Data protection method for mobile terminal and mobile terminal
A mobile terminal, data protection technology, applied in the direction of digital data protection, digital data authentication, electronic digital data processing, etc., can solve problems such as the inability to guarantee personal data security, and achieve the effect of improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
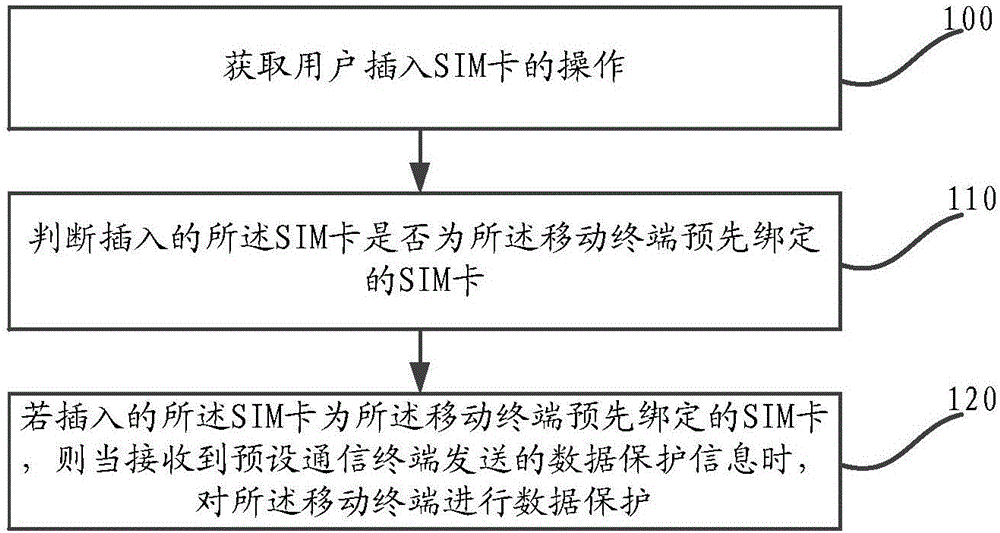
[0023] This embodiment provides a data protection method for a mobile terminal, such as figure 1 As shown, the method includes: step 100 to step 120.
[0024] Step 100, acquiring the operation of inserting the SIM card by the user.
[0025] After the data protection function is set on the mobile terminal, when the mobile terminal is turned on or powered on, or the screen is unlocked, the operation of inserting the SIM card will be detected in real time. During specific implementation, the user's operation of inserting the SIM card in the mobile terminal can be acquired by calling the interface of the system or registering a system event.
[0026] Step 110, judging whether the inserted SIM card is a pre-bound SIM card for the mobile terminal.
[0027] After acquiring the operation of inserting the SIM card in the mobile terminal, first acquire the card number of the SIM card inserted in the operation of inserting the SIM card. Then, match the obtained card number with the pr...
Embodiment 2
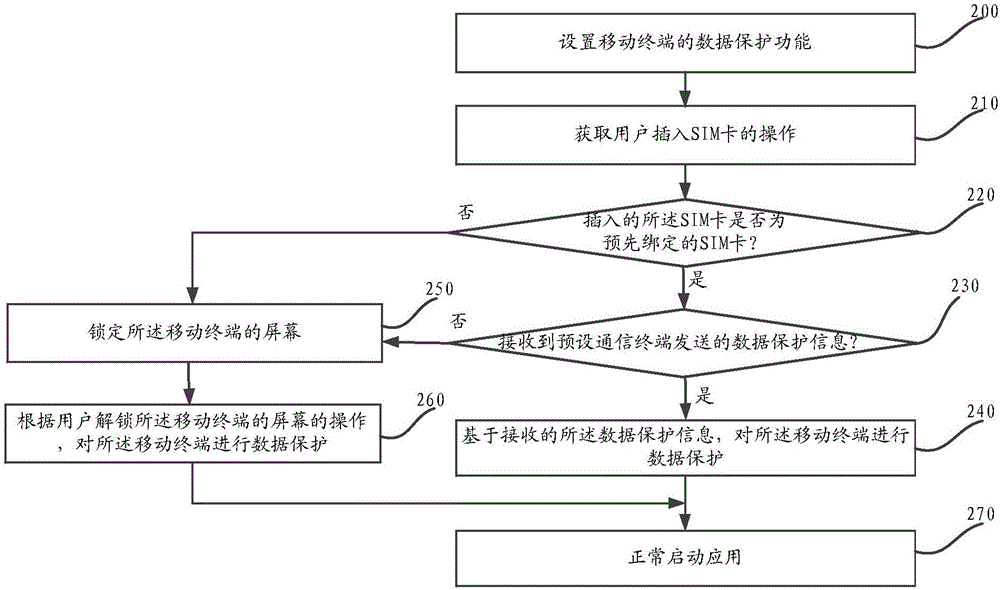
[0035] This embodiment provides a data protection method for a mobile terminal, such as figure 2 As shown, the method includes: Step 200 to Step 270.
[0036] Step 200, setting the data protection function of the mobile terminal.
[0037] During specific implementation, the data protection function of the mobile terminal can be set through the setting interface of the mobile terminal. Setting the data protection function of the mobile terminal includes: setting the SIM card number bound to the mobile terminal, and setting the information of the communication terminal used to send data protection information; storing the binding information generated according to the SIM card number and the communication Terminal information. During specific implementation, firstly, the data protection function for the mobile terminal is enabled. An interactive menu may be provided through a preset human-computer interaction interface for the user to choose to enable or disable the data pro...
Embodiment 3
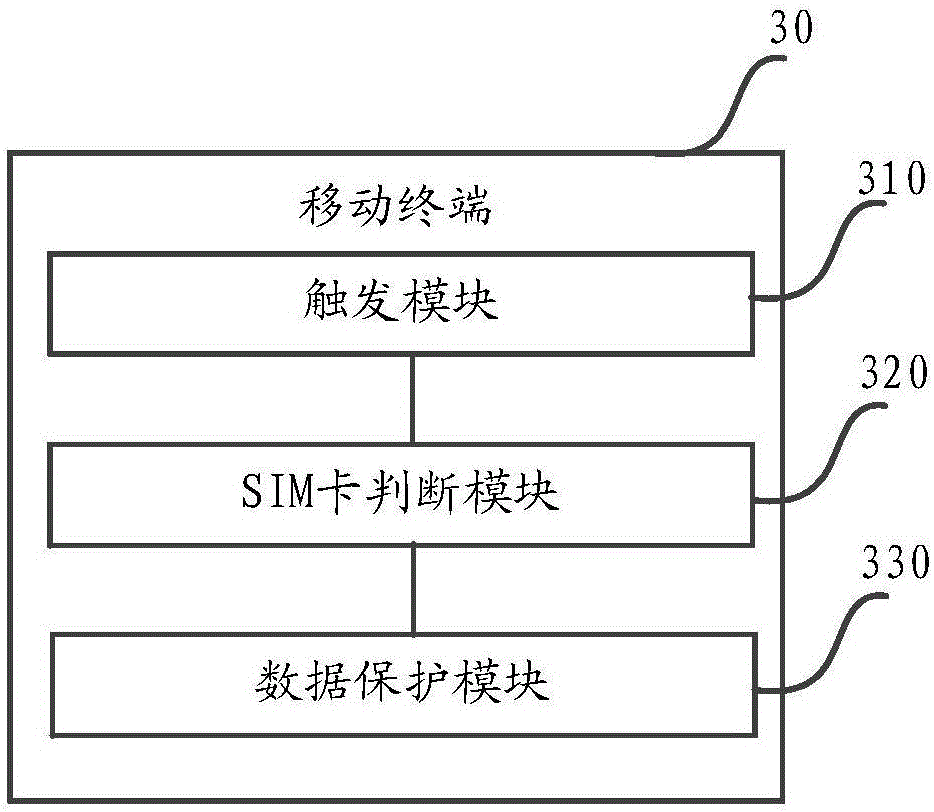
[0062] refer to image 3 Correspondingly, the embodiment of the present invention also discloses a mobile terminal 30 . The mobile terminal 30 includes:
[0063] The trigger module 310 is used to obtain the operation of inserting the SIM card by the user;
[0064] A SIM card judging module 320, configured to judge whether the inserted SIM card obtained by the triggering module 310 is a pre-bound SIM card of the mobile terminal;
[0065] The data protection module 330 is configured to perform data protection on the mobile terminal when receiving the data protection information sent by the preset communication terminal if the inserted SIM card is the SIM card pre-bound to the mobile terminal, Wherein, the data protection information includes a preset keyword for instructing data protection.
[0066] The mobile terminal disclosed in the embodiment of the present invention judges whether the inserted SIM card is the pre-bound SIM card of the mobile terminal by obtaining the ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com