Network access control method and system
A network access control and access volume technology, applied in the field of network access control methods and systems, can solve the problems of IP address error interception, large delay in analyzing log files, and inability to intercept blacklisted IP addresses in a timely and accurate manner, so as to reduce delays. Time and effect of guaranteed access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
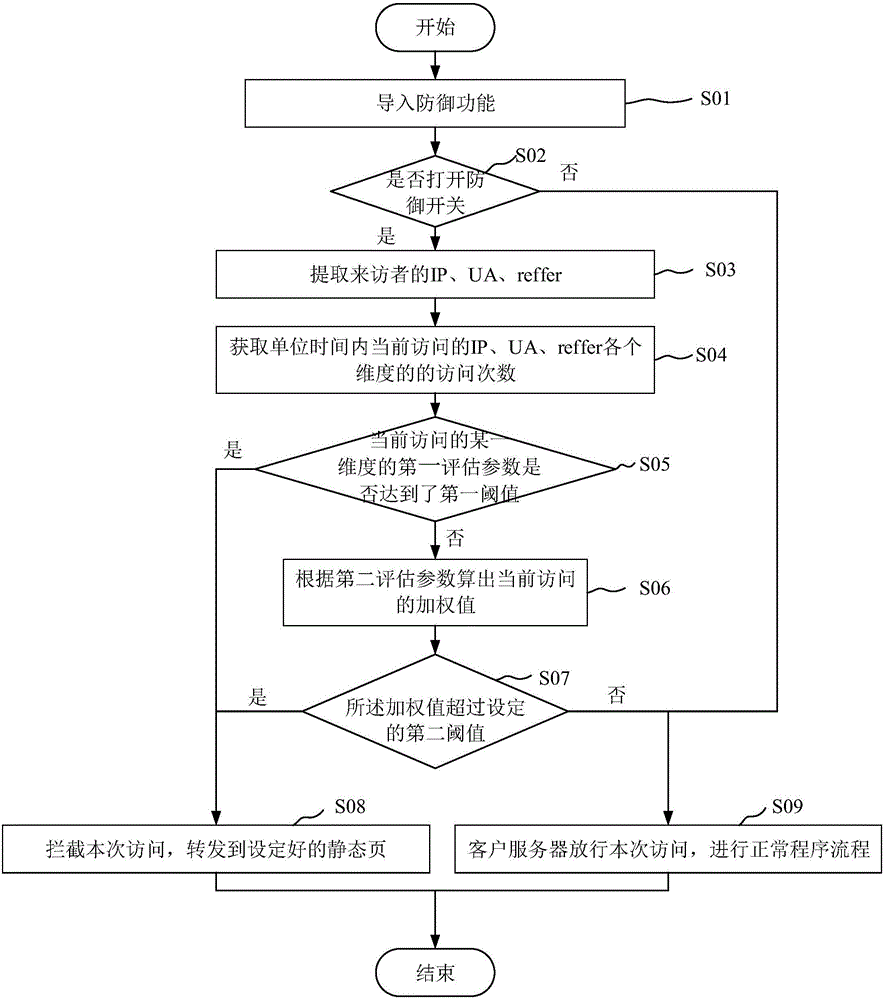
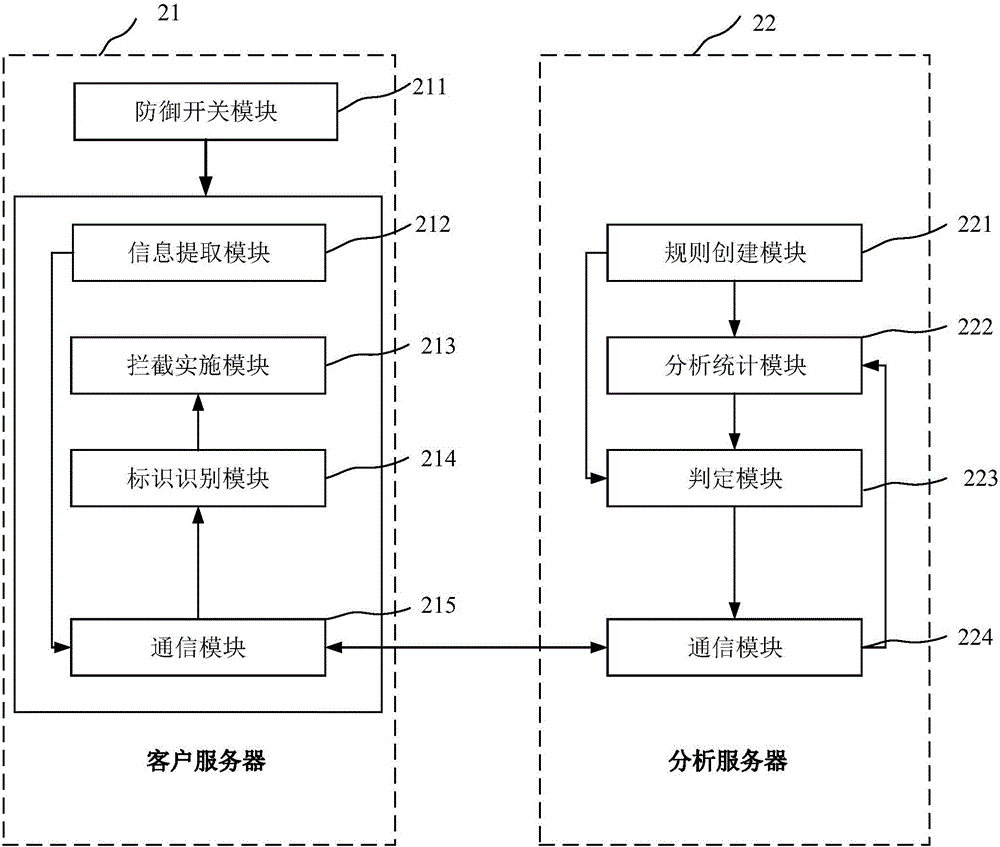
[0038] The present invention is described below based on examples, but the present invention is not limited to these examples. In the following detailed description of the invention, some specific details are set forth in detail. The present invention can be fully understood by those skilled in the art without the description of these detailed parts. In order to avoid obscuring the essence of the present invention, well-known methods, procedures, and flow charts are not described in detail. Additionally, the drawings are not necessarily drawn to scale.
[0039] The flow charts and block diagrams in the accompanying drawings illustrate the possible system framework, functions and operations of the methods, systems, and devices of the embodiments of the present invention, and the blocks on the flow charts and block diagrams can represent a module, program segment or just a segment Code, said modules, program segments and codes are all executable instructions for implementing p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com