Repeated short message recognition and analysis methods and system
An analysis method and short message technology, applied in the field of information security, can solve the problem of shielding the sending source and cannot shield it, and achieve the effect of efficient and accurate verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] All the features disclosed in this specification, except mutually exclusive features and / or steps, can be combined in any way.
[0034] The present invention will be described in detail below in conjunction with the accompanying drawings.
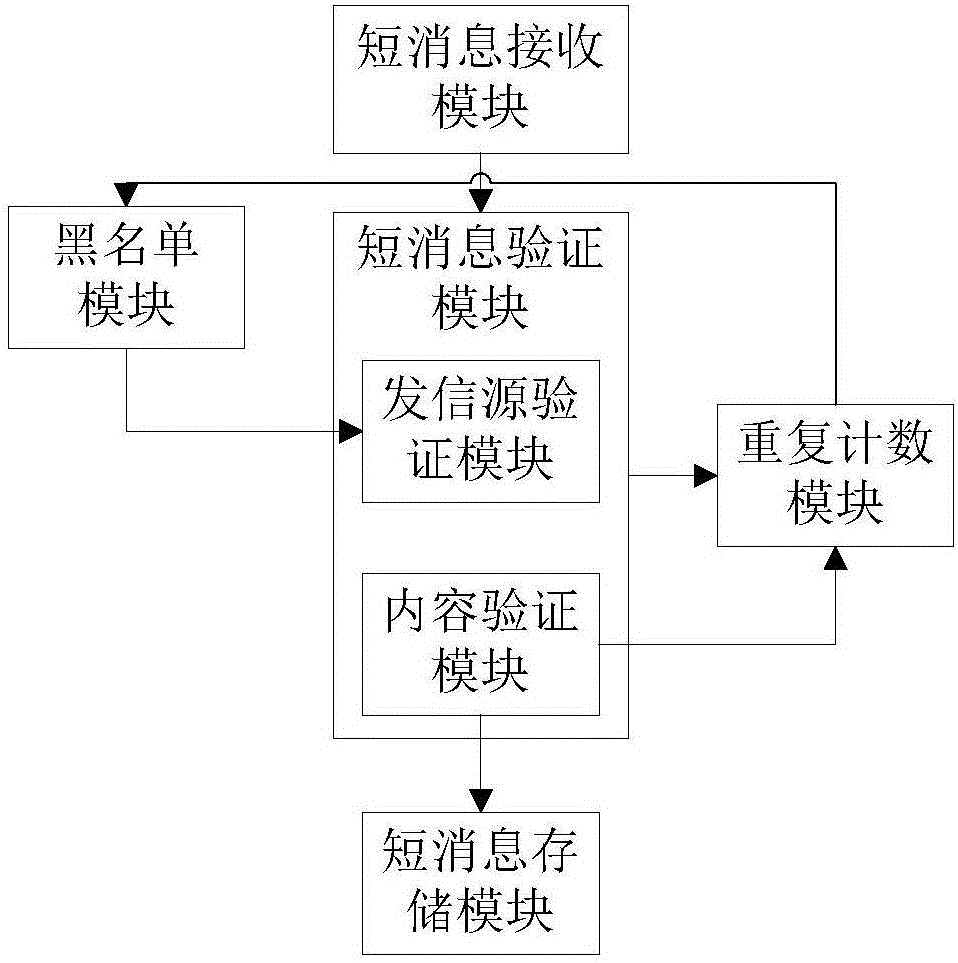
[0035] A method and system for identifying and analyzing repeated short messages, said system comprising:
[0036] Short message receiving module: used to receive and cache short messages sent to users by operators, and send the short messages in the cache to the short message verification module for verification;
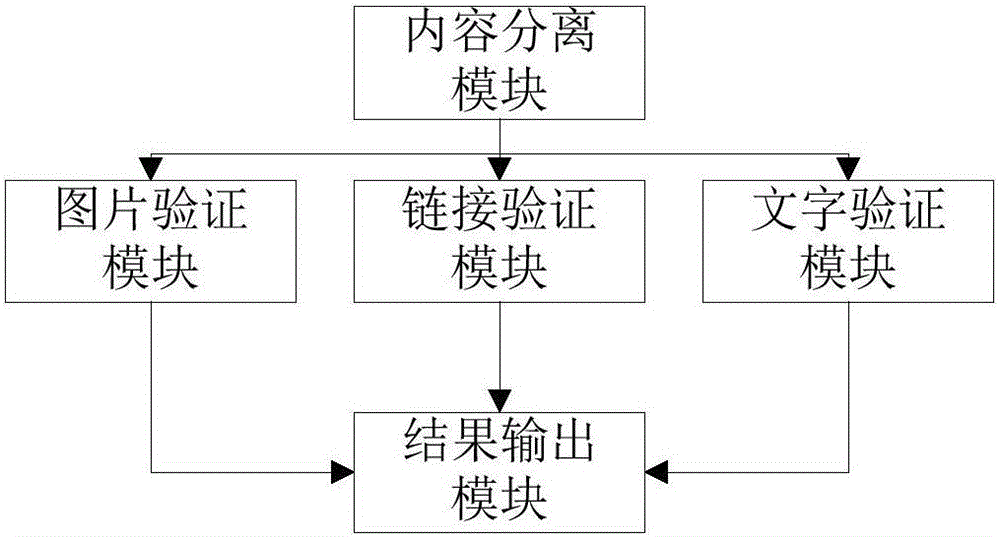
[0037] Short message verification module: includes a sending source verification module and a content verification module. The sending source verification module first compares the sending source of the short message with the list of repeated sending sources stored in the blacklist module, and if not determined as non-repeating The source of the letter, and then verify the content of the short message through the content...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com