Method for processing user credibility social network data
A technology of social network and processing method, applied in the field of processing user credibility social network data, can solve the evaluation and determination of user's repayment willingness and repayment ability, the borrower's query of historical credit status, and the online evaluation of user authenticity. , difficulties in repayment ability and repayment willingness, etc., to achieve the effect of clear technical solutions and effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
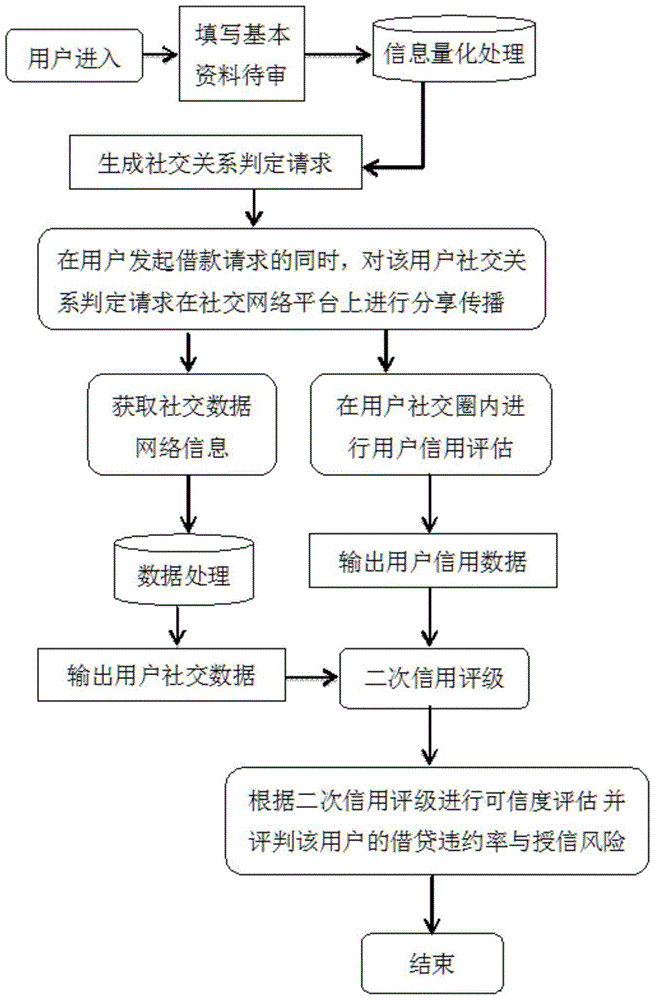
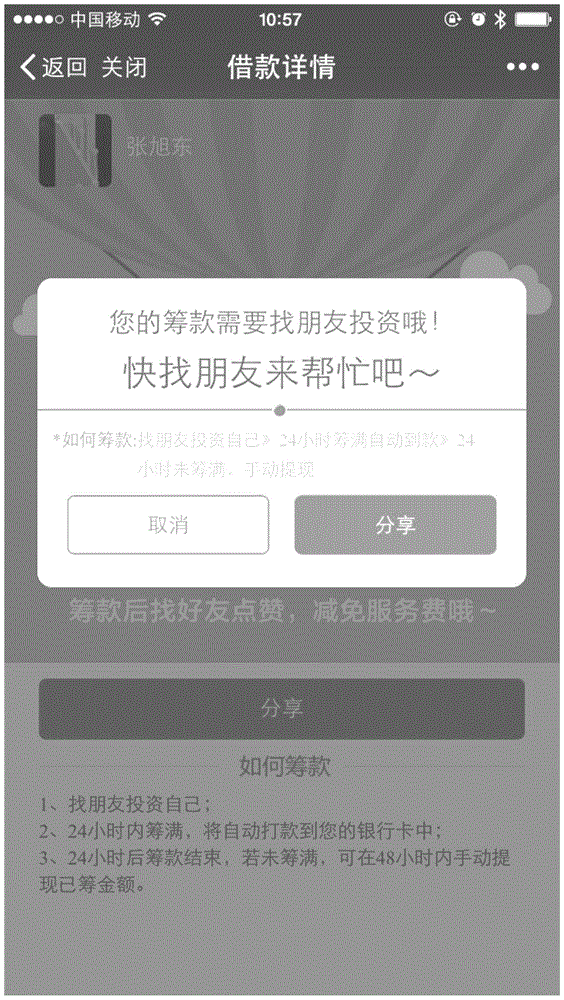
[0071] User A registers and enters the social platform through a mobile phone number and initiates a loan after completing identity authentication. The user implements the platform and requests to share the loan request to the social circle. A's friends A1, A2...A6 click the link, and record the click time and corresponding page refresh times of these 6 users. Then A1 and A2 among the 6 friends left the page, and the remaining 4 people A3, A4, A5, and A6 were guided to the next step by the page, that is, they answered the relevant questions about the identity of user A. A3 answered incorrectly, and A4 , A5, and A6 answered correctly and invested in user A. User A has raised a full amount and the data collection is complete.
[0072] For user A, based on the link A1-A6 has no abnormal values in terms of time, region, and device matching, the value of the liked relationship is 6; based on the correct answers to A4-A6 and part A3, the value of the authentication relationship i...
Embodiment 2
[0078] User B registers and enters the social platform through a mobile phone number and initiates a loan after completing identity authentication. The user implements the platform's requirements and shares the loan request to the social circle. B's friends B1, B2, and B3 click the link, and record the click time and corresponding page refresh times of these three users. Then these three friends all entered the next step, that is, answered the relevant questions about the identity of the user, all answered correctly and invested in user B, user B raised a full amount, and the data collection was completed. For user B, based on B1-B3 clicking on the link, there are no abnormal values in terms of time, region, and device matching, and the value of its like relationship is 3; based on the correct answer of B1-B3, its authentication relationship value is 3; based on B1-B3 investment If it is successful and no outliers appear, its investment relationship value is 3. At the same ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com