A Behavioral Mode Security Protection Method Based on Lower-position Computer
A technology of safety protection and lower computer, applied in the direction of electrical testing/monitoring, etc., can solve problems such as danger, loss of function of lower computer equipment, and operation instructions that do not conform to the normal operation process, and achieve the effect of avoiding misoperation and preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
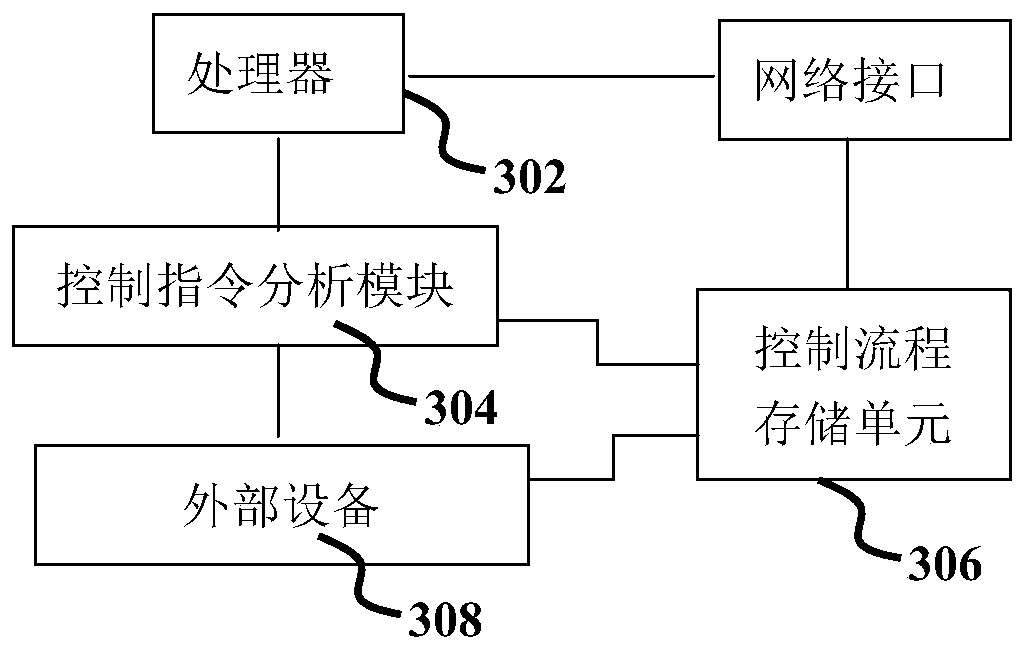
Image
Examples
Embodiment 1
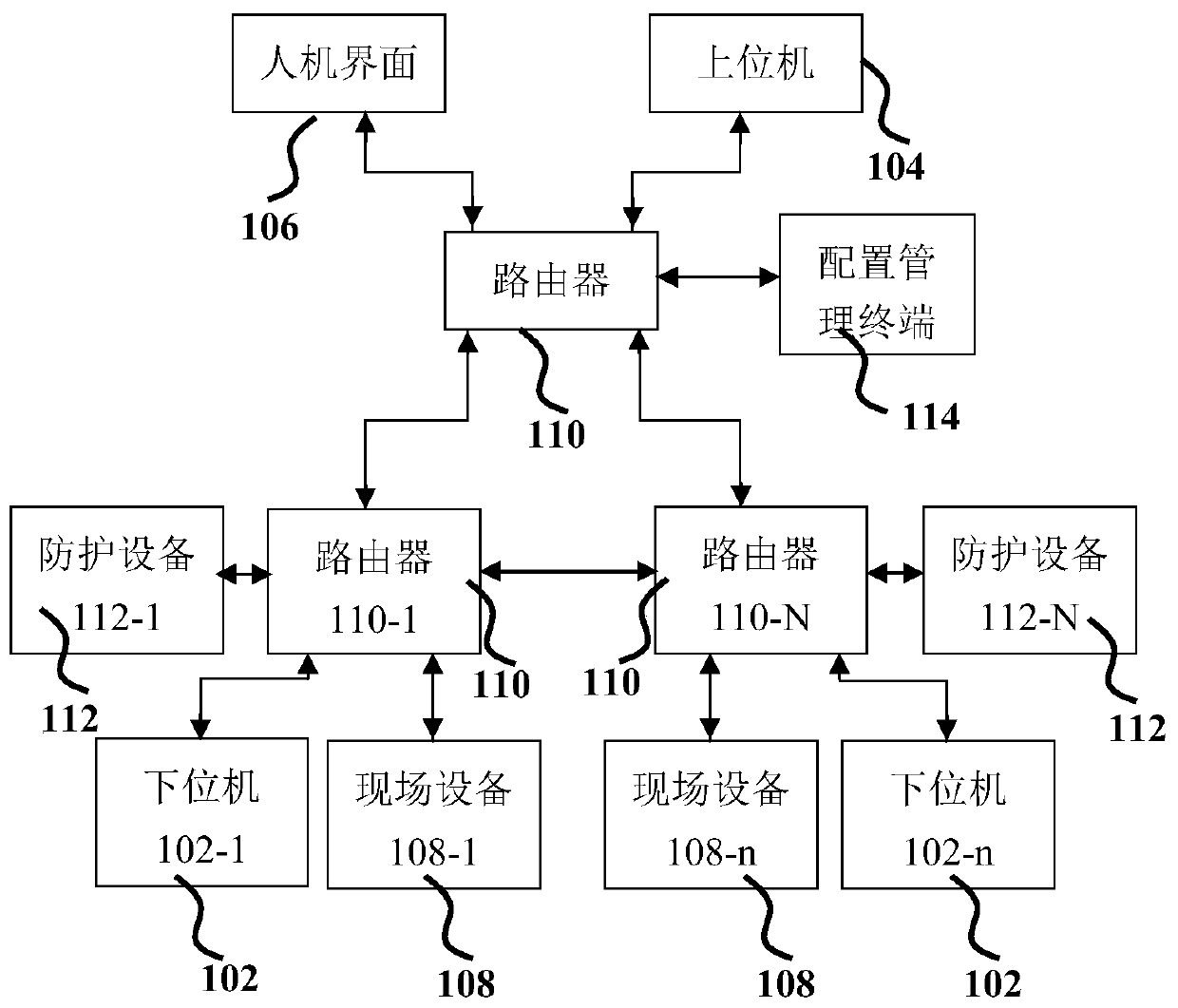
[0034] exist figure 1 It indicates that in the control system environment 100, the upper computer 104 and the lower computer 102 communicate through an industrial control protocol. There is an application program interface between the lower computer 102 and the man-machine interface 106, and the field device 108 executes control commands or feeds back measurement information through the interface with the lower computer 102, including but not limited to temperature, pressure, speed, etc., configuration management equipment 114 is used for predefining the control flow behavior mode, and sending the predefined control flow behavior mode data to each protection device 112-1 to 112-N through the interface with the protection device 112. The protective devices 112-1 to 112-N monitor the control commands sent to the field device 108 through the routers 110-1 to 110-N, that is, monitor the control commands and data sent on the communication interface, if the control commands and data...
Embodiment 2
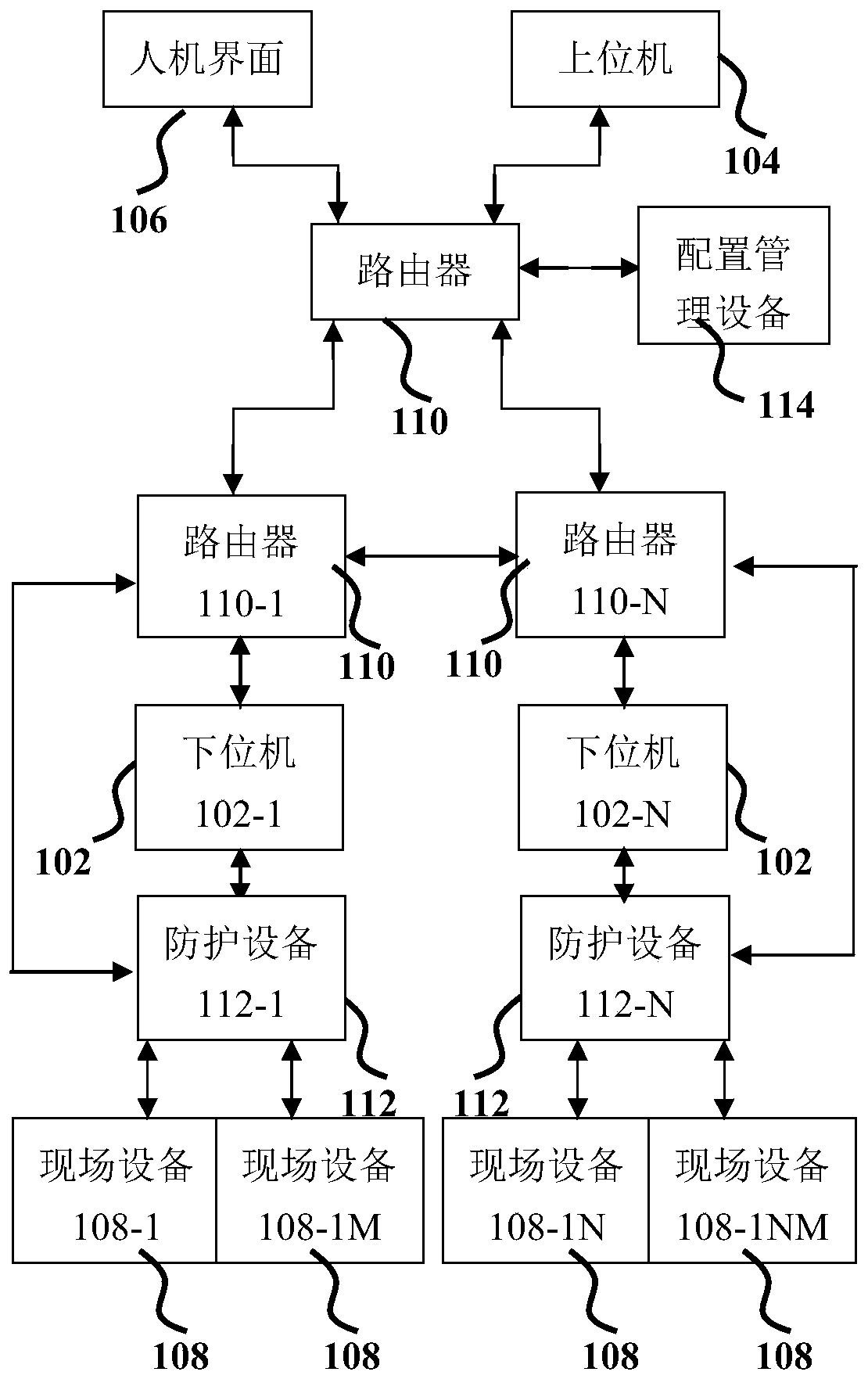
[0036] exist figure 2 Indicates that in the control system environment 100, the upper computer 104 and the lower computer 102 communicate through an industrial control protocol; there is an application program interface between the lower computer 102 and the man-machine interface 106; the protective device 112 and the lower computer 102 are provided with A communication interface that can communicate with each other; the field device 108 executes control commands or feeds back measurement information through the communication interface between the protective device 112 and the lower computer 102, including but not limited to temperature, pressure, speed, etc.; the configuration management device 114 is used to control Predefining the process behavior mode, and sending the predefined control process behavior mode data to each protection device 112-1 to 112-N through the communication interface with the protection device 112. At the same time, the communication interface is als...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com