Authentication and pairing of devices using a machine readable code
A readable code and machine technology, applied in branch office equipment, connection management, network topology, etc., can solve problems such as unresolved users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
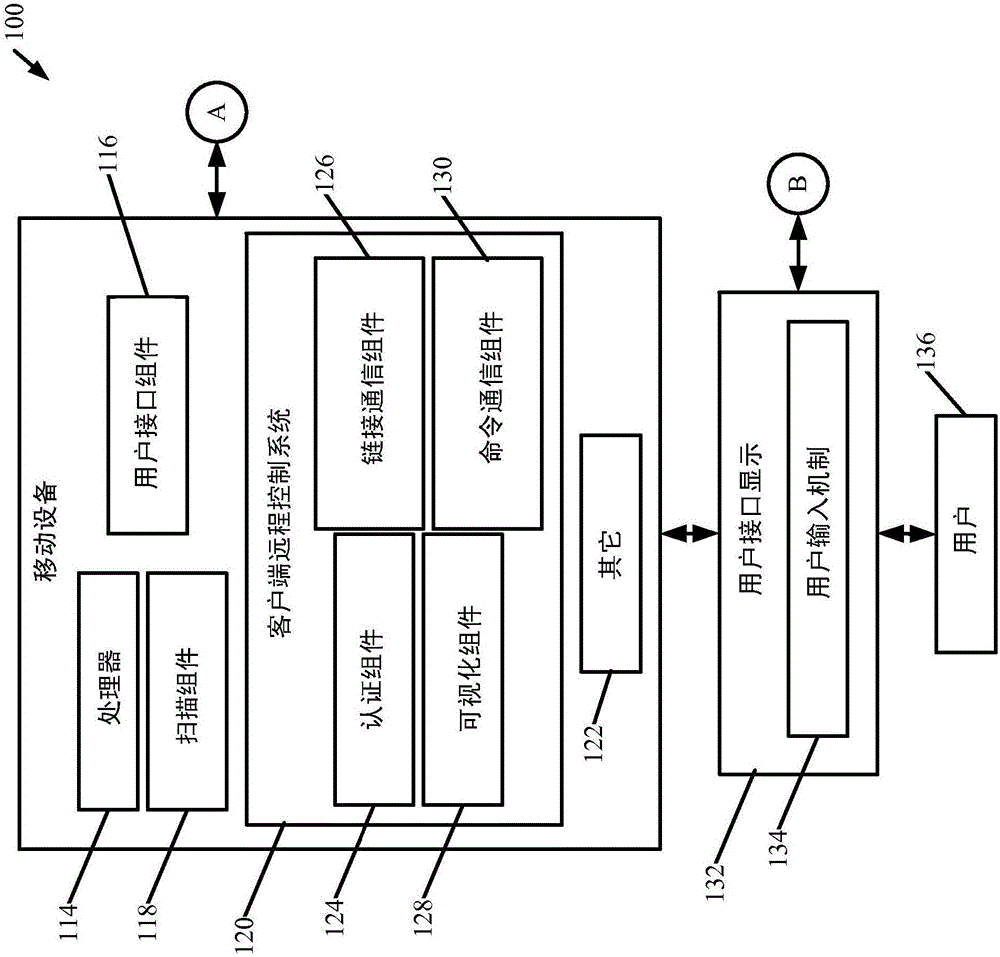
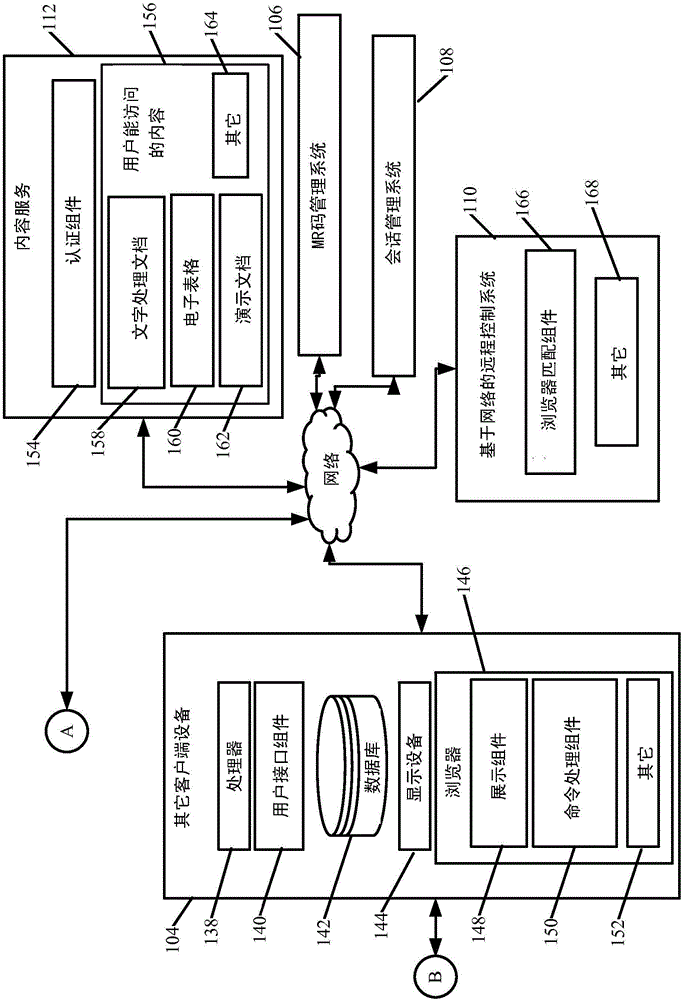
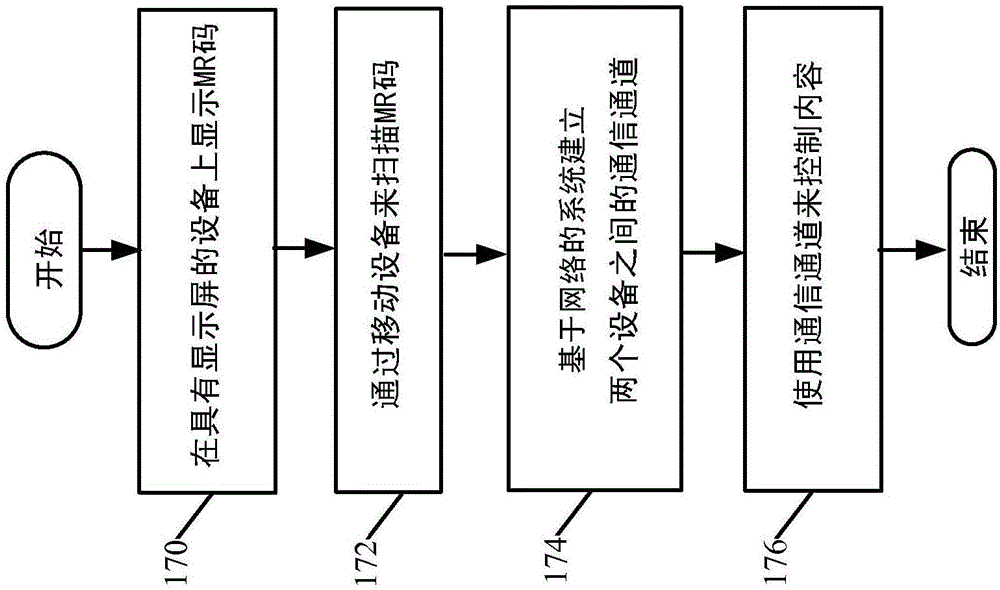
[0021] Picture 1-1 and 1-2 (collectively referred to as FIG. 1 ) shows a block diagram of an exemplary authentication and pairing architecture 100 . Architecture 100 includes mobile device 102 , another client device 104 , a set of web-based services including MR code management system 106 , session management system 108 , and web-based remote control system 110 . A set of content services 112 is also illustratively included. In the embodiment shown in FIG. 1 , the mobile device 102 exemplarily includes a processor 114, a user interface component 116, a scanning component 118, and a client remote control system 120 (which may be a mobile application running on the mobile device 102) , and may also include other components 122 .
[0022] Architecture 100 will be described herein in connection with the example where the MR code is an optical code scanned by scanning component 118 . However, the MR code may also be other MR codes, such as codes provided using near field commu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com