Log processing method and device
A processing method and log technology, applied in the field of information processing, can solve the problems of excessive filtering of logs, ineffective filtering of information redundancy, inconsistent query and retrieval performance of security information, etc., so as to improve the real effectiveness and reduce a large amount of redundancy The effect of the log
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0041] The embodiment of the present invention provides a log processing method, which is applied to a centralized security management platform. During the specific implementation process, the centralized security management platform can be an ordinary computer or server or an industrial control computer (industrial computer), etc. The function realized by the log processing method can be realized by calling the program code by the processor in the centralized security management platform, and of course the program code can be stored in the computer storage medium; it can be seen that the centralized security management platform at least includes a processor and a storage medium.
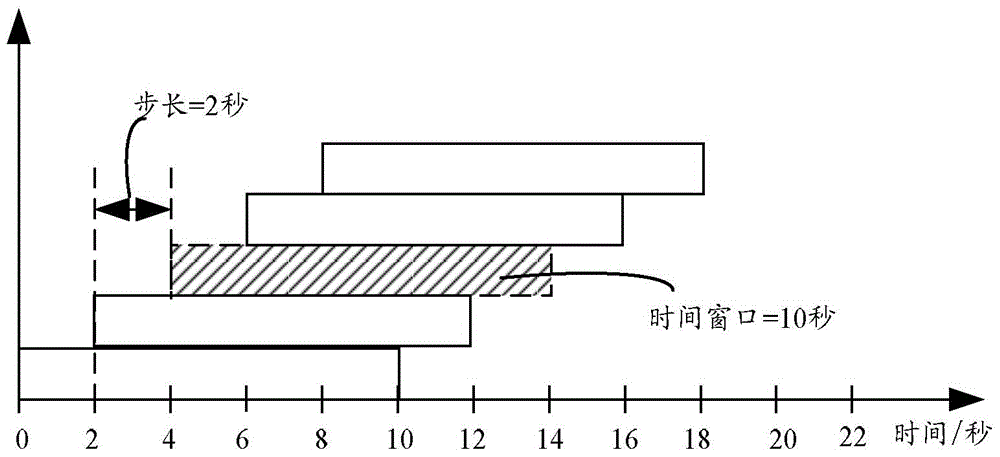
[0042] In the process of log processing, it is generally to obtain logs within a time window such as |T2-T1|=T0. As mentioned above, T1 is the initial time, and T2 is the time to obtain logs. When T2 and When T1 is different, T0 is not 0, and T0 is defined as the time window; in the process of specif...
Embodiment 2
[0072] Based on the foregoing first embodiment, the embodiment of the present invention provides a log processing method, which is applied to a centralized security management platform. During the specific implementation process, the centralized security management platform can be an ordinary computer or server or an industrial control computer (industrial personal computer) and other equipment, the function realized by the log processing method can be realized by the processor in the centralized security management platform calling the program code, of course the program code can be stored in the computer storage medium; it can be seen that the centralized security management platform includes at least processor and storage media.
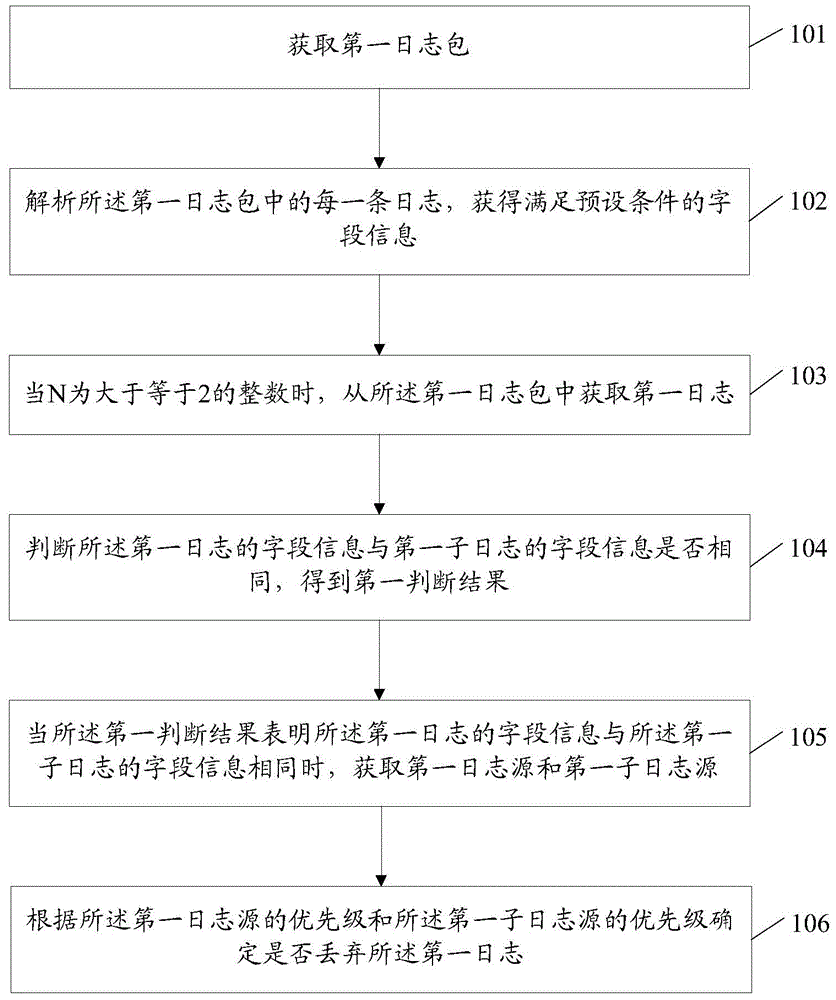
[0073] figure 2 It is a schematic diagram of the implementation flow of the log processing method in Embodiment 2 of the present invention, as figure 2 As shown, the method includes:
[0074] Step 201, obtaining the first log package;
[0075...
Embodiment 3
[0095] The embodiment of the present invention provides a log processing method, which is applied to a centralized security management platform. During the specific implementation process, the centralized security management platform can be an ordinary computer or server or an industrial control computer (industrial computer), etc. The function realized by the log processing method can be realized by calling the program code by the processor in the centralized security management platform, and of course the program code can be stored in the computer storage medium; it can be seen that the centralized security management platform at least includes a processor and a storage medium.
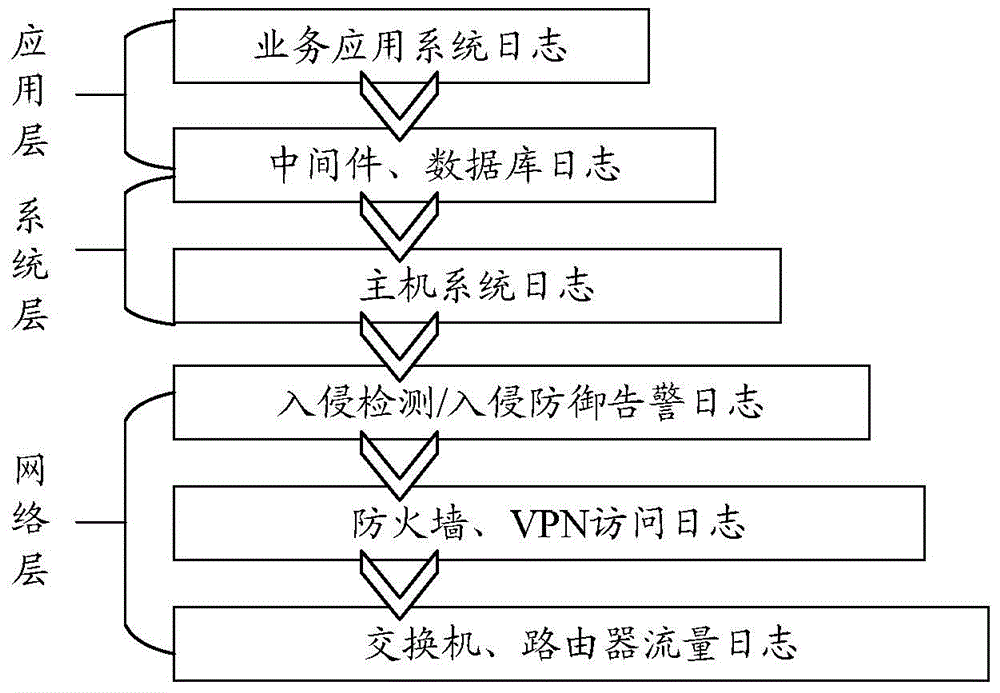
[0096] exist Figure 1-3 In the illustrated embodiment, the processing of a log within a time window is taken as an example for illustration. exist image 3 In the illustrated embodiment, based on the foregoing image 3 The processing method of processing a log described in the illustrated embodim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com