Goods purchase and authentication method
A technology for commodities and buyers, applied in the field of shopping, can solve problems such as safety issues, and achieve the effect of saving intermediate links in logistics, saving store storage costs, and improving consumer experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0101] figure 1 The flow of the method for commodity purchase and authentication according to the first embodiment of the present invention is shown. details as follows:
[0102] A method for commodity purchase and authentication, the commodity is fixed with an RFID tag, the RFID tag carries the RFID information of the commodity, and the corresponding relationship between the RFID information of the sample of the commodity and the category of the commodity is preset in the server; and the sample of the commodity Corresponding relationship with actual commodity items to be sold; the method includes the following steps:
[0103] Step 101: The terminal scans the RFID information of the sample of the product, and sends the RFID information of the sample and the purchased quantity to the server;
[0104] Step 102: The server queries the corresponding relationship according to the RFID information of the sample, obtains the commodity category corresponding to the sample, and ships...
no. 2 example
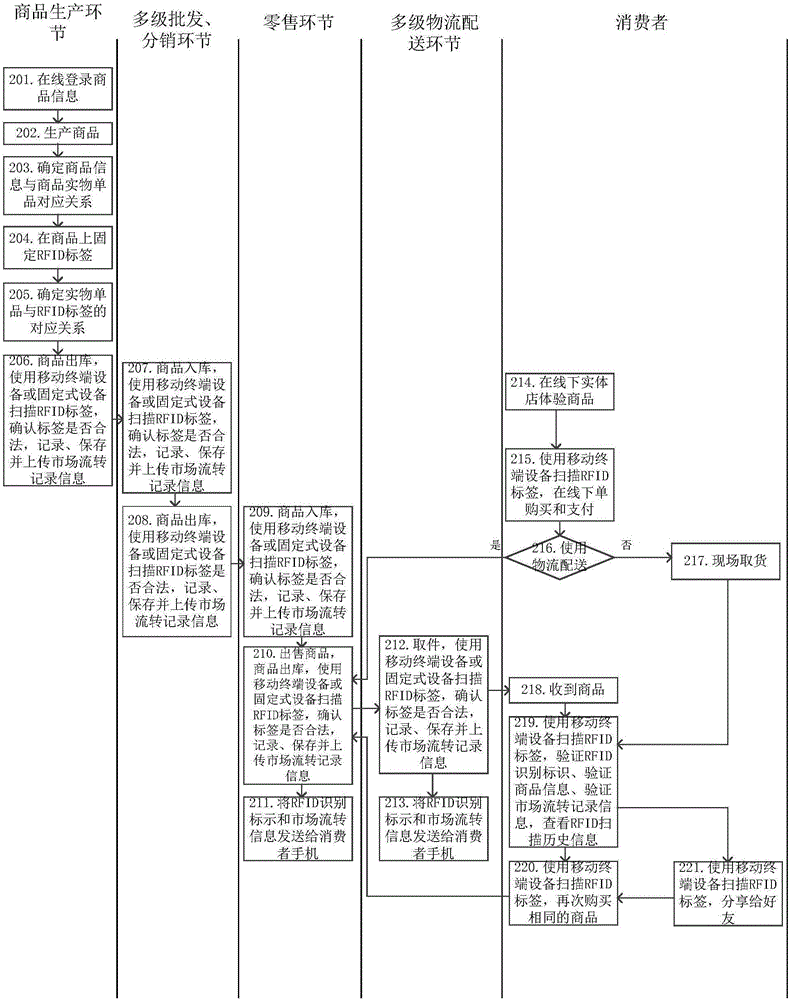
[0121] figure 2 Shown is the method flow of commodity purchase and authentication according to the second embodiment of the present invention. In this embodiment, the commodity has an RFID tag since it leaves the factory, as follows:
[0122] Step 201: Register product information online, and go to step 202.
[0123] Step 202: produce goods, go to step 203.
[0124] Step 203: Determine the corresponding relationship between the product information and the actual product, and proceed to step 204.
[0125] Step 204: Fix the RFID tag on the commodity, go to step 205.
[0126] Step 205: Determine the correspondence between the physical item and the RFID tag, and proceed to step 206.
[0127] Step 206: Commodities are out of the warehouse, use mobile terminal equipment or fixed equipment to scan RFID tags, confirm whether the tags are legal, record, save and upload market circulation information records, and enter step 207.
[0128] It should be noted that, in this embodiment,...
no. 3 example
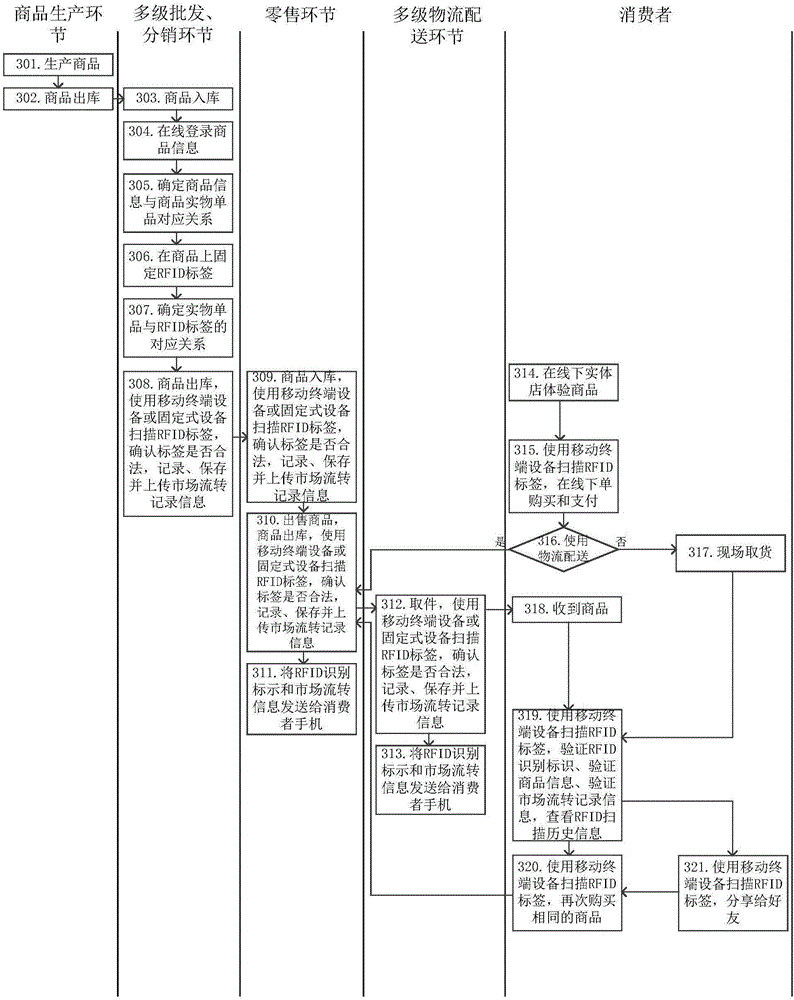
[0149] image 3 Shows the flow of the method for commodity purchase and authentication according to the third embodiment of the present invention. In this embodiment, the commodity does not have an RFID tag when it leaves the factory, but the RFID tag is fixed on the commodity during the wholesale distribution link ,details as follows:
[0150] Step 301: produce goods, go to step 302.
[0151] Step 302: Commodity out of warehouse, go to step 303.
[0152] It should be noted that, in this embodiment, the above-mentioned steps 301-302 are all performed by the product production link.
[0153] Step 303: Commodity storage, go to step 304.
[0154] Step 304: Online registration of commodity information, go to step 305.
[0155] Step 305: Determine the corresponding relationship between commodity information and commodity physical items, and proceed to step 306.
[0156] Step 306: Fix the RFID tag on the commodity, go to step 307.
[0157] Step 307: Determine the correspondenc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com