and the first length, and obtain the first storage space according to the first length and the first head address.
[0036] Specifically, the preset interval is determined according to the program length, and the upper boundary value of the preset interval is used as the first length. Align the first address of the program storage space to the left to an integer multiple of the first length to obtain the first first address, calculate the sum of the first first address and the first length to obtain the first end address, and combine the first first address and the first end address The storage space between is used as the first storage space.
...
Embodiment 2
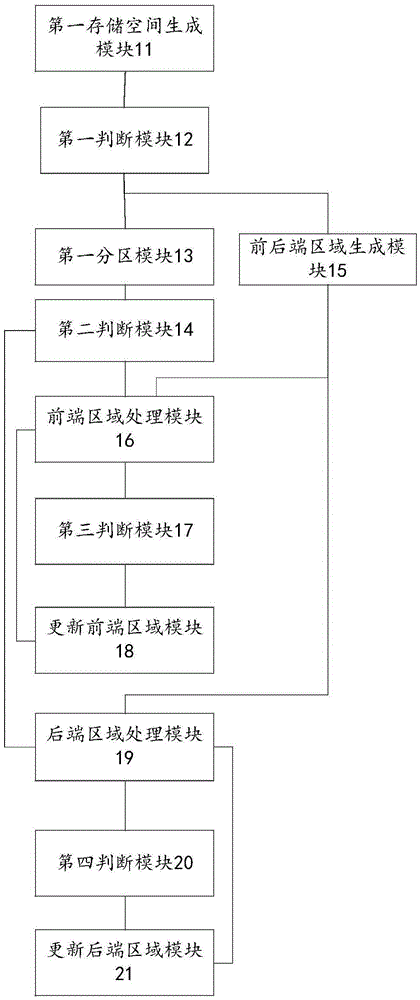
[0101] see figure 2 , the present invention provides a device for protecting program storage space through precise partitioning, including:
[0102] The first storage space generation module 11 is used to determine the first length according to the length of the program, and align the first address of the program storage space to an integer multiple of the first length to the left to obtain the first first address, according to the first first address and the first length get the first storage space;
[0103] Specifically, the first storage space generating module is specifically configured to determine the preset interval where the program length is located, use the upper boundary value of the preset interval as the first length, and align the first address of the program storage space to the left Integer multiples of the first length to obtain the first head address, and the first storage space is obtained according to the first head address and the first length.
[0104]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com