Safety access control method of hard disk and hard disk
A security access control, hard disk technology, applied in the direction of internal/peripheral computer component protection, digital data authentication, etc., can solve the problem that the data security of the mobile hard disk cannot be effectively guaranteed, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
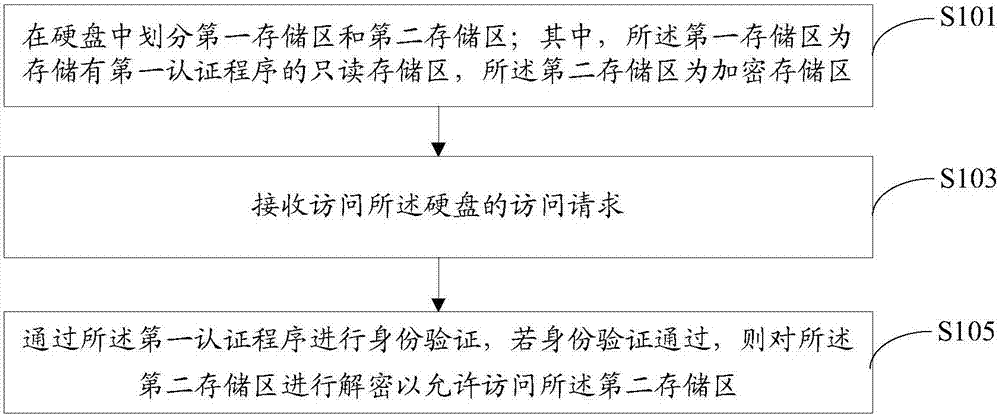
[0038] The embodiment of the present application discloses a security access control method for a hard disk, see figure 1 shown, including the following steps:
[0039] Step S101 , dividing a first storage area and a second storage area in the hard disk; wherein, the first storage area is a read-only storage area storing a first authentication program, and the second storage area is an encrypted storage area.
[0040] Taking the mobile hard disk as an example, the mobile hard disk is divided into the first storage area and the second storage area. When the mobile hard disk is connected to the computer, the computer can only load the read-only storage area of the mobile hard disk, that is, the first storage area. The second storage area is used as an encrypted storage area, which can be loaded by the computer only through authentication.
[0041] It is pointed out here that in the embodiment of the present application, the mobile hard disk is not limited to only include the ...
Embodiment 2
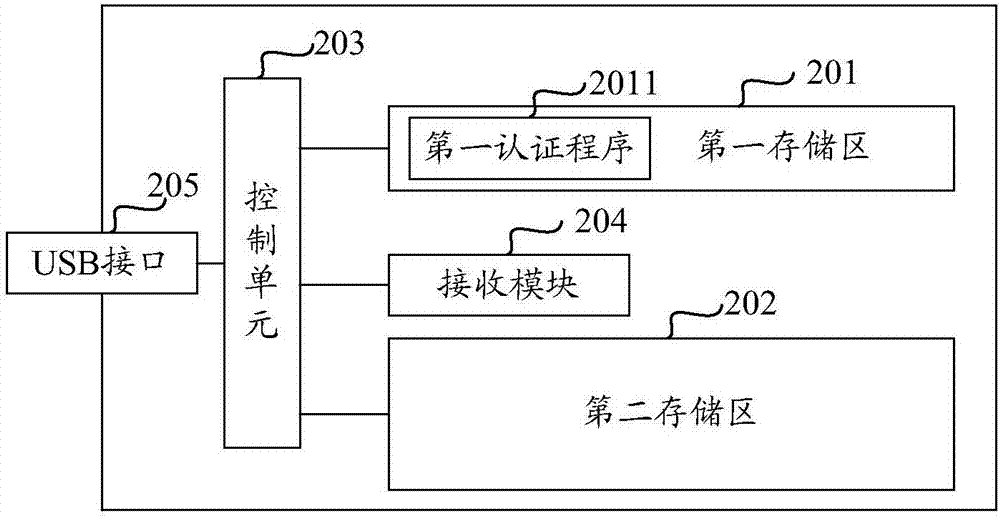
[0064] see figure 2 As shown, the embodiment of the present application provides a hard disk, and the hard disk includes a first storage area 201 , a second storage area 202 , a control unit 203 , a receiving module 204 and a USB interface 205 .
[0065] The first storage area 201 is a read-only storage area. When the computer is connected to the hard disk, the user can only view the contents of the first storage area 201 through the computer, but cannot write to it. A first authentication program 2011 is stored in the first storage area 201 for verifying the identity of the user accessing the second storage area 202 . The second storage area 202 is an encrypted storage area, which can only be accessed after authentication.
[0066] Setting the first authentication program 2011 in the first storage area 201 effectively prevents the technical problem that the first authentication program is tampered with.
[0067] After the receiving module 204 receives the access request fo...
Embodiment 3
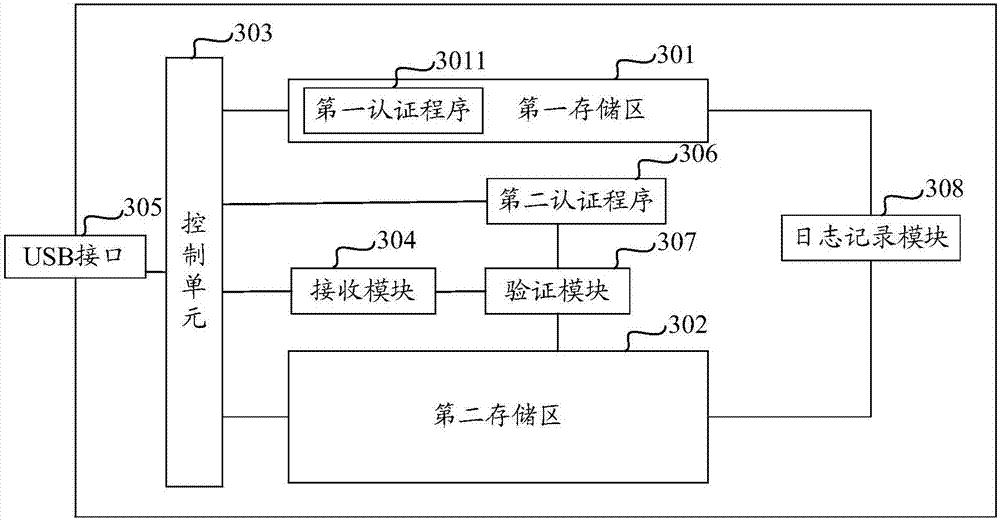
[0080] see Figure 4 As shown, it is a flowchart of a method for using a hard disk in the embodiment of the present application, including the following steps:
[0081] Step S401, access to the computer.
[0082] In the embodiment of the present application, a mobile hard disk is taken as an example for illustration.
[0083] Step S402, loading the first storage area.
[0084] In the embodiment of the present application, the first storage area is a read-only storage area, and a first authentication program is stored in the first storage area, which is used to verify the identity information of the user who wants to access the second storage area.
[0085] Step S403, running the first authentication program.
[0086] After the first storage area is loaded, the first authentication program located in the first storage area is automatically run, and when the identity information of the user who wants to access the second storage area is verified by the first authentication pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com