Identity authentication method and apparatus thereof
A technology of identity authentication and target text, applied in the field of biosafety dynamic authentication, which can solve problems such as loss of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
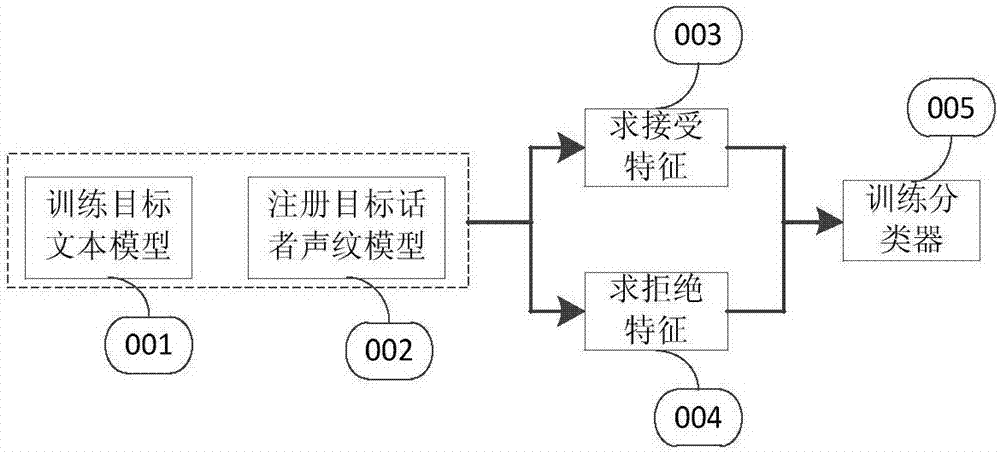
Method used
Image
Examples
Embodiment 1
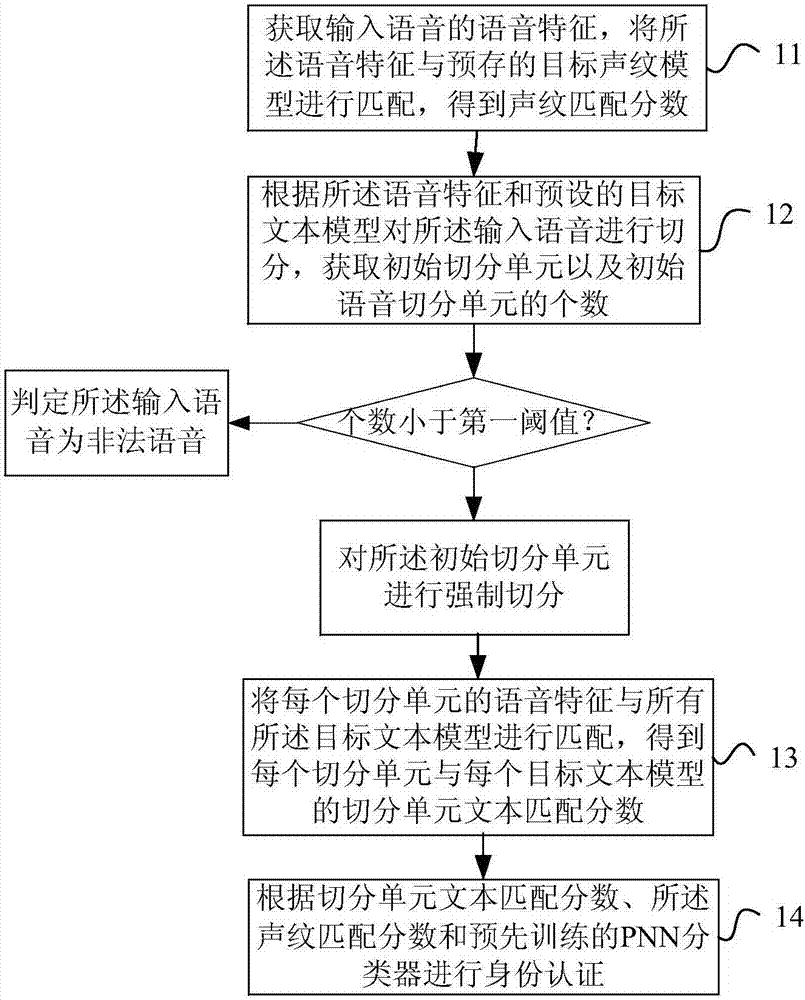
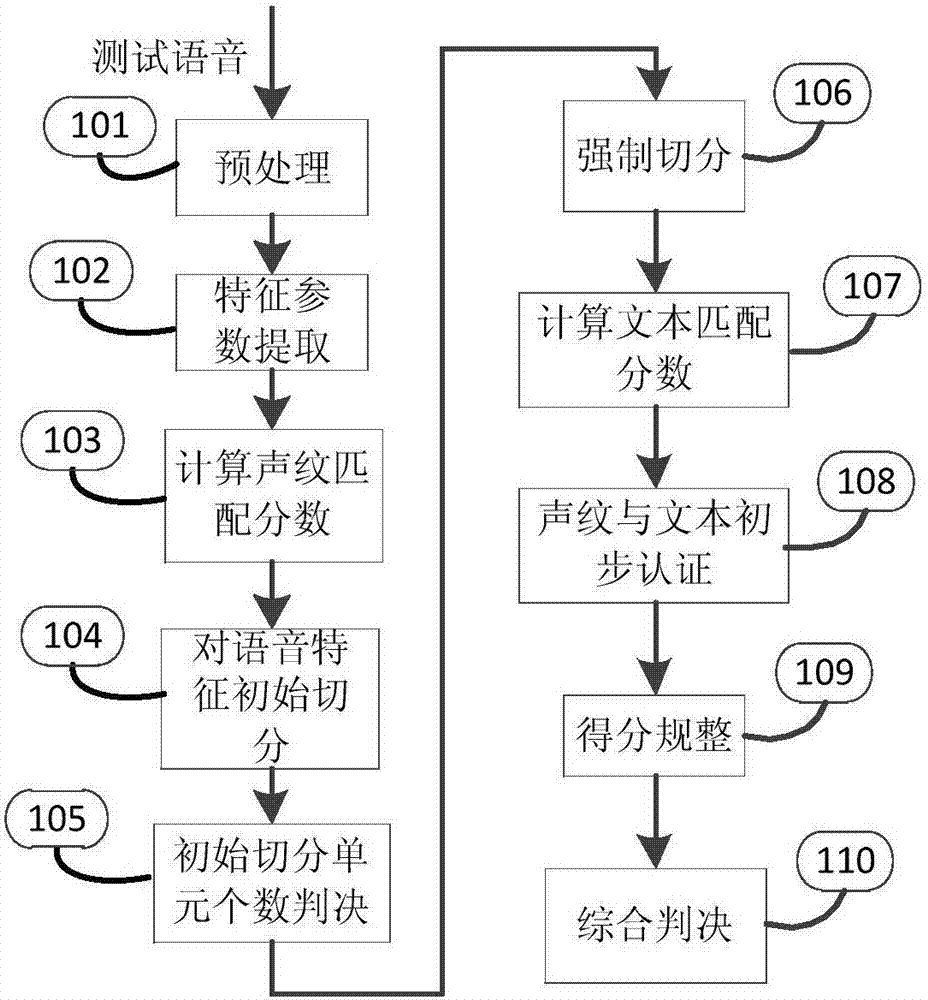
[0097] like image 3 shown, including the following steps:
[0098] Step 101, preprocessing: preprocessing the test speech input by the user according to the short-term energy and short-term zero-crossing rate, removing non-speech segments in the speech;
[0099] Step 102, feature parameter extraction: perform feature parameter extraction on the preprocessed test speech, the system can use 12-dimensional Mel Frequency Cepstrum Coefficient (Mel Frequency Cepstrum Coefficient, referred to as MFCC) and its first-order difference coefficient as feature parameters, A total of 24 dimensions;
[0100] Step 103, calculating the voiceprint matching score: matching the test speech features with the voiceprint model of the target speaker to obtain the voiceprint matching score;
[0101] Step 104: Initial segmentation of speech features: through initial segmentation of test speech features, initial segmentation units and the number of initial segmentation units are obtained.
[0102] I...
Embodiment 2
[0141] For the initial segmentation of speech features in step 104 in the first embodiment, the determination of the number of segmentation units in step 105, and the mandatory segmentation in step 106, the following methods are used in the present embodiment to perform segmentation and determination:
[0142] Step 201, voice signal initial segmentation;
[0143] In this embodiment, splitting is started according to the order of the length of the initial segmentation unit from large to small, and each initial segmentation unit is divided into two segments on average until the total number of segmentation units is equal to up to the number of the target text;
[0144] If the number of forced segmentation is greater than or equal to the second threshold, the forced segmentation ends; if the number of forced segmentation is less than the second threshold, each currently segmented unit is matched with each target text HMM for scoring , respectively select the target text HMM corr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com