Network private key generating and applying method and system for mobile terminal
A mobile terminal, private key technology, applied in the field of computer and information security, can solve the problems of no PIN protection, loss of applicability and security, affecting Internet use and rapid development, etc., to overcome security defects and improve security and efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The technical solutions of the present invention will be further specifically described below through examples.
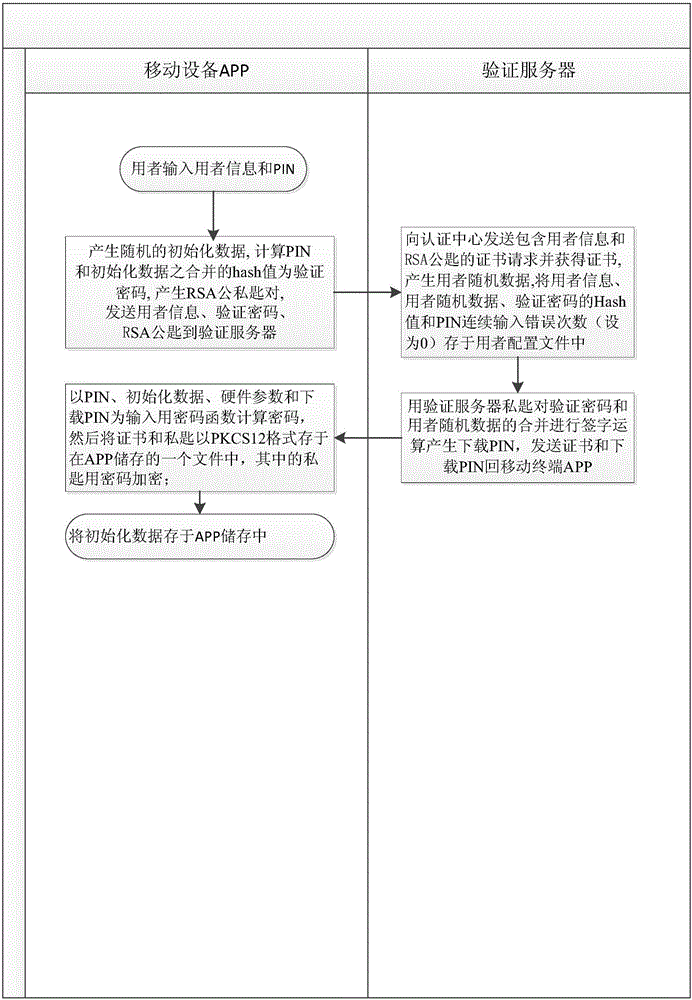
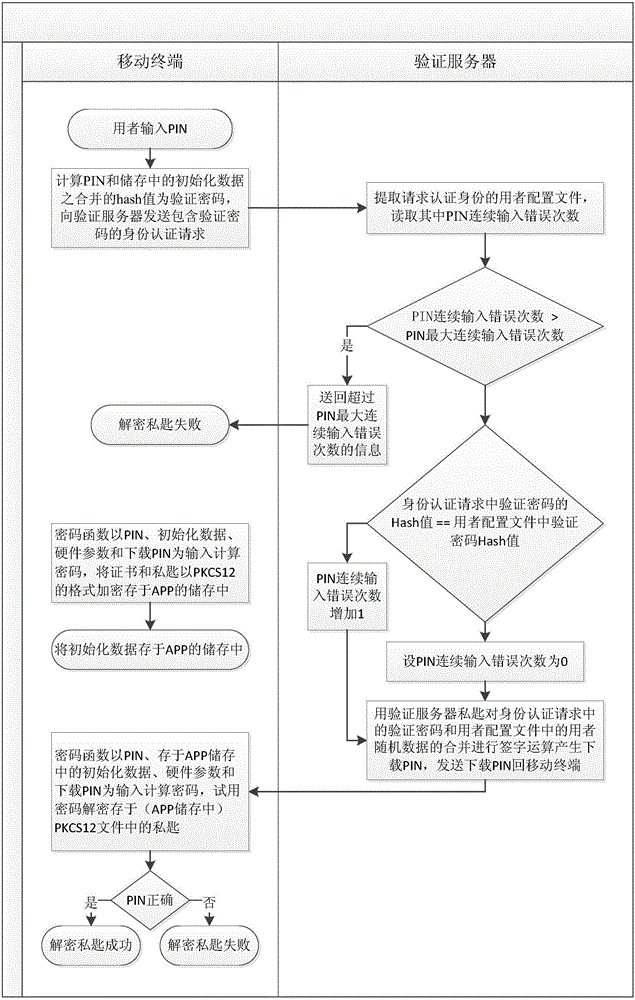
[0043] Unlike the software private key in the prior art, which puts the data and calculations for decrypting the private key on the same terminal, for the network private key of the present invention, part of the data and calculations for decrypting the private key are moved to the verification server , and the verification server sets the maximum number of consecutive incorrect PIN inputs to prevent unlimited input of various PINs. The specific solution of the present invention is described below through an embodiment, that is, how the APP on the mobile terminal initializes, encrypts and decrypts the private key.
[0044] (1) Initialize and encrypt the private key
[0045] figure 1 It is a schematic flow chart of initializing and encrypting a private key in a preferred embodiment of the present invention.
[0046] First, the user inputs user information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com