Identity card reading terminal and cloud authentication platform authentication method and system
A technology of card reading terminal and ID card, which is applied in the electronic field, can solve the problems of high manufacturing cost of ID card reader and low utilization rate of ID card reader, etc., and achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
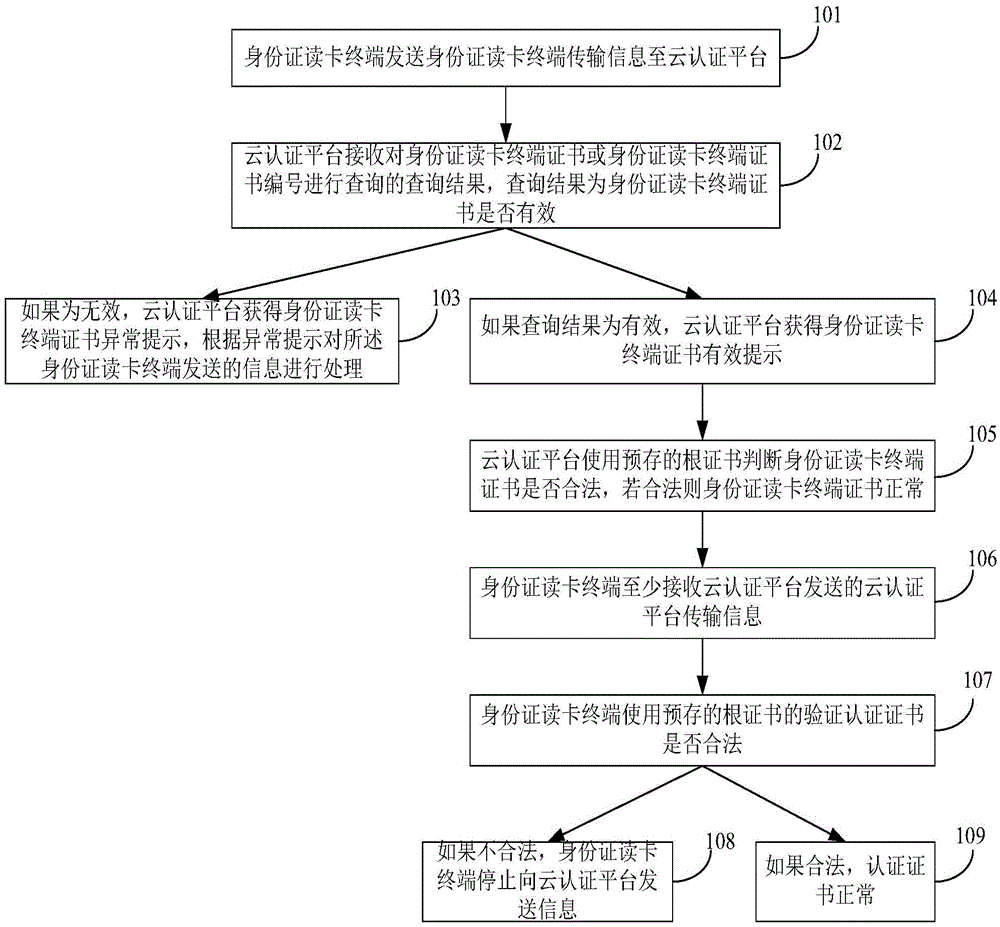
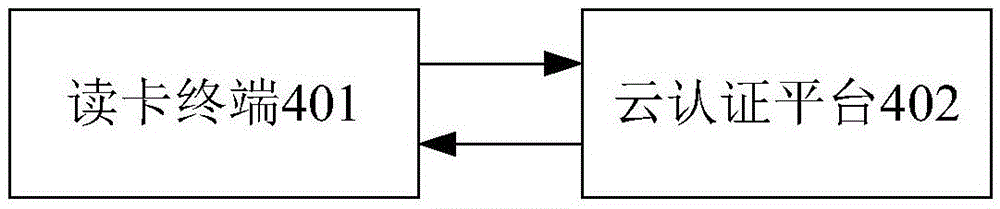
[0025] figure 1 An authentication method for an ID card reader terminal and a cloud authentication platform provided for this embodiment, such as figure 1 As shown, the authentication method between the ID card reader terminal and the cloud authentication platform provided by this embodiment mainly includes the following steps (101-109).
[0026] Step 101: The ID card reading terminal sends the ID card reading terminal transmission information to the cloud authentication platform, the ID card reading terminal transmission information includes at least the ID card reading terminal certificate, and the ID card reading terminal certificate includes at least: ID card reading terminal The terminal certificate content information is the signature information of the ID card reading terminal certificate obtained by signing the ID card reading terminal content information, wherein the ID card reading terminal content information includes at least the ID card reading terminal certificat...
Embodiment 2
[0048] An authentication method for an ID card reader terminal and a cloud authentication platform provided by this embodiment belongs to the same idea as Embodiment 1, and the similarities with Embodiment 1 will not be repeated. The following only focuses on the differences between this embodiment and Embodiment 1. to explain:
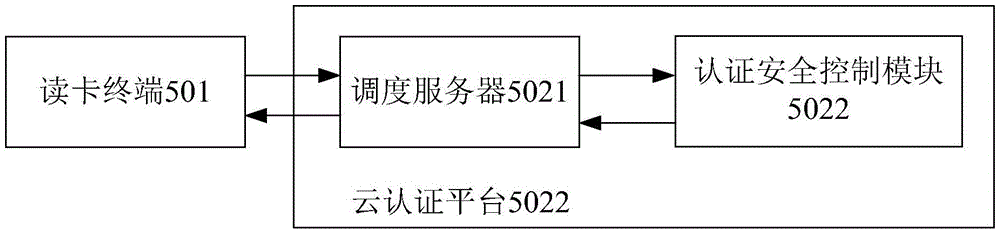
[0049] In this embodiment, the cloud authentication platform further includes at least one scheduling server and at least one authentication security control module. The scheduling server receives the information transmitted by the ID card reading terminal and verifies whether the certificate of the ID card reading terminal is normal. If the terminal certificate is normal, the scheduling server sends the transmission information of the ID card reader terminal to the authentication security control module that meets the preset conditions. The authentication security control module generates the transmission information of the cloud authentication platfo...
Embodiment 3
[0070] An authentication method for an ID card reader terminal and a cloud authentication platform provided by this embodiment belongs to the same idea as Embodiment 1 and Embodiment 2, and the same points as Embodiment 1 or Embodiment 2 will not be repeated here. The following is only for this embodiment The differences between embodiment 1 and embodiment 2 are described:
[0071] In this embodiment, the cloud authentication platform further includes at least one scheduling server and at least one authentication security control module, the scheduling server receives the transmission information of the ID card reader terminal, and sends the transmission information of the ID card reader terminal to the authentication security control module, by The authentication security control module verifies whether the ID card reader terminal certificate is normal, and the certification result of the authentication security control module certificate is sent to the dispatch server. If the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com