Access control method and device
An access control and access request technology, applied in the field of network communication, can solve problems such as increasing SSO system load, application system paralysis, application server overload, etc., to achieve the effect of reducing overload, reducing access requests, and improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The network architecture and business scenarios described in the embodiments of the present invention are to more clearly illustrate the technical solutions of the embodiments of the present invention, and do not constitute limitations on the technical solutions provided by the embodiments of the present invention. The evolution of the architecture and the emergence of new business scenarios, the technical solutions provided by the embodiments of the present invention are also applicable to similar technical problems.
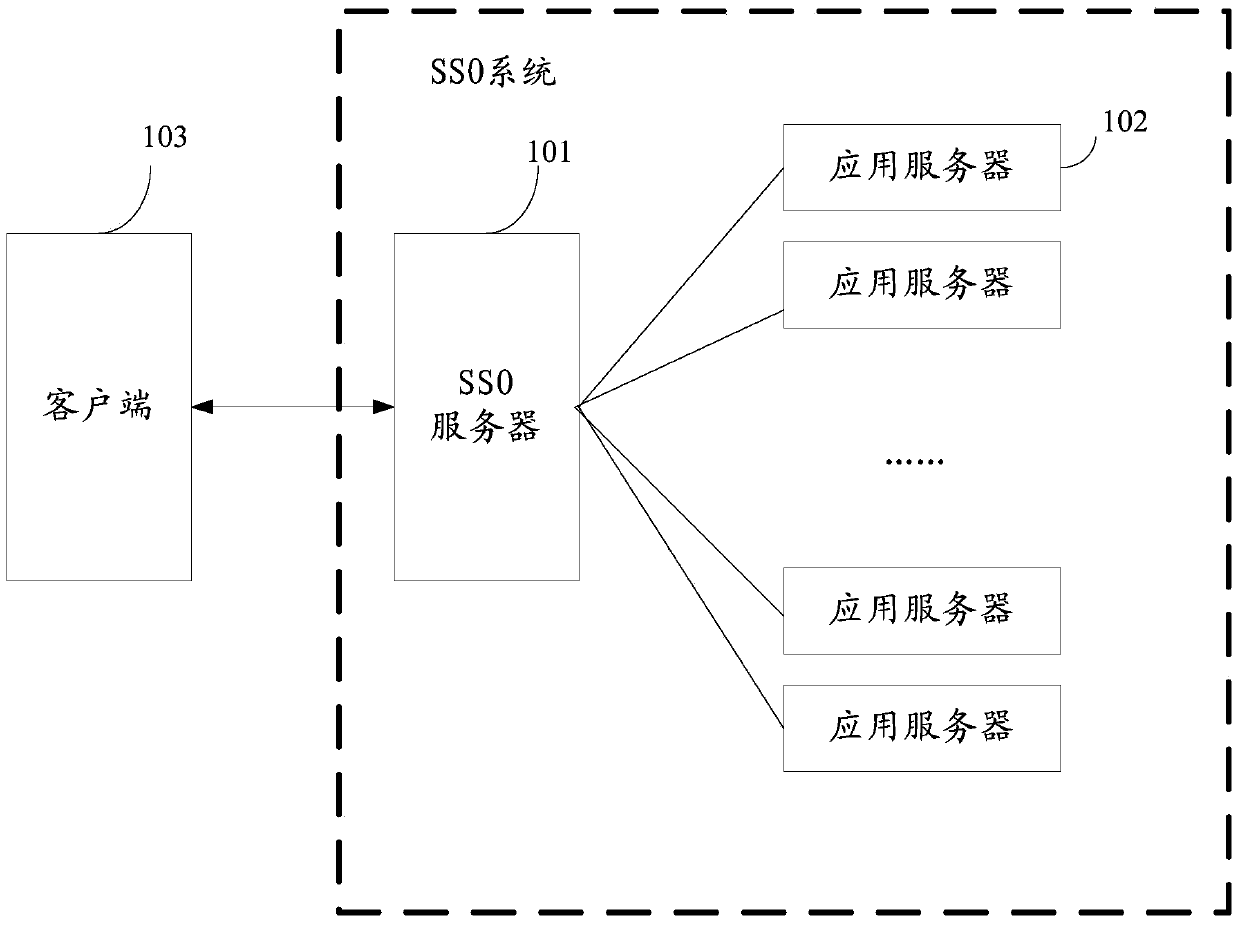
[0032] For ease of understanding, a possible application scenario of the embodiment of the present application is introduced. see figure 1 , in this application scenario, the single sign-on (SSO, Single Sign On) system may include: an SSO server 101 and multiple application services may be connected to multiple application servers 102 through a network.
[0033] The SSO server 101 is associated with the plurality of application servers 102 , so that the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com