Terminal device and starting method thereof
A technology of terminal equipment and bootloader, which is applied in the direction of instruments, electronic digital data processing, platform integrity maintenance, etc., can solve problems such as the inability to guarantee the security of intelligent terminals, achieve integrity and consistency, reduce costs, and reduce errors Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
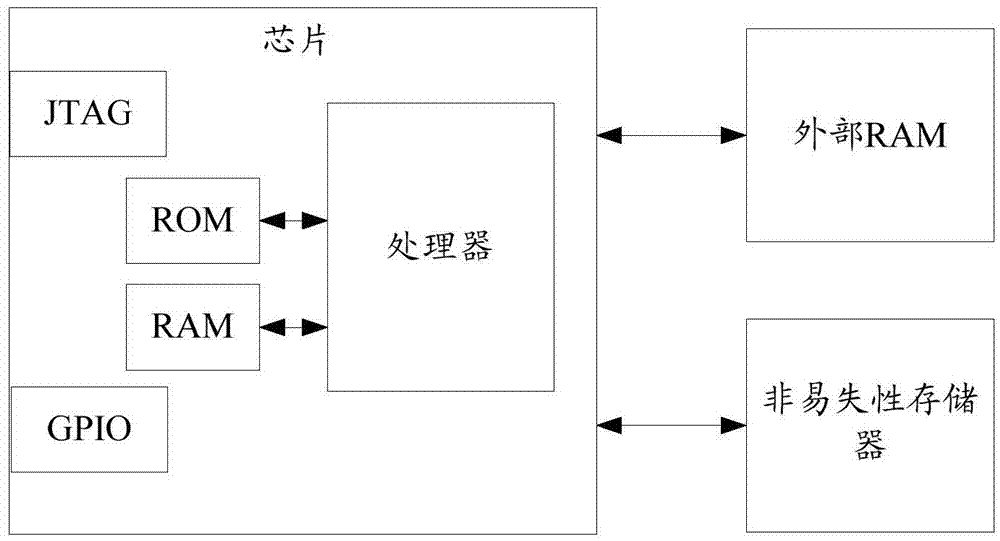
[0070] As mentioned in the background technology, all intrusions to the field of smart terminals need to change the system content, and almost all intrusions need to change key system files, so it is very necessary to verify the integrity and consistency of the system. The verification of consistency and consistency is carried out when the smart terminal is started, so as to ensure the safe start of the smart terminal. However, the start-up process of the terminal device in the prior art does not verify the code, and the code may have been changed and cracked, thereby threatening system security.
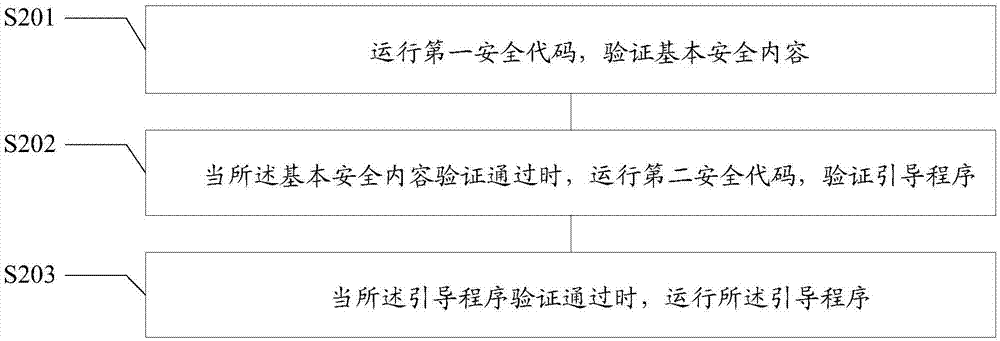
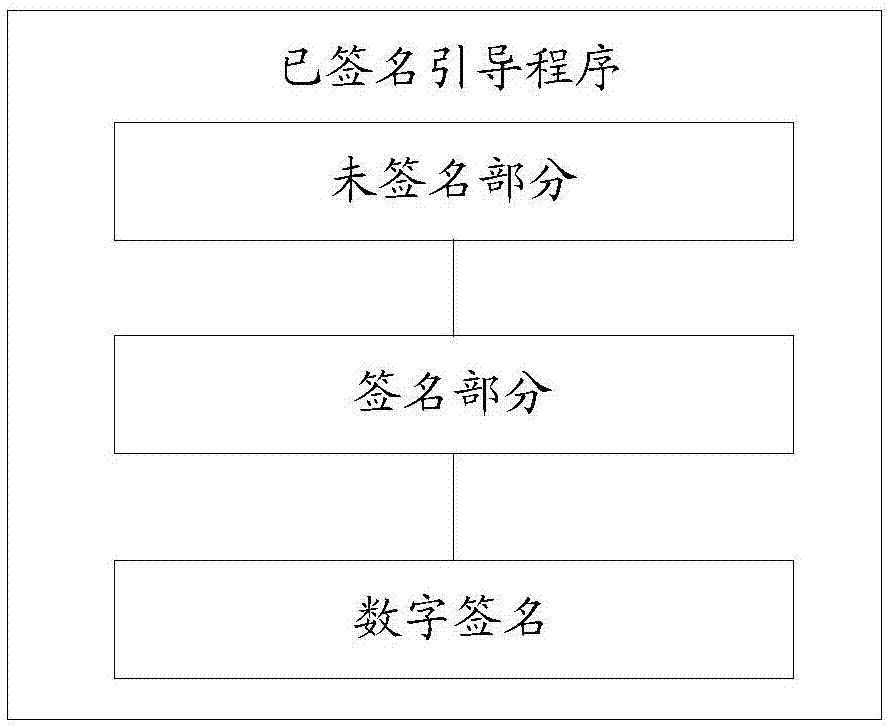
[0071] In the embodiment of the present invention, the basic security content is verified by running the first security code. When the basic security content is verified, the second security code is run to verify the boot program. When the boot program is verified, the boot program is run. , wherein, the basic security content and the boot program are stored in a non-volatile first ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com