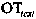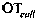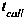Event trigger implicit identity verification method based on mobile equipment
An identity verification method and mobile device technology, applied in the field of event-triggered implicit identity verification based on mobile devices, can solve problems such as low verification efficiency, large amount of user data, and susceptibility to objective factors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] refer to figure 1 According to the present invention, a mobile device-based trigger event triggers an implicit identity verification method. The specific steps are as follows:
[0043] In order to illustrate the specific implementation of the present invention more clearly, first, necessary explanations are given to the concepts of trigger event type, trigger event confidence table, user confidence flow, and decision threshold involved in the present invention.
[0044] The types of triggering events are receiving or sending mobile phone text messages, incoming and outgoing calls, changes in browser browsing history, and changes in WIFI access history. When the trigger event Event occurs, the mobile phone conducts implicit authentication.
[0045] The trigger event confidence table represents the trustworthiness of the trigger event, including SMS statistics, call statistics, web page browsing statistics, and WIFI access statistics. refer to figure 2 , the content o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com