Method, device and system for realizing security login and security equipment
A security device and secure login technology, applied in the Internet field, can solve problems such as high-strength passwords that are inconvenient for users to remember, hash collision attacks, account theft, etc., to achieve physical isolation, ensure security, and increase difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
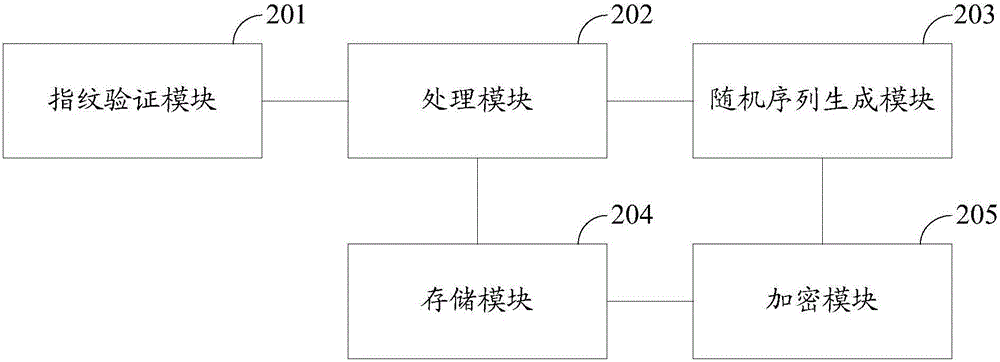
Image
Examples
Embodiment Construction
[0055] In order to make the above objects, features and advantages of the present invention more comprehensible, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
[0056] In the prior art, at least the following problems exist in the login process using username and password:
[0057](1) Setting simple passwords is more vulnerable to hash collision attacks. Nowadays, the database of many websites does not store the plaintext of the user login password, but stores the hash value of the password. Hash transformation is a one-way function. Commonly used hash transformations include MD5, SHA-1, and SHA-256. Although it is a one-way function, the hash value of the fixed string remains unchanged. If the user's password is too simple, hackers can use exhaustive methods to brute force the password after dragging it out of the website's database. For example, if the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com