Method of protecting encrypted control word, hardware security module, main chip and terminal
A technology of hardware security modules and control words, which is applied in the directions of secure communication devices, program/content distribution protection, internal/peripheral computer component protection, etc., can solve problems such as restricting development, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
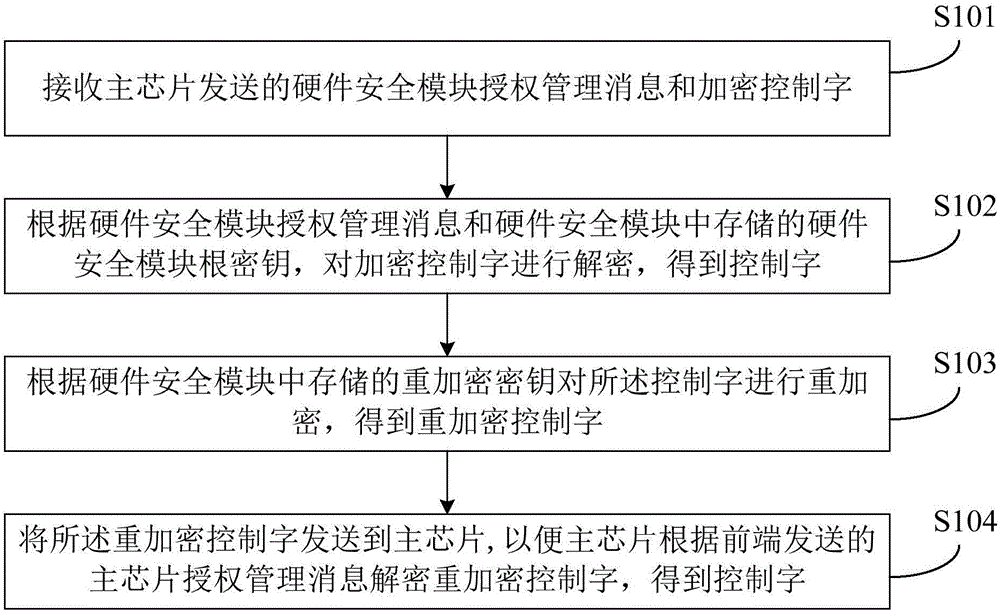
[0038] figure 1 The flow chart of the method for protecting an encrypted control word provided by Embodiment 1 of the present invention, this embodiment can be applied to a downloadable conditional access system DCAS, wherein the DCAS includes a front end and a terminal, and the terminal includes a main chip and a hardware security module. The method May be performed by the hardware security module. The method of Embodiment 1 of the present invention specifically includes:
[0039] S101. Receive a hardware security module authorization management message and an encrypted control word sent by the main chip, wherein the hardware security module authorization management message includes a key for decrypting the encrypted control word.
[0040] Wherein, the control word is used for the front-end to scramble the audio and video content subscribed by the user, such as the content of digital TV. Knowing the control word can descramble the scrambled content, so as to watch the audio ...
Embodiment 2
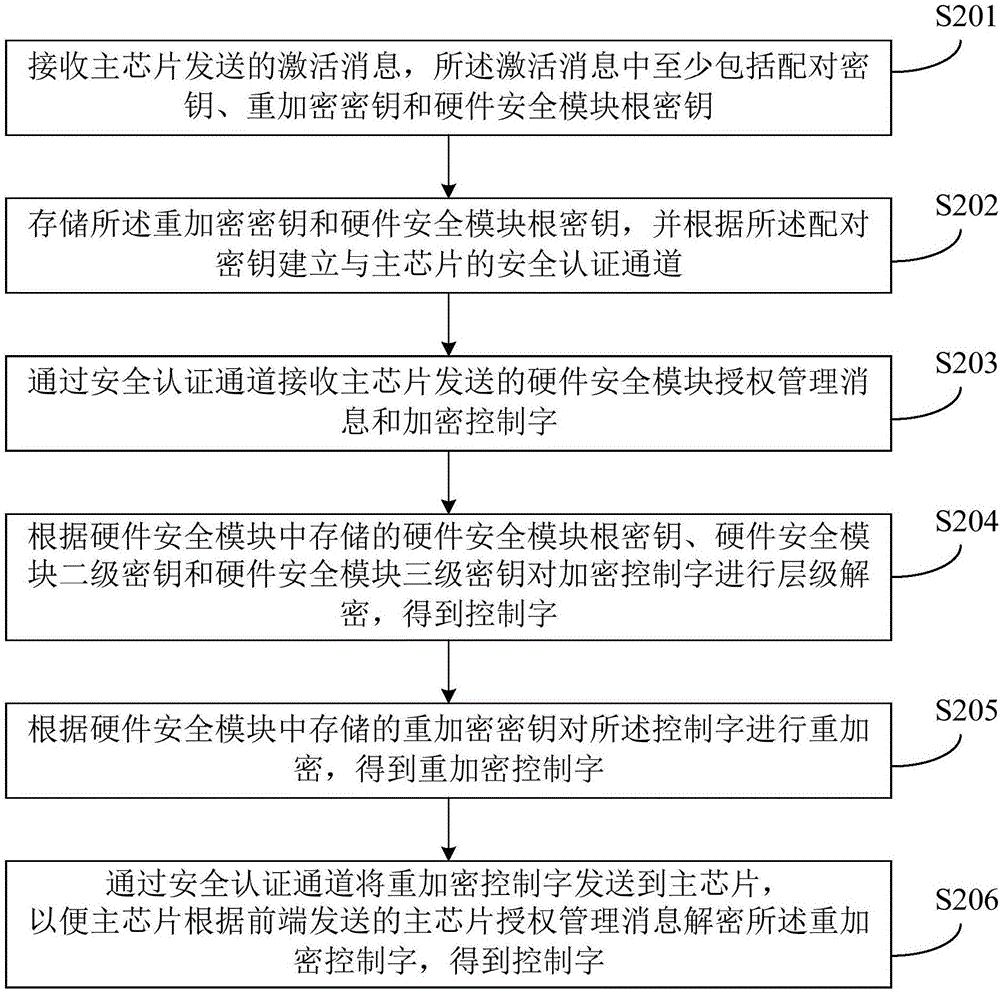
[0054] figure 2 It is a flow chart of the method provided by Embodiment 2 of the present invention. Embodiment 2 further optimizes the terminal activation operation on the basis of Embodiment 1. Such as figure 2 As shown, the method of the second embodiment of the present invention specifically includes:
[0055] S201. Receive an activation message sent by the main chip, where the activation message includes at least a pairing key, the re-encryption key, and a hardware security module root key.
[0056] The activation described here is usually performed before the terminal is used, and it can be used normally after activation. Specifically, the main chip in the terminal sends an activation request message to the front end, and then the front end sends the activation message to the main chip, and then the main chip sends the activation request message to the hardware security module. The activation message includes at least a pairing key, a re-encryption key and a hardware...
Embodiment 3
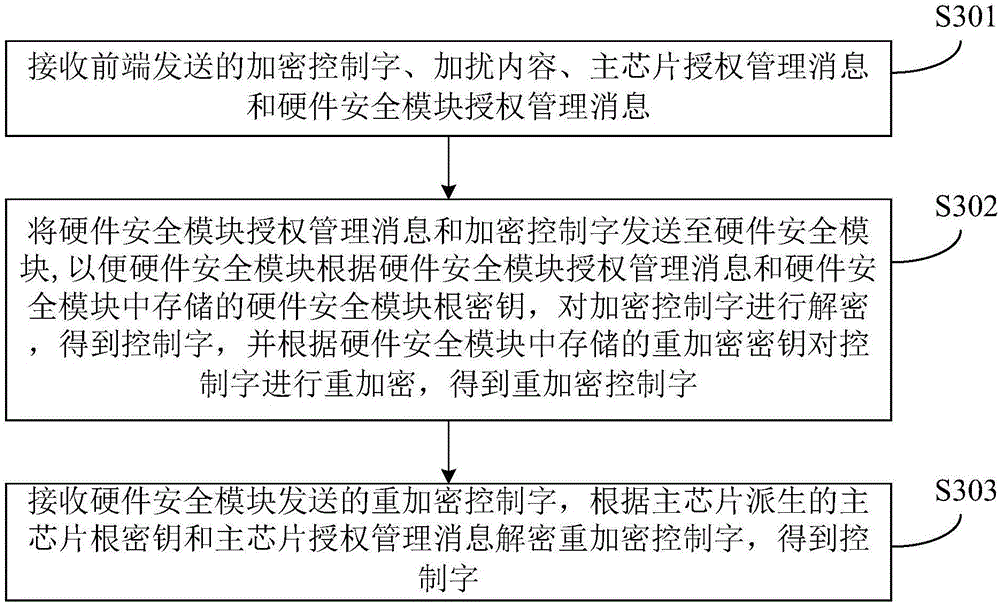
[0067] image 3 It is a flow chart of the method for protecting an encrypted control word in Embodiment 3 of the present invention. This embodiment can be applied to a downloadable conditional access system DCAS, wherein the DCAS includes a front end and a terminal, and the terminal includes a main chip and a hardware security module. The method Can be executed by the main chip. The method of the third embodiment of the present invention specifically includes:
[0068] S301. Receive the encrypted control word, scrambled content, main chip authorization management message, and hardware security module authorization management message sent by the front end.
[0069] Among them, the control word is used by the front end to scramble the audio and video content to be played. After the control word is encrypted, the terminal is authorized and sent to the main chip in the form of the main chip authorization management message and the hardware security module authorization management...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com