Detection method and detection system for SQL injection attack
A technology of injection attack and detection method, applied in the field of information security, it can solve the problems of website security threats, inability to know website SQL injection attack vulnerabilities, weak sense of product value, etc., and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
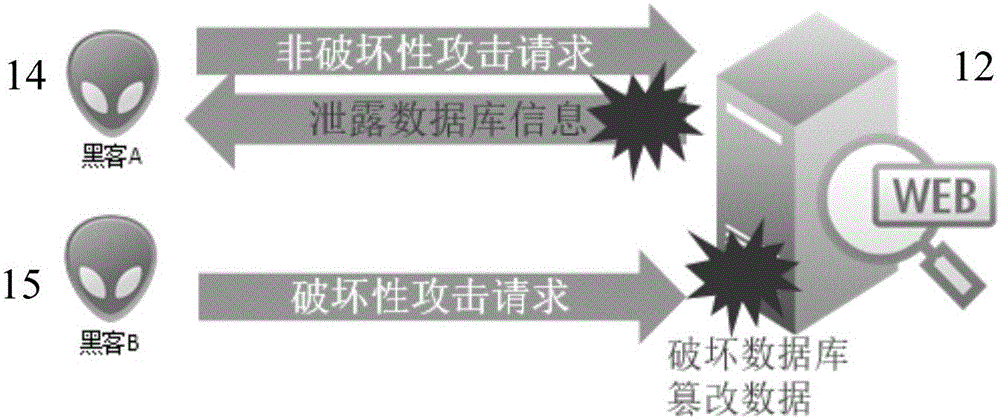
[0022] In order to reduce the false alarm rate and false negative rate of SQL injection attack detection, the present invention provides a SQL injection attack detection method and system.
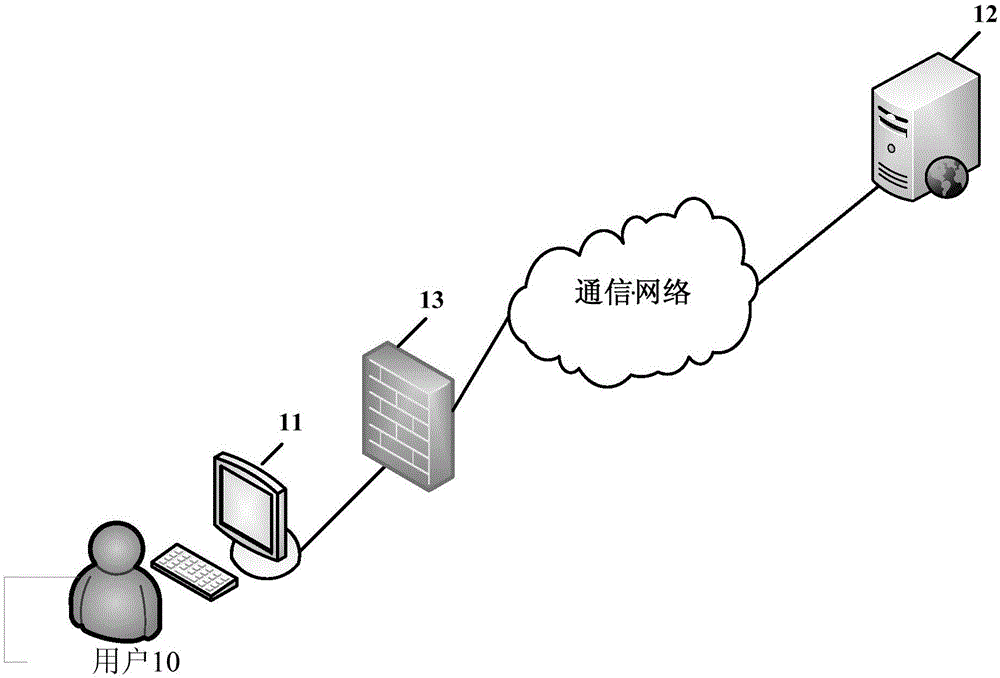
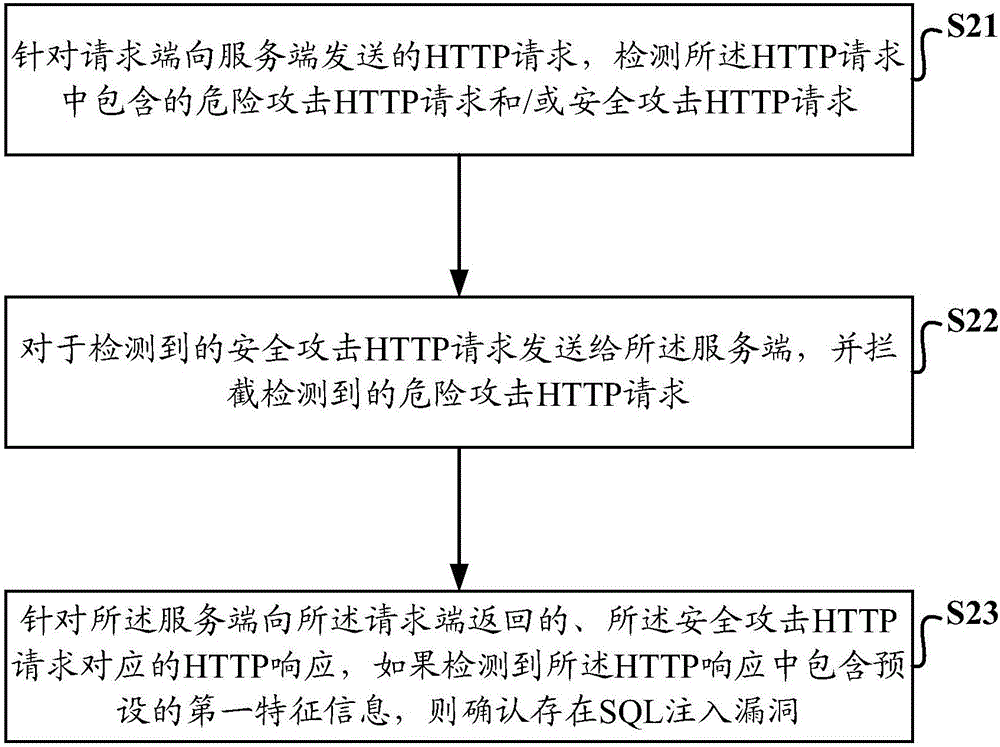
[0023] The implementation principle of the SQL injection attack detection method provided by the embodiment of the present invention is: the firewall detects the HTTP request sent by the client to the server, sends the detected security attack HTTP request to the server, and intercepts the detected dangerous attack HTTP Request, for the HTTP response corresponding to the security attack HTTP request returned by the server to the requesting end, if it is detected that the HTTP response contains the preset first characteristic information, then it is confirmed that there is a SQL injection vulnerability. The above-mentioned SQL injection attack detection method Allow some HTTP requests containing security attack HTTP requests to be sent to the server, and then detect whether there is a SQL in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com