Security management method and device
A technology for security management and designated files, which is applied in the computer field, can solve problems such as the difficulty of ordinary users, and achieve the effect of protecting system security and preventing malicious behaviors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
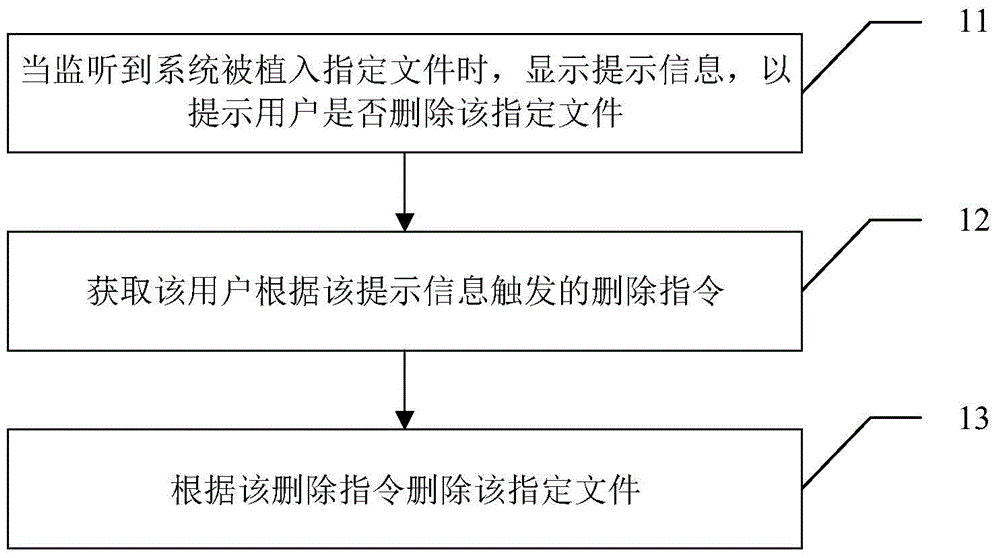
[0029] see figure 1 , the first embodiment of the present invention provides a security management method, the method includes:
[0030] Step 11, when it is detected that the system is implanted with a specified file, a prompt message is displayed to prompt the user whether to delete the specified file, wherein the specified file is used to help an application program that does not have the superuser permission to obtain the superuser permission;
[0031] Monitor various operations of various applications in the system in real time in the background, and display a prompt message when it detects that an application has implanted a specified file into the system. The prompt information may include a button for triggering a delete instruction or a no-delete instruction, which is used to prompt and guide the user to choose whether to delete the specified file.
[0032] Wherein, the specified file is used to help an application program without Root permission to obtain Root permis...
no. 2 example
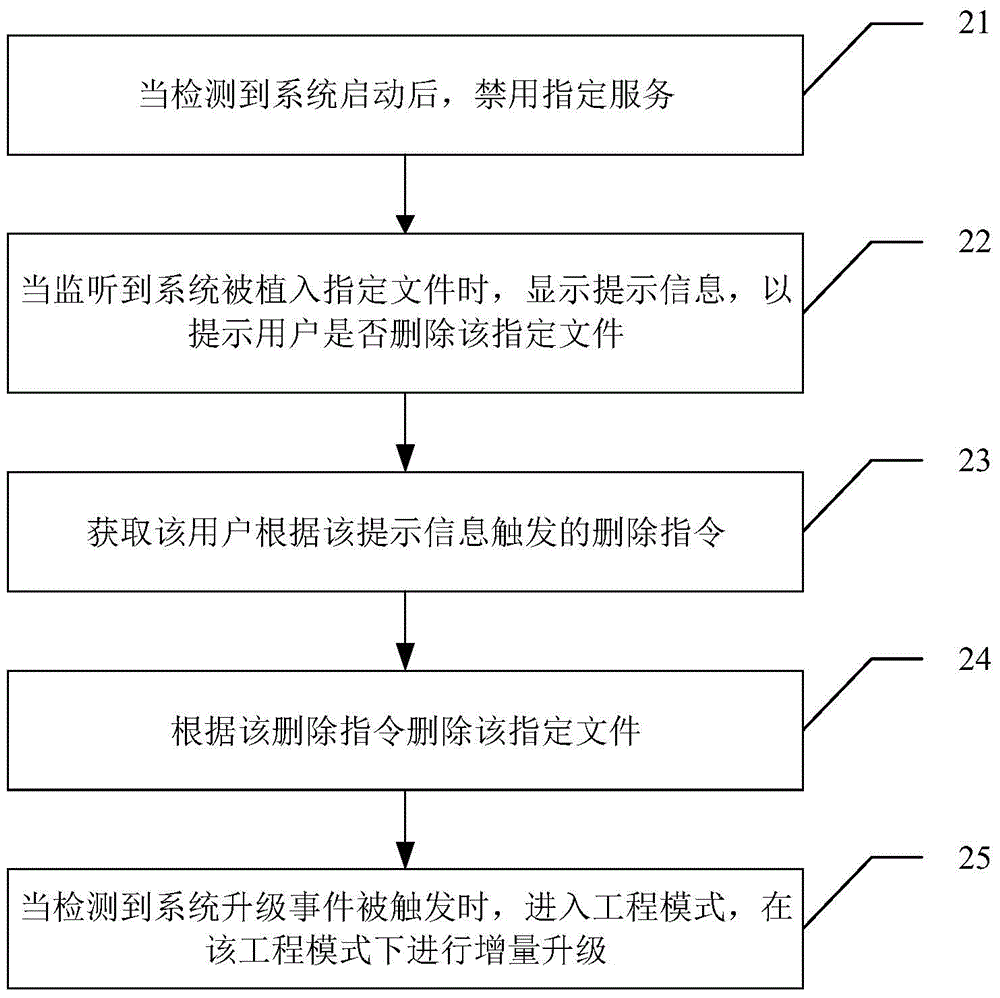
[0039] see figure 2 , the second embodiment of the present invention provides a security management method, the method comprising:
[0040] Step 21, after detecting that the system starts, disable the specified service;
[0041] Regardless of the Linux kernel (kernel) or the Android system, there are some loopholes. For different loopholes, different third-party Root tool programs have different principles and schemes for obtaining Root permissions. Implanting a specific file, that is, establishing a channel between the system and the application program, so that the application program can obtain Root authority through the channel.
[0042] Specifically, the third-party root tool program first stores related tool programs for cracking the system in the userdata folder, then searches for system vulnerabilities, obtains root privileges, and remounts the system under the prerequisite of obtaining root privileges, and uploads the system to the system Implant the above-mentione...
no. 3 example
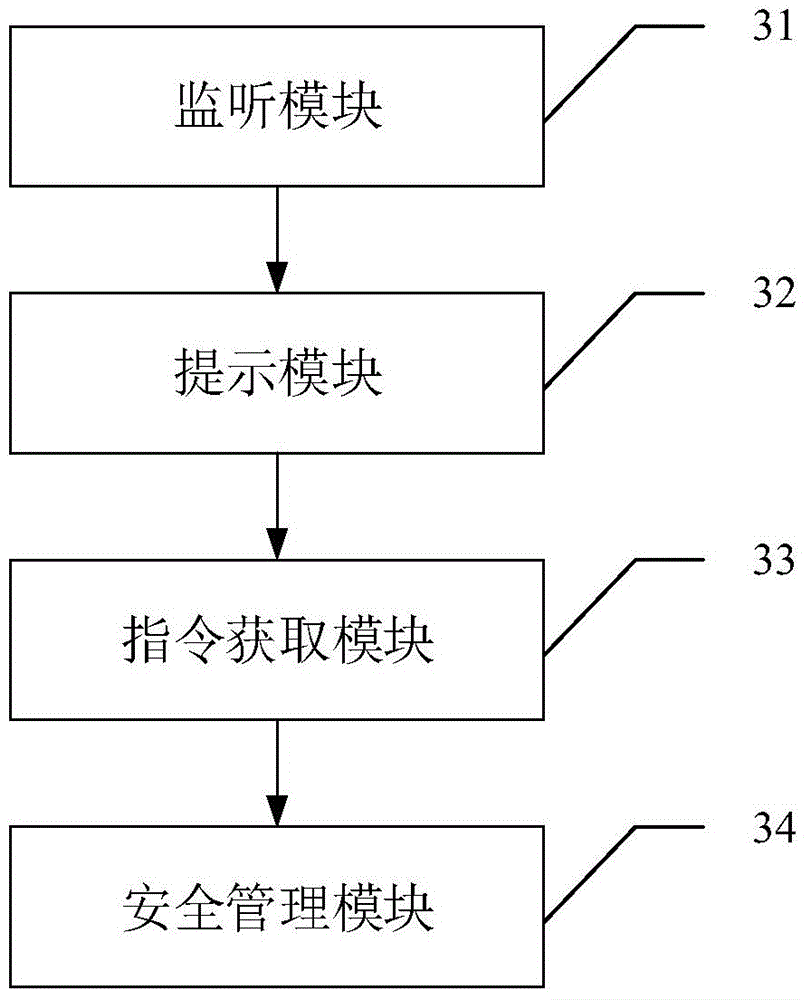
[0064] see image 3 , the third embodiment of the present invention provides a safety management device, the device includes:
[0065] A monitoring module 31, configured to monitor whether the system is implanted with a specified file;
[0066] The prompting module 32 is used to display prompt information when the monitoring module 31 detects that the system is implanted with a specified file to prompt the user whether to delete the specified file, wherein the specified file is used to help an application program that does not have superuser authority to obtain the specified file. superuser privileges;
[0067] An instruction obtaining module 33, configured to obtain the deletion instruction triggered by the user according to the prompt information;
[0068] The security management module 34 is configured to delete the specified file according to the deletion instruction acquired by the instruction acquisition module 33 .
[0069] For other details of implementing the techn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com