Cache infection detection method and apparatus based on deep analysis on DNS message
A technology of in-depth analysis and detection device, which is used in digital transmission systems, electrical components, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
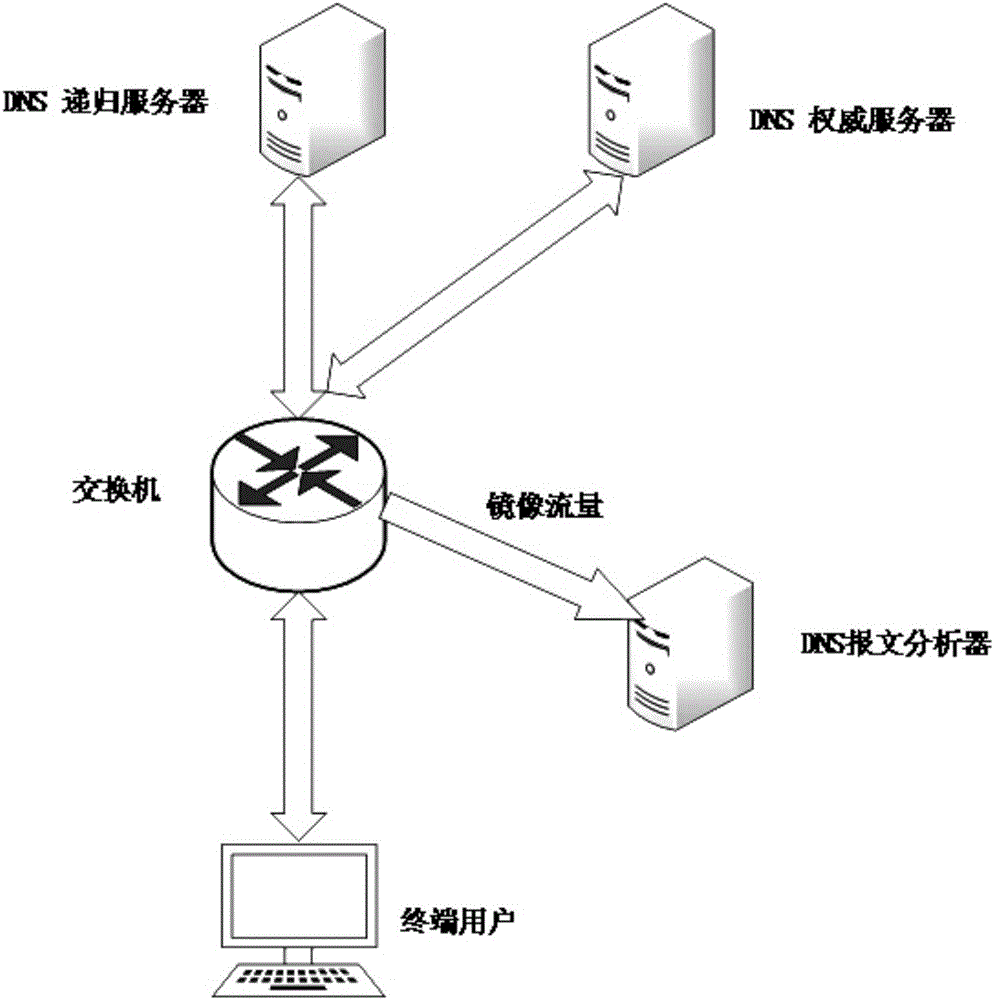
[0028] The deployment of the DNS cache poisoning detection device of the present invention in the network is as follows: figure 1 As shown, the DNS traffic between the DNS recursive server and the DNS authoritative server and between the DNS recursive server and the DNS end user is mirrored to the DNS packet analyzer through the switch for DNS cache poisoning detection.
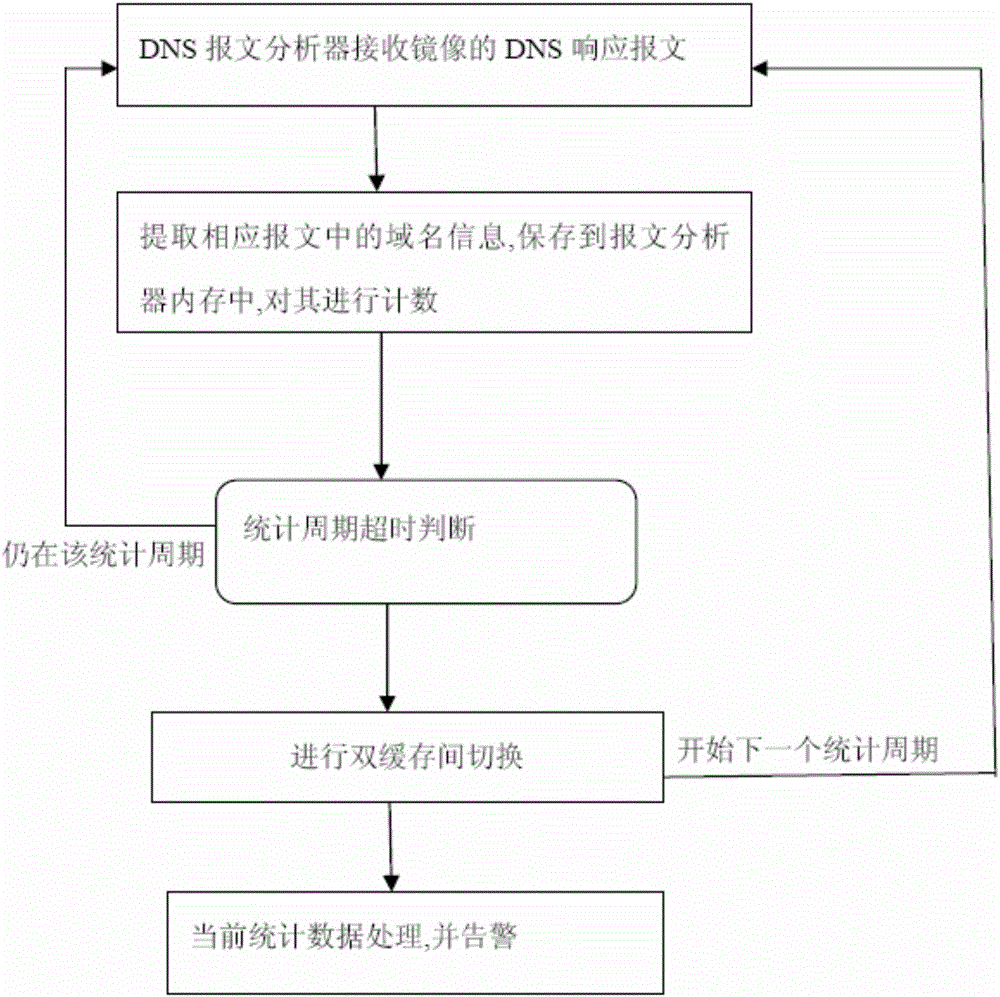
[0029] The DNS cache poisoning detection process of this embodiment is as follows figure 2 shown. Its steps are described as follows:
[0030] For DNS recursive servers and DNS authoritative servers:
[0031] 1) The DNS packet analyzer receives DNS traffic between the mirrored DNS recursive server and the DNS authoritative server.
[0032] 2) The DNS message analyzer parses the network domain name address information in the DNS response message, saves it in the memory of the DNS message analyzer, and counts the number of responses to the domain name.
[0033] 3) When the statistical period (eg, 1 minute)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com