Simulator-based android application server side Web vulnerability detection method
A technology of vulnerability detection and application services, applied in the direction of electrical components, transmission systems, etc., can solve problems such as time-consuming and labor-intensive, high reverse difficulty, waste of detection resources, etc., to achieve the effect of avoiding processing methods, low cost, and easy to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
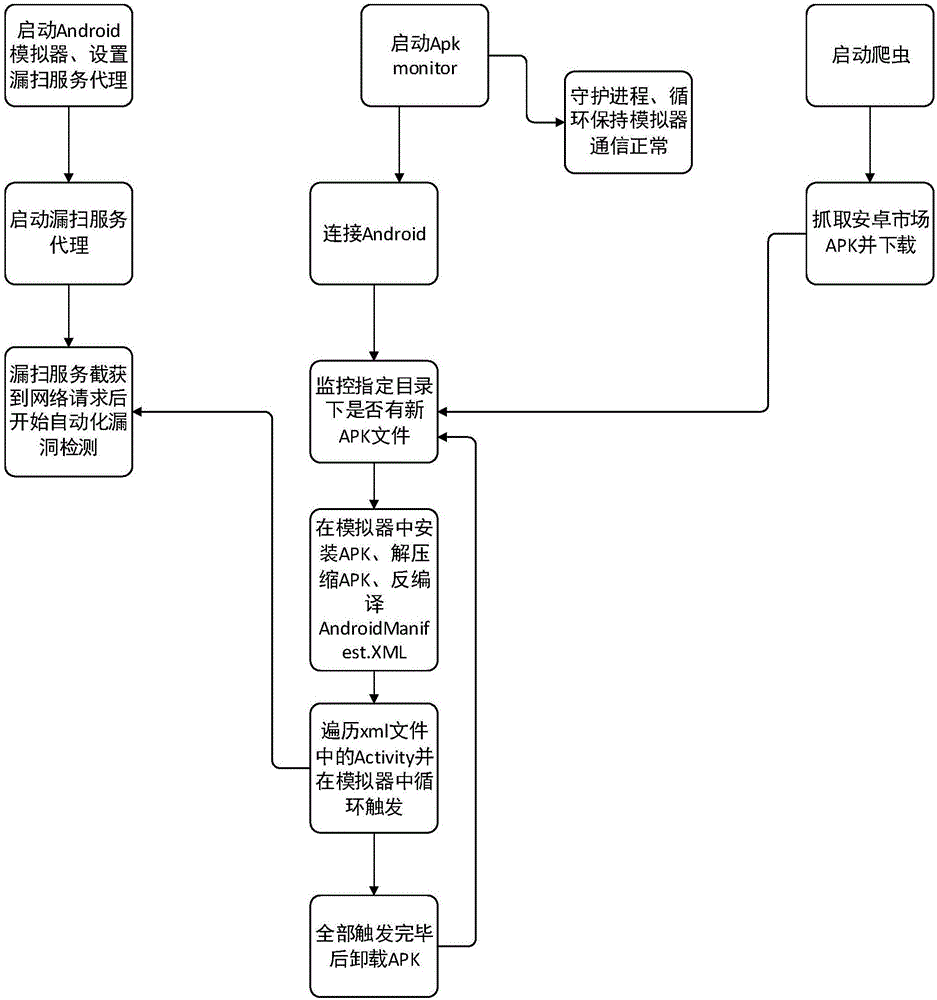
[0028] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. like figure 1 As shown, the processing flow includes: 1) start the vulnerability detection agent module, start the Android emulator and configure the network; 2) write the APK Monitor module, connect the Android emulator and monitor the directory, and the APK Monitor module uses a Python script to specify the directory Monitor new files; 3) Download batch or individual Android application installation files, ie APK files, to a specified directory through a Python script; 4) APK Monitor monitors the APK files in the directory, automatically installs them through the ADB command, and traverses Trigger the Activity of the APP to execute the functions of the APP; 5) Capture all the requests of the APP to the server through the agent of the vulnerability detection agent module; 6) The vulnerability detection agent module performs vulnerabili...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com