Pseudo base station protection method and device
A technology of protective device and pseudo base station, which is applied in the field of communication, can solve the problem of low security and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
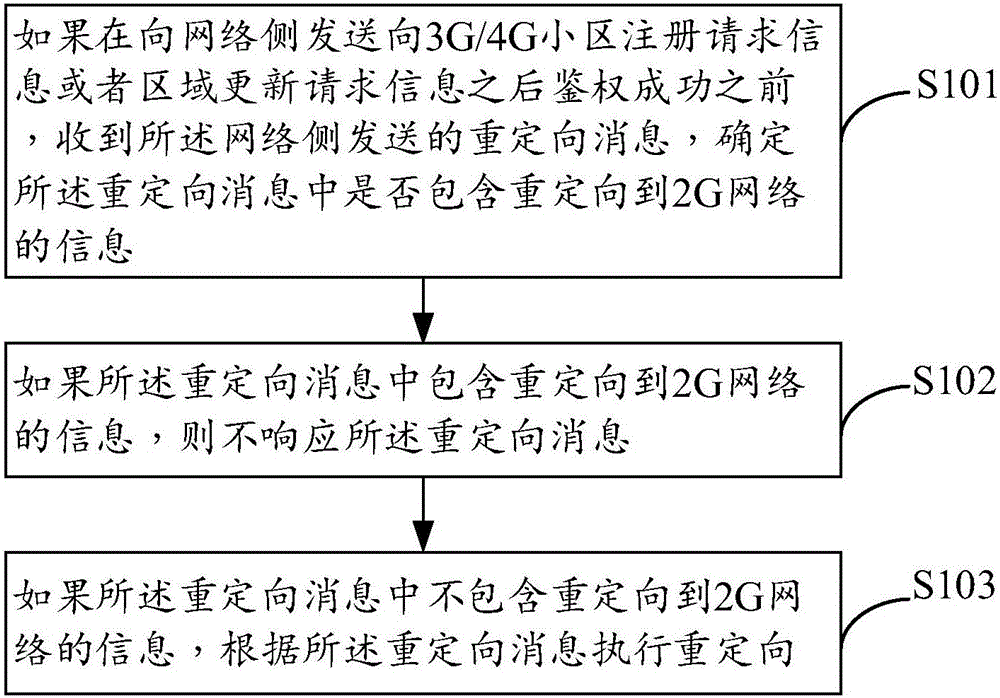
[0040] figure 1 It is a schematic flow chart of a method for protecting a false base station provided in Embodiment 1 of the present invention. The method is applied to a terminal, and the terminal may be a device such as a mobile phone or a tablet. Such as figure 1 As shown, the false base station protection method may include the following steps:
[0041] S101: If the redirection message sent by the network side is received before the authentication is successful after sending the registration request information to the 3G / 4G cell or the area update request information to the network side, determine whether the redirection message includes a redirection message to 2G network information.
[0042] When the terminal first accesses the network, or when the network type of the terminal changes, it will send a registration request message to the network side. When the terminal enters another location area from one location area, it will send an area update request message to ...
Embodiment 2
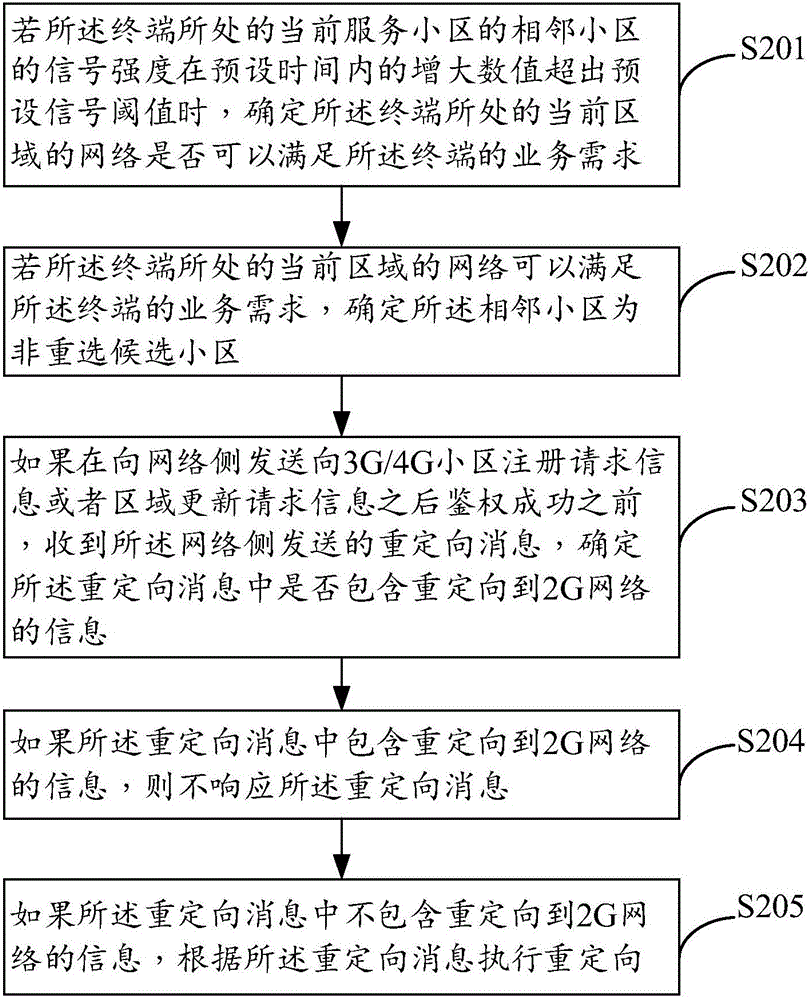
[0049] figure 2 It is a schematic flow chart of a method for protecting a false base station provided in Embodiment 2 of the present invention. The method is applied to a terminal, and the terminal may be a device such as a mobile phone or a tablet. Such as figure 2 As shown, the false base station protection method may include the following steps:
[0050] S201: If the increase value of the signal strength of the adjacent cell of the current serving cell where the terminal is located exceeds the preset signal threshold within a preset time, determine whether the network in the current area where the terminal is located can meet the requirements. Describe the service requirements of the terminal.
[0051] In the idle state, the terminal will always measure the signal of the adjacent cell of the current serving cell where the terminal is located, and when the signal strength of the adjacent cell is greater than the signal strength of the current serving cell where the term...
Embodiment 3
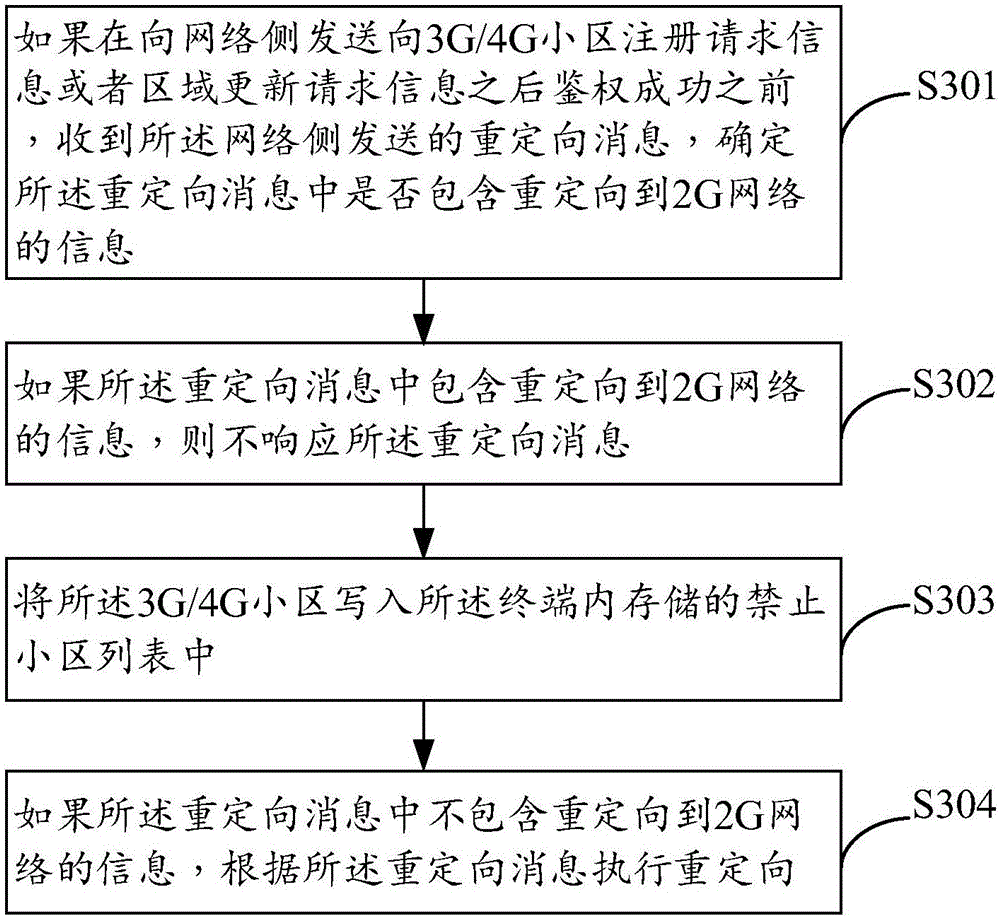
[0063] image 3 It is a schematic flow chart of a method for protecting a false base station provided in Embodiment 3 of the present invention. The method is applied to a terminal, and the terminal may be a device such as a mobile phone or a tablet. Such as image 3 As shown, the false base station protection method may include the following steps:
[0064] S301: If the redirection message sent by the network side is received before the authentication is successful after sending the registration request information to the 3G / 4G cell or the area update request information to the network side, determine whether the redirection message includes a redirection message to 2G network information.
[0065] Step S301 in this embodiment is consistent with step S101 in Embodiment 1. For details, please refer to the relevant description of Step S101 in Embodiment 1, and details are not repeated here.
[0066] S302: If the redirection message includes redirection information to the 2G ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com