A control flow hijacking attack detection method and system based on dynamic analysis
A technology for attack detection and control flow, applied in error detection/correction, software testing/debugging, instrumentation, etc., can solve problems such as low efficiency, low precision, and difficult deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] In the present invention, it is used to detect control flow hijacking attacks, and the present invention will be further described below in conjunction with the accompanying drawings. The present invention aims to provide a control flow hijacking attack system based on dynamic analysis, which can detect control flow hijacking attacks simply and efficiently, and can be easily deployed in the actual application environment to defend against control flow hijacking attacks in the actual application environment .
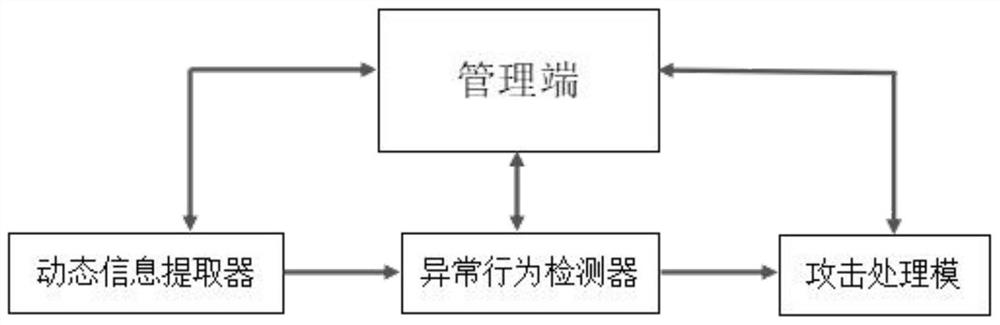
[0015] figure 1 It is an architecture diagram describing the composition of the system of the present invention.
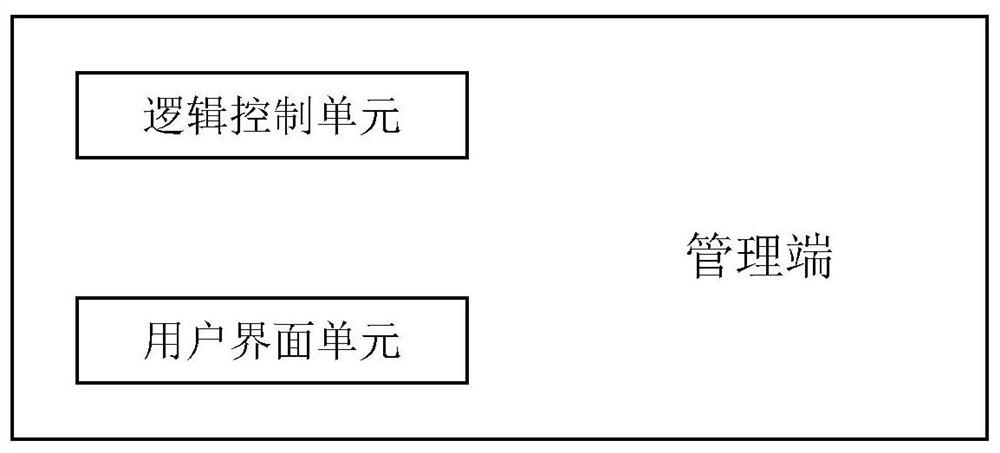
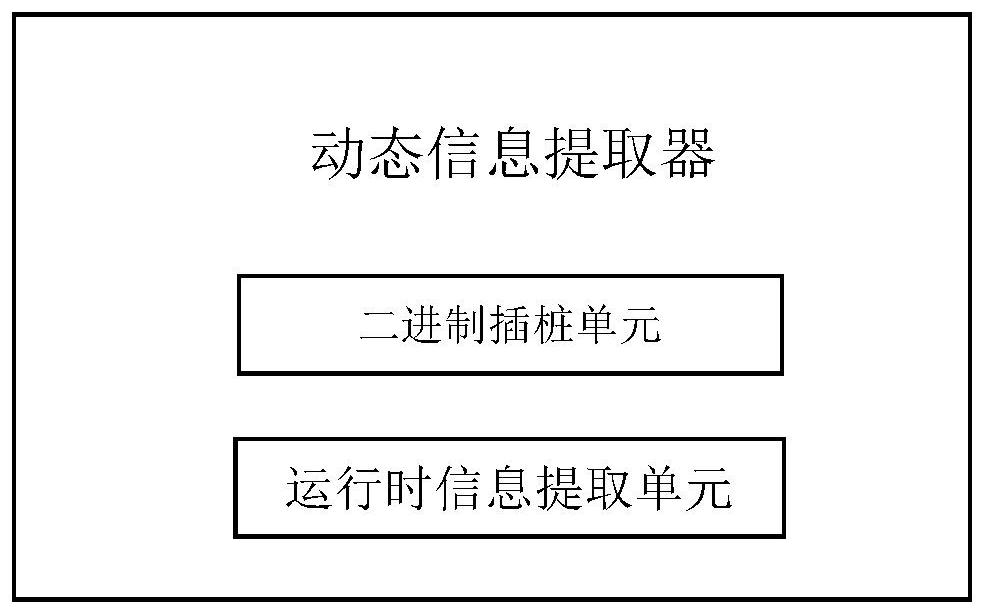
[0016] Such as figure 1 As shown, the core of the detection system is the management terminal, which integrates other modules so that the functions of the entire system are harmoniously connected. At the same time, a user interaction interface is provided through which the user can start the target program and input the detected samples or data. , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com