Network access method and system
A network access and network technology, applied in the electronic field, can solve the problems of user inconvenience and complicated operation, and achieve the effect of reducing the number of times
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
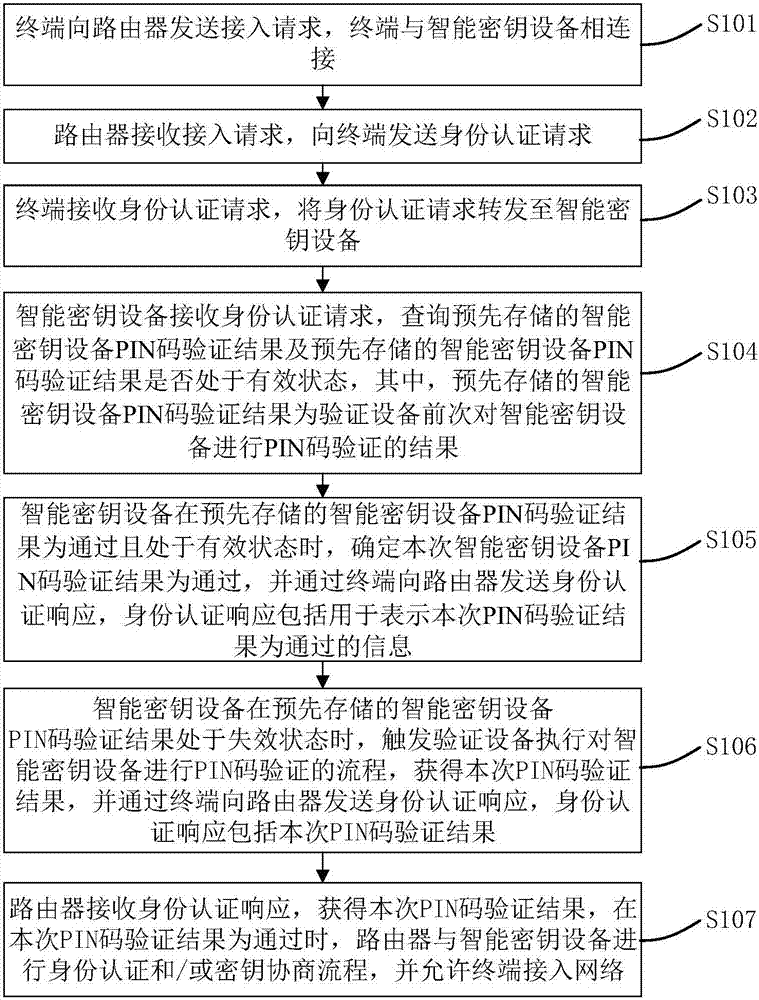
[0027] This embodiment provides a network access method, such as figure 1 As shown, including the following steps (S101-S107):
[0028] S101. The terminal sends an access request to the router, and the terminal is connected to the smart key device.
[0029] In this embodiment, the terminal may be any terminal with a network access function, for example, a smart phone, a tablet computer, a PC, etc., which is not specifically limited in this embodiment. The router has an identity authentication function, specifically: the router has a built-in security chip, and the security chip stores digital certificates and / or private keys; or the router has built-in software to realize the digital certificate function; or the router is connected to an external smart key device. The smart key device is a device with a security chip. The security chip has an independent processor and storage unit, which can store PKI digital certificates, private keys, encryption and decryption keys, verific...
Embodiment 2
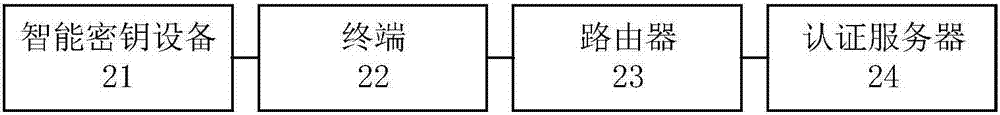
[0065] This embodiment provides a network access system, figure 2 A schematic structural diagram of the network access system provided in this embodiment.
[0066] Such as figure 2 As shown, the network access system provided in this embodiment includes: a smart key device 21, a terminal 22 and a router 23; the terminal 22 is connected to the smart key device 21, and is used to send an access request to the router 23; the router 23, It is used to receive an access request and send an identity authentication request to the terminal 22; the terminal 22 is also used to receive the identity authentication request, and forwards the identity authentication request to the smart key device 21; the smart key device 21 is used to receive the identity authentication request Request to query the pre-stored PIN code verification result of the smart key device and whether the pre-stored PIN code verification result of the smart key device is valid, wherein the pre-stored PIN code verific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com