Isolation method based on fingerprint recognition of computer input and output devices
A technology for input and output devices and fingerprint identification, which is applied in the protection of internal/peripheral computer components, digital data authentication, etc., and can solve problems such as poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
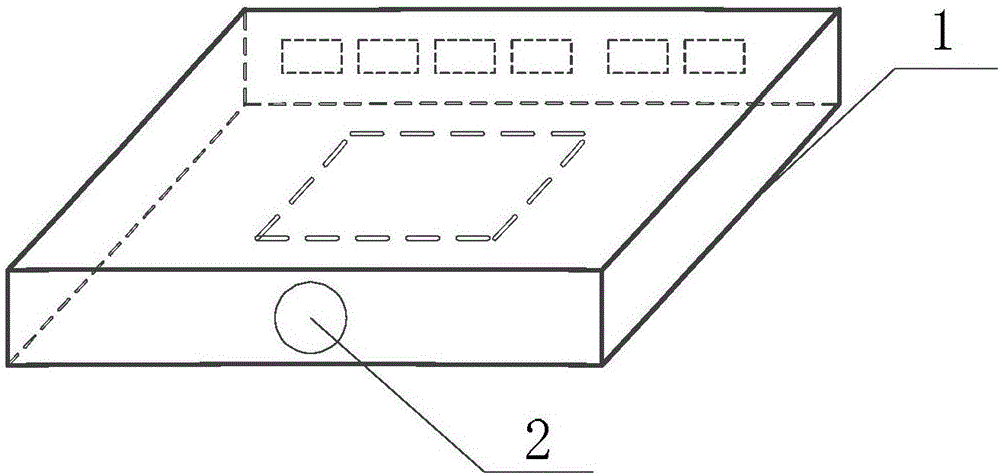
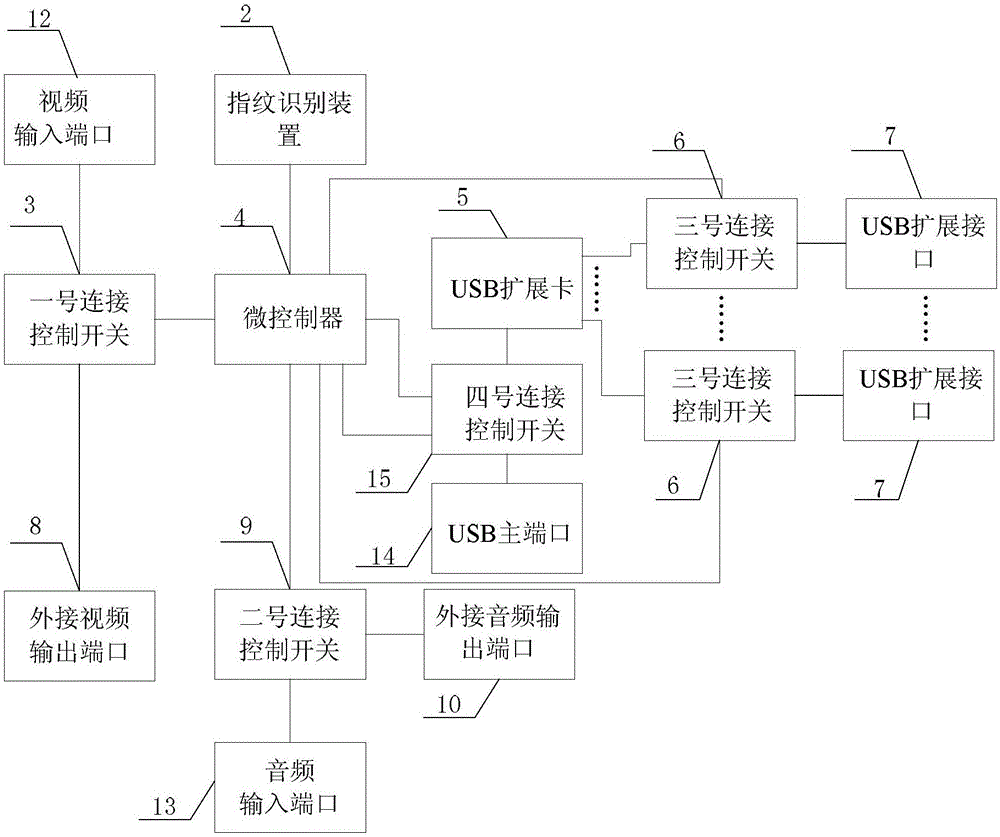
[0022] Specific implementation mode 1. Combination figure 1 and 2 Describe this embodiment, the computer input and output equipment isolation method based on fingerprint identification described in this embodiment, the method is realized by the computer input and output equipment isolation device based on fingerprint identification, the device includes a housing 1, a fingerprint identification device 2, a number one Connection control switch 3, microcontroller 4, USB expansion card 5, n number three connection control switches 6, n USB expansion interfaces 7, external video output port 8, second connection control switch 9, external audio output port 10 and No. 4 connection control switch 15;
[0023] The fingerprint identification device 2, n USB extension interfaces 7, external video output port 8 and external audio output port 10 are all embedded in the side of the housing 1, and the video input port 12, USB main port 14 and audio input port 13 are also embedded. On the c...
specific Embodiment approach 2
[0037] Specific Embodiment 2. This embodiment is a further description of the method for isolating computer input and output devices based on fingerprint identification described in Specific Embodiment 1. No. 1 connection control switch 3, n No. 3 connection control switches 6 and No. 2 connection The control switches 9 are all single-pole single-throw switches.
specific Embodiment approach 3
[0038] Specific Embodiment 3. The difference between this embodiment and the method for isolating computer input and output devices based on fingerprint identification described in Specific Embodiment 1 is that it uses an NFC card reader or an RFID card reader instead of the fingerprint identification device 2, and the NFC The card reader or the RFID card reader is used to identify the NFC card or the RFID card, and the signal output end of the NFC card reader or the RFID card reader is connected to the card identification signal input end of the microcontroller 4 .
[0039] When the USB device is connected to the host computer through the device, the microcontroller 4 of the device connects the USB device to the microcontroller 4 of the device through the USB expansion card 5, the third connection control switch 6 and the fourth connection control switch 15 USB interface, the microcontroller 4 loads the USB device driver, reads the UUID (Universally Unique Identifier, Universa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com