Method for improving security of IPv6 protocol data packets
An ipv6 protocol and data packet technology, which is applied in the direction of secure communication devices, digital transmission systems, user identity/authority verification, etc., can solve problems such as unresolved source address counterfeiting, fault bottlenecks, etc., and achieve enhanced accountability and prevention of heavy-duty Unleash aggressive behavior and reduce the effect of fake aggressive behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described in detail below in combination with specific embodiments and with reference to the accompanying drawings. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
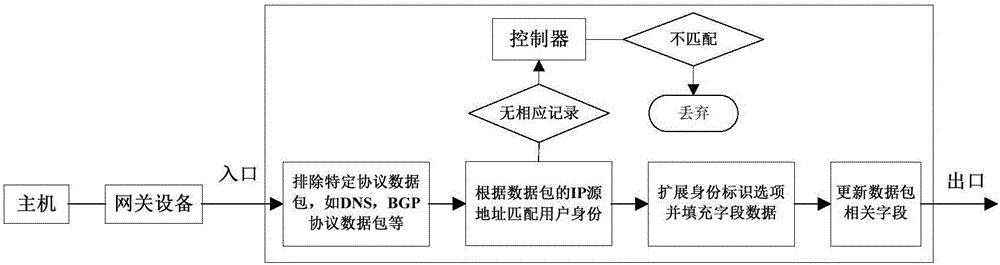
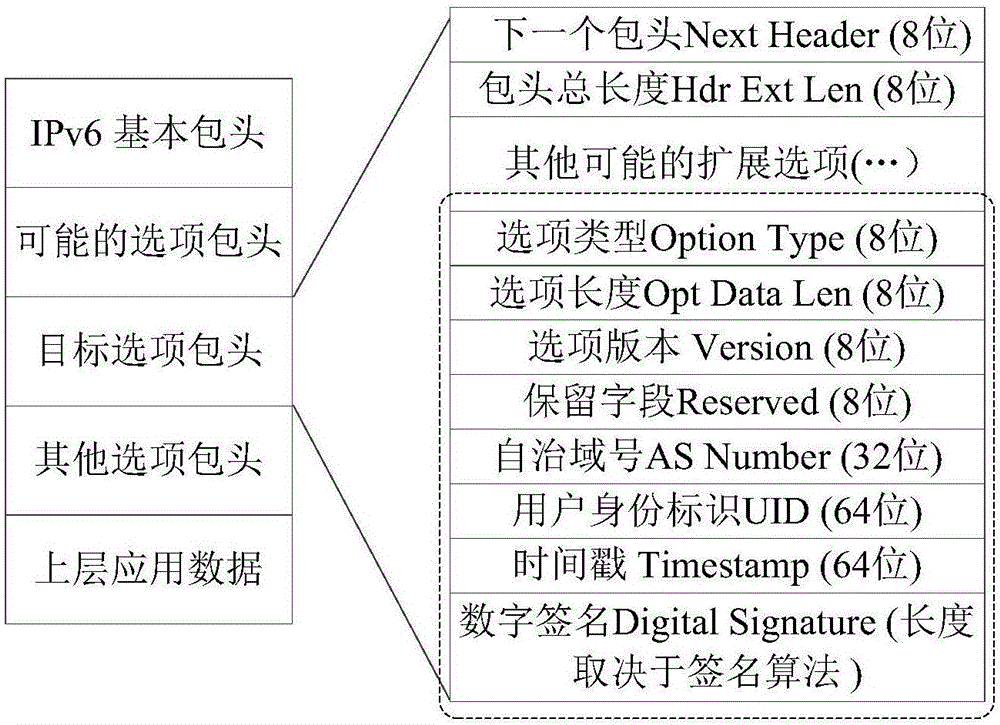
[0025] Such as figure 1 As shown, the present invention can use the programmable user network access device or the overall network exit device (hereinafter referred to as "device") to extend the identity identification option proposed by the present invention to the user data packet. Further, the embodiment includes the following steps:
[0026] A0. Optionally, the device first excludes data packets that are not suitable for extended identity identification options, such as DNS, BGP, DHCP and other protocol data packets.
[0027]A1. Match user identity based on IP source address: The device looks up the user identity and its private key mapped to the IP address in the loc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com