A Semantic Location Privacy Preservation Method Based on Edge Cluster Graph
A technology of privacy protection and semantic location, which is applied in the field of network security and privacy protection, can solve the problems of low service quality, inability to guarantee the anonymous set structure, and slow anonymous speed, so as to improve query efficiency, reduce anonymous time, and increase success rate Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
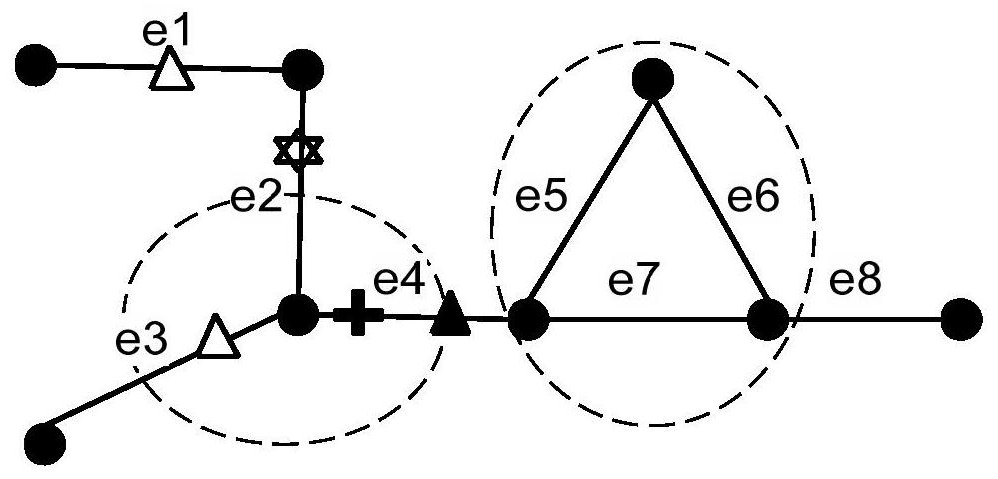
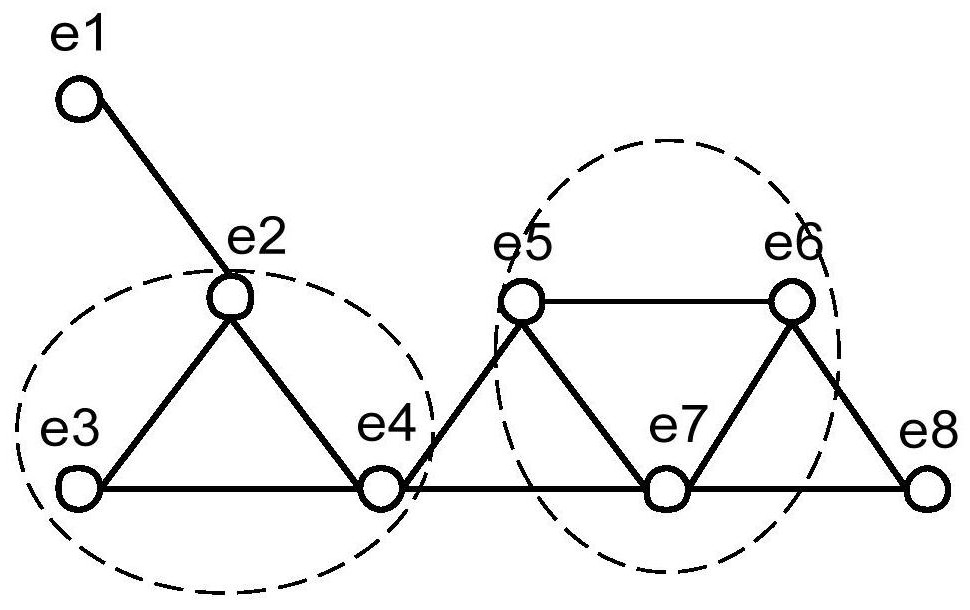
[0027] The present invention adopts such as figure 1 The system structure based on a trusted third party is shown. The system is mainly divided into three parts: LBS users, anonymous servers, and location servers. LBS users are location service requesters, and anonymous servers execute anonymous algorithms to protect user requests. Service provider, responding to requests protected by anonymity.
[0028] A kind of semantic position privacy protection method based on edge cluster graph provided by the present invention is described in detail below, for convenience of description, at first make following definition:
[0029] Definition 1: (user privacy preference profile) The privacy preference sent by the user to the anonymous server is expressed as profile=(k,l,θ,v,l max );
[0030] Among them, k, l, and θ respectively indicate that the anonymous set needs to contain at least k users and l road sections, θ is the user sensitivity threshold, that is, the ratio of the sum of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com