Login method and system
A login method and a login system technology, applied in the login method and system fields, can solve problems such as potential safety hazards, impact on Internet user information security, huge losses, etc., and achieve the effect of avoiding unnecessary losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
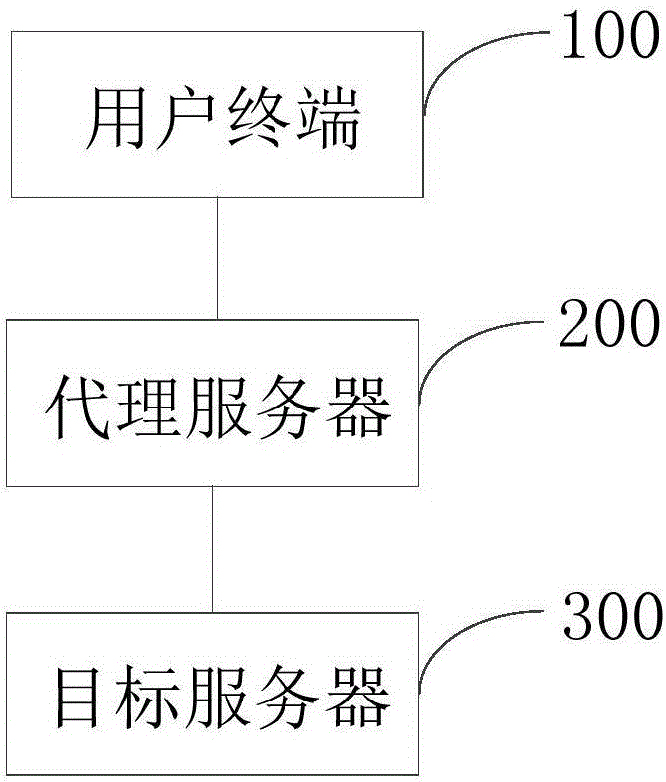
[0037] like figure 1 Shown is a system block diagram of the login system provided by the preferred embodiment of the present invention. The login system includes a user terminal 100, a proxy server 200 and a target server 300. The user terminal 100 is used to log in to the proxy server 200 through the first account information, and the proxy server 200 is used to log in the user terminal 100 through the first account information. Forward the second account information uploaded by the user terminal 100 to the target server 300, and after receiving the second account information forwarded by the proxy server 200, the target server 300 feeds back to the proxy server 200 a first security pass information bound to the second account information , so that when the user terminal 100 logs in to the target server 300 again, it can directly log in to the target server 300 through the first security pass information stored in the proxy server 200 .
[0038] Taking the login to the Taoba...
no. 2 example
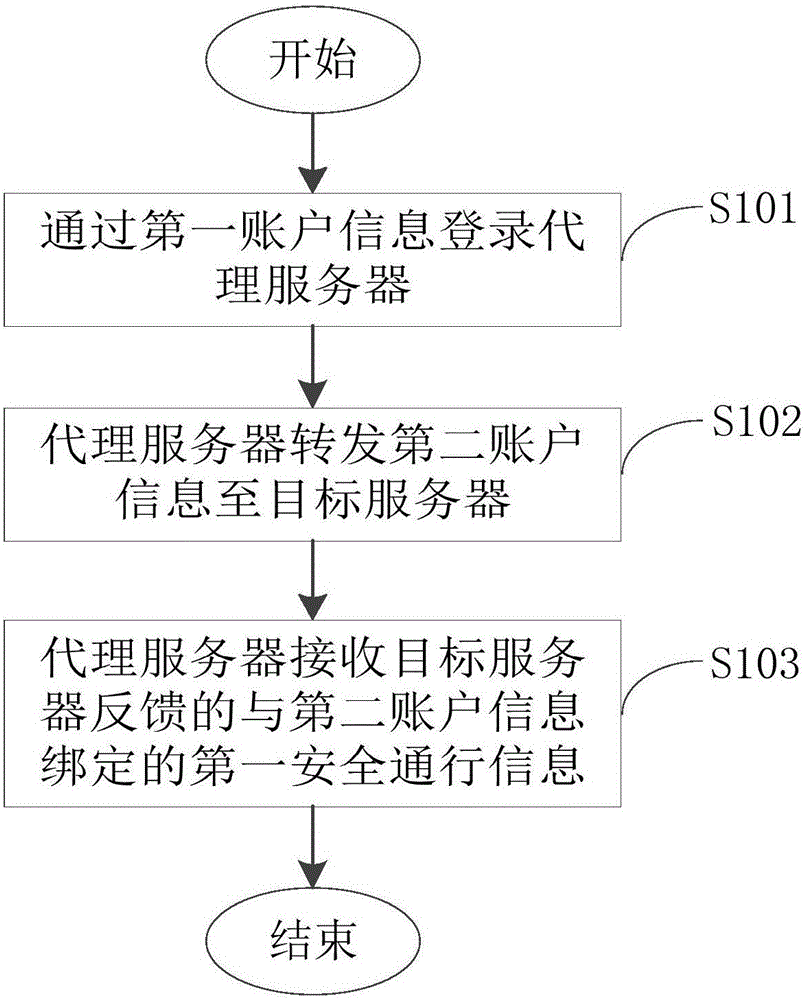
[0043] see figure 2 , is a flow chart of the login method provided by the preferred embodiment of the present invention. The following will be figure 2 The specific process shown will be described in detail.
[0044] The method provided by the embodiment of the present invention is used to realize quick and convenient login to the target server through the proxy server, and is especially suitable for the situation where multiple different website servers correspond to multiple different accounts. It includes the following steps.
[0045] Step S101: Log in to the proxy server through the first account information.
[0046] When using the method provided by the embodiment of the present invention to log in to the target server for the first time, first, the user terminal logs in to the proxy server through the web interface provided by the proxy server through the first account information (account number and password, etc.) that has successfully registered with the proxy s...
no. 3 example
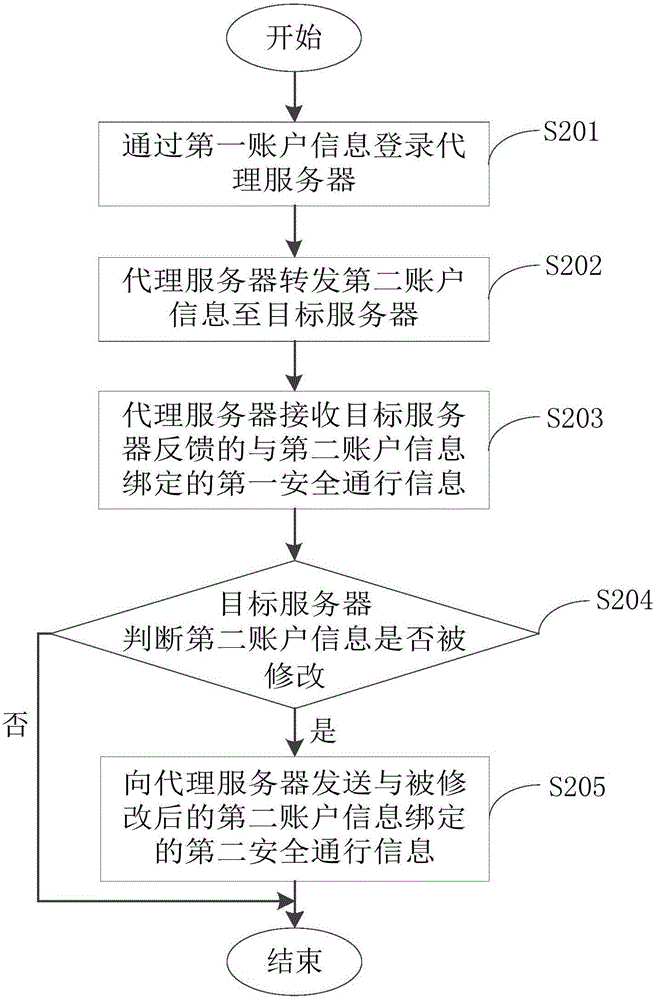
[0055] see image 3 , is a flowchart of another login method provided by a preferred embodiment of the present invention. The following will be image 3 The specific process shown will be described in detail.
[0056] Step S201: Log in to the proxy server through the first account information.
[0057] Step S202: the proxy server forwards the second account information to the target server.
[0058] Step S203: the proxy server receives the first safe pass information bound with the second account information fed back by the target server.
[0059] Step S204: the target server determines whether the second account information has been modified.
[0060] Since the first security pass information generated by the target server is bound to the second account information forwarded to it by the proxy server, when certain information in the second account information used to log in to the target server (such as password or user contact information, etc.) After being modified by ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com