Data desensitization method, device and system
A data desensitization and desensitization technology, applied in the field of data processing, can solve the problems of loss of readability, insufficient consideration of data encryption and fuzzification, and leakage of core data, so as to prevent leakage and ensure maximum readability. security, and the effect of ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
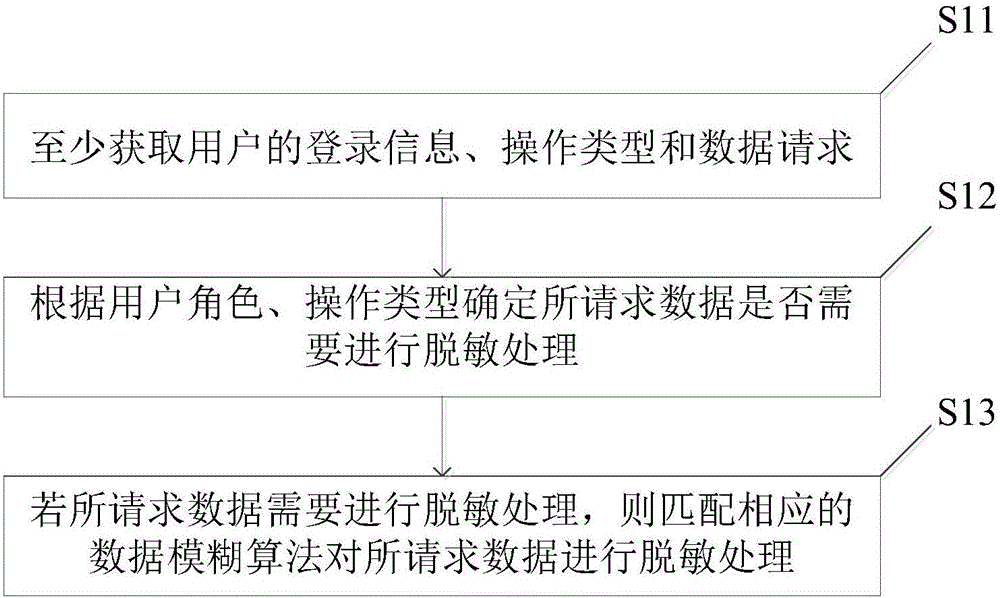
[0036] Such as figure 1 As shown, the embodiment of the present invention provides a data desensitization method, including the following steps:
[0037] S11. Obtain at least user role, operation type and data request.
[0038] In the embodiment of the present invention, the user's login information is associated with the user role, so the user role can be determined according to the login information input by the user on the operation terminal.
[0039] The operation types in the embodiment of the present invention include at least business processing, batch query and export
[0040] S12. Determine whether the requested data needs to be desensitized according to the user role and operation type.
[0041] As a possible implementation of determining whether data needs to be desensitized in the embodiment of the present invention, determine its authority in the selected operation type according to the user role, determine the sensitivity level of the requested data according t...
Embodiment 2
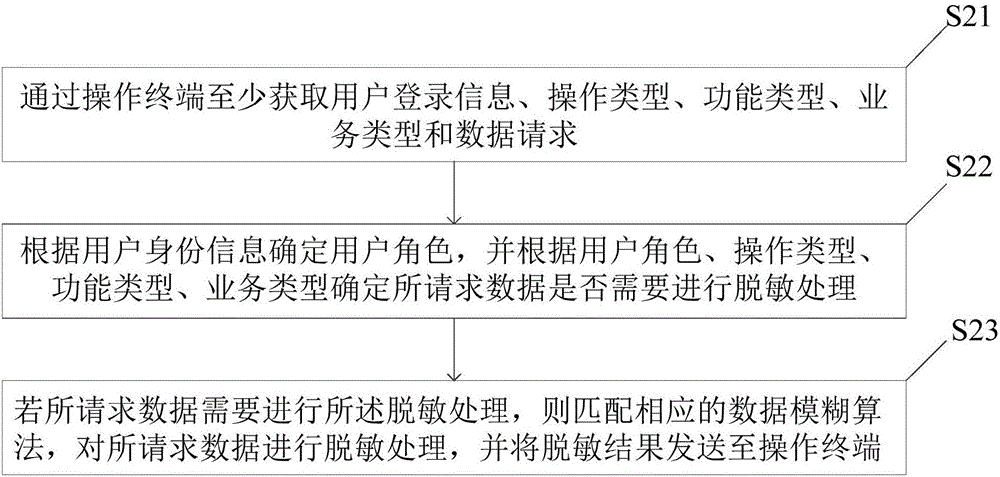
[0054] Such as figure 2 As shown, the embodiment of the present invention provides a data desensitization method, including the following steps:
[0055] S21. Obtain at least user login information, operation type, function type, service type and data request through the operation terminal.
[0056] In the embodiment of the present invention, the user's login information is associated with the user role, so the user role can be determined according to the login information input by the user on the operation terminal.
[0057] The operation types in the embodiment of the present invention at least include business processing, batch query and export. Function types include at least business processing, batch query and export.
[0058] It should be noted that the operation type is at the application level, which can be expanded according to the actual usage scenario, and the use of the operation type usually needs to be implemented with the help of the function type. For examp...
Embodiment 3
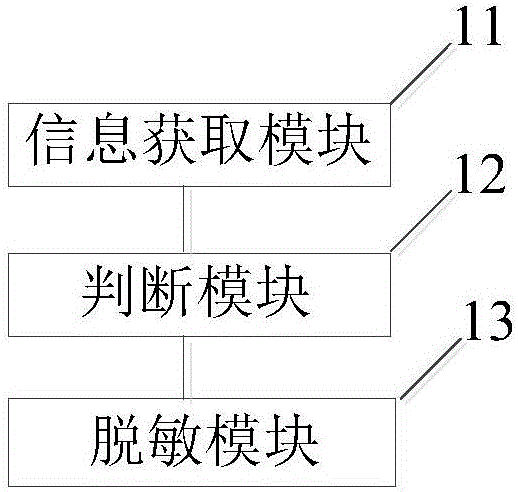
[0067] Such as image 3 As shown, the embodiment of the present invention provides a data desensitization device, including an information acquisition module 11, a judgment module 12 and a desensitization module 13, and the information acquisition module 11 is used to at least acquire the user's login information, operation type and data request; The judging module 12 is used to determine whether the requested data needs to be desensitized according to the user role and operation type; the desensitization module 13 is used to match the corresponding data fuzzy algorithm to desensitize the requested data when the requested data needs to be desensitized. Sensitive handling.
[0068] The embodiment of the present invention combines data desensitization with system function architecture, completes the planning of desensitization scheme synchronously when planning product functions, and sets corresponding desensitization methods. The design of the desensitization method fully cons...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com