Tag reader and database three-way authentication system and method
A tag reader and authentication method technology, applied in digital data authentication, other database retrieval, other database query, etc., can solve problems such as restricting the growth of the radio frequency identification industry, and achieve the effect of avoiding leakage and ensuring normal communication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
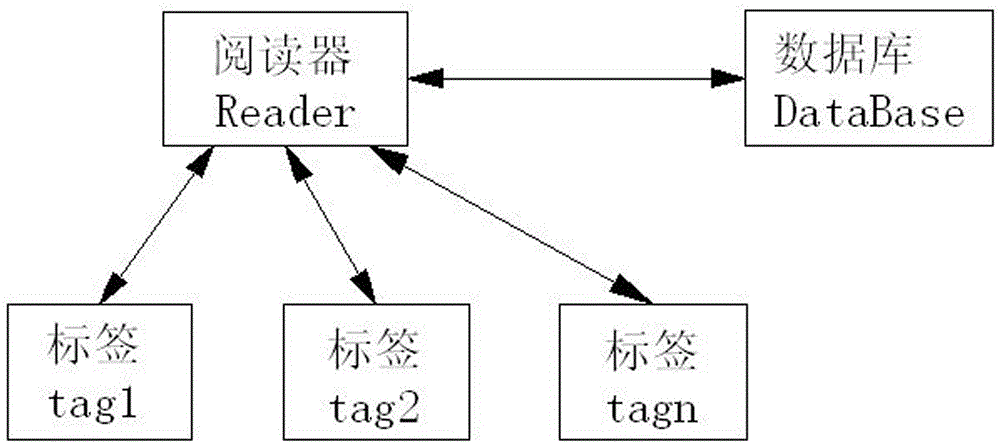
[0054] A three-way authentication system for a tag reader and a database. The application authentication system can quickly and accurately realize the three-way authentication between the reader, the tag, and the database, thereby ensuring the normal communication between the three, such as figure 1 As shown, the following setting method is specially adopted: a reader, a tag and a database are set, the database is connected to the reader, and the reader is connected to the tag.
[0055] When it is in use, connect the reader to the database DataBase through the data transmission link, so as to perform data interaction between the two; at the same time, use wired or wireless to connect the tag and the reader to realize the connection between the two For the data interaction among them, there are preferably i tags, satisfying i=1, 2, 3...n.
Embodiment 2
[0057] This embodiment is further optimized on the basis of the above embodiments. In order to better realize the authentication system of the present invention, the data communication between the tag and the reader can be carried out in a wired or wireless communication mode, such as figure 1 As shown, the following setting method is adopted in particular: the tag is connected to the reader in a wired or wireless manner.
Embodiment 3
[0059] This embodiment is further optimized on the basis of any of the above embodiments, further to better realize the authentication system of the present invention, such as figure 1 As shown, the following setting method is adopted in particular: a reserved storage area, an EPC storage area, a TID storage area and a user storage area for storing different data are set in the tag;
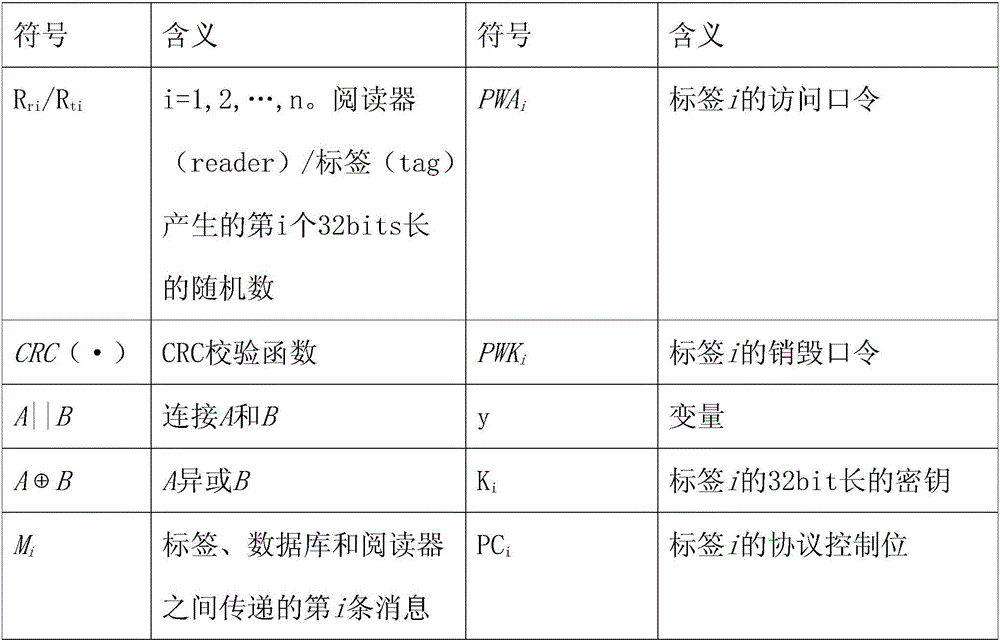
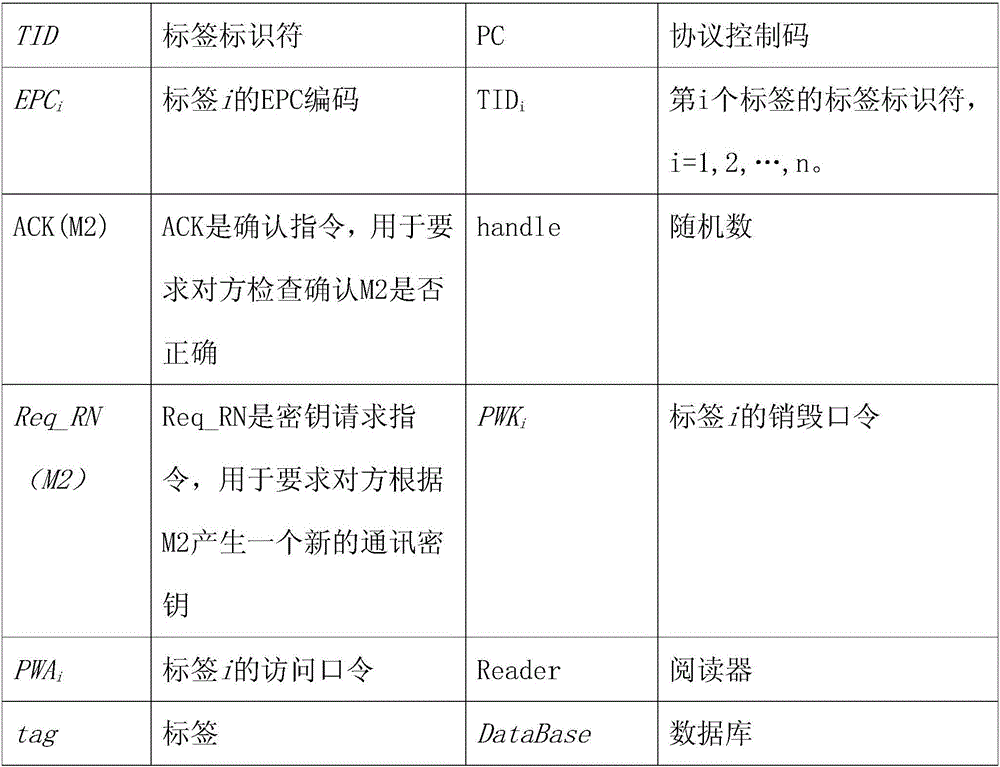
[0060] The reserved storage area stores a 32bit access password (access password) PWA i And 32bit destruction password (kill password) PWK i ;
[0061] The EPC storage area stores 32bit EPC, 16bit protocol control code (PC), EPC and PC value cyclic redundancy check code;
[0062] The TID (tag identifier) storage area stores the TID of the 32bit identification number information of the electronic tag (tag) i , all additional information of 32bit; when used, it is the same as that stipulated in the EPC C1G2 agreement;
[0063] The user storage area stores other information of user products, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com