Accurate cluster speed limiting method and device
An accurate and clustered technology, applied in the computer field, which can solve the problems of low operability, adding speed-limiting nodes, and poor applicability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
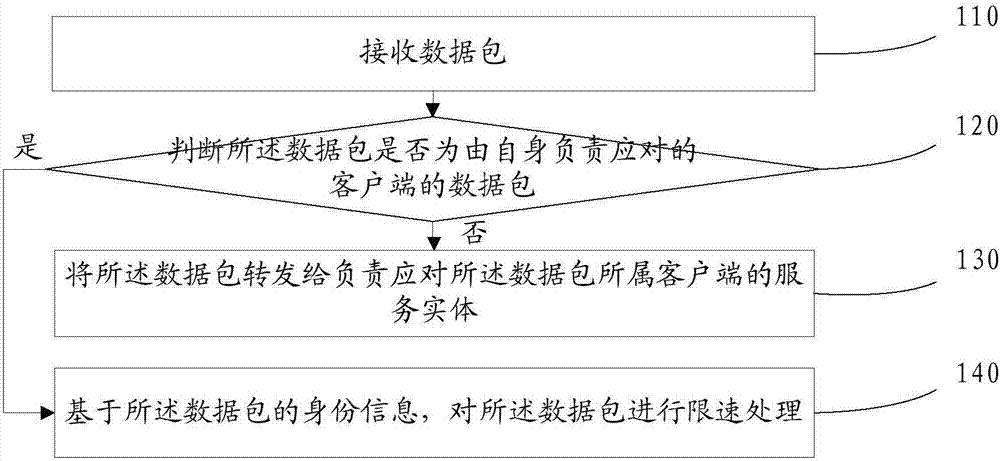
[0118] refer to figure 1, which shows a flow chart of the steps of an embodiment of a cluster precise rate limiting method of the present application, which may specifically include the following steps:
[0119] Step 110, receiving data packets.
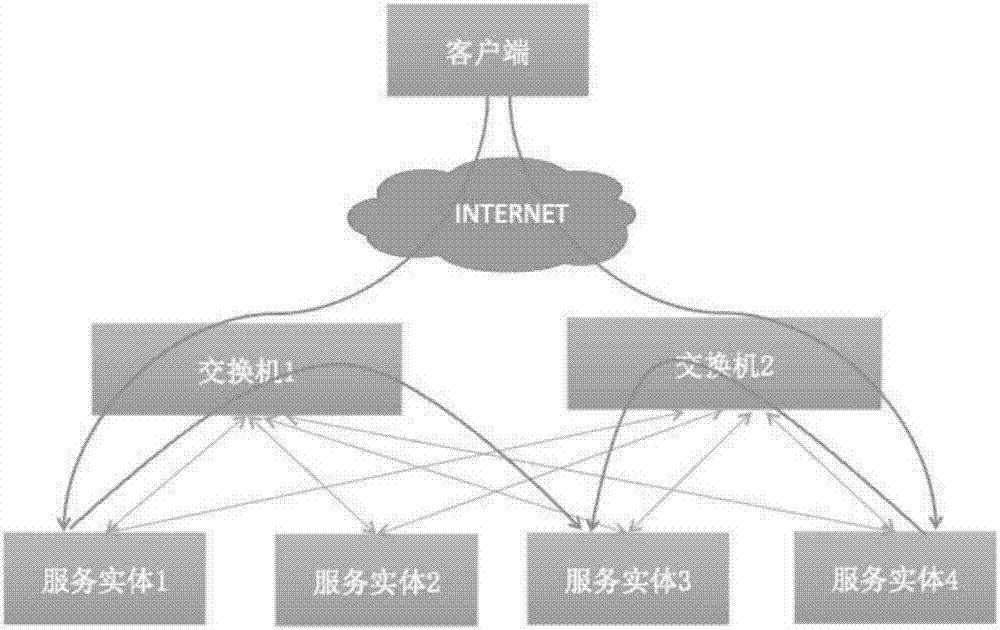
[0120] Such as Figure 1A It is a schematic diagram of an application scenario of this application. It can be seen that there are 4 service entities inside the cluster, and the service entities communicate with the outside, such as the client, through each switch. The data packets sent by the client first pass through the switch, and then the switch distributes it to at least one service entity. deal with.
[0121] Among them, a cluster refers to a group of service entities that work together to provide a service platform that is more scalable and available than a single service entity. It mainly includes High Availability Cluster, Load Balance Cluster, and High Performance Computing Cluster. This application is mainly aimed at h...
Embodiment 2
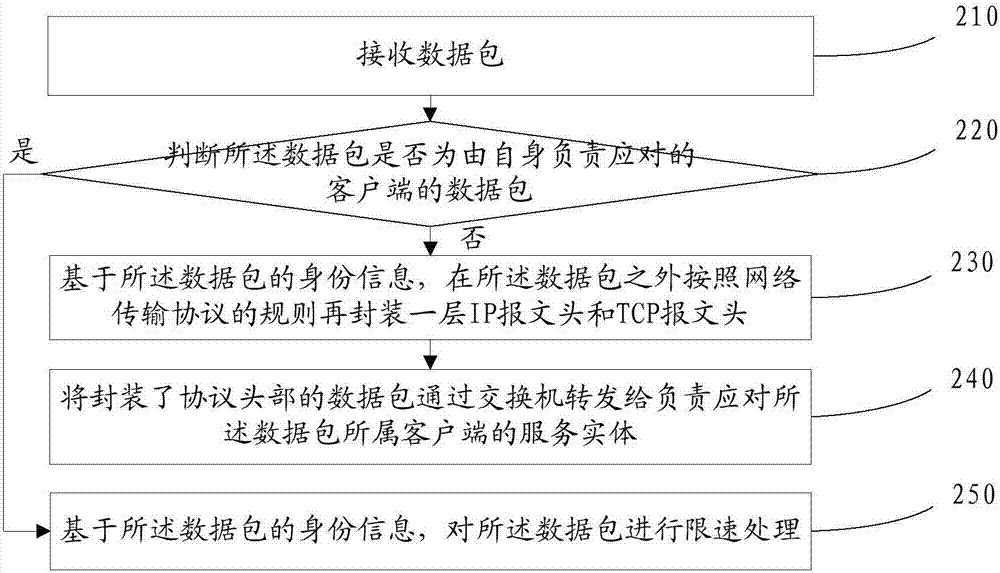
[0159] refer to figure 2 , which shows a flow chart of the steps of an embodiment of a cluster precise rate limiting method of the present application, which may specifically include the following steps:
[0160] Step 210, receiving a data packet.
[0161] Step 220, judging whether the data packet is a data packet of a client that is responsible for handling by itself; if the data packet is not a data packet of a client that is responsible for handling by itself, proceed to step 230; For the data packets of the corresponding client, go to step 250 .
[0162] Step 230: Based on the identity information of the data packet, an IP header and a TCP header are encapsulated outside the data packet according to the rules of the network transmission protocol.
[0163] Based on the advantages of the aforementioned TCP, in order to ensure the correctness of the data during the forwarding process of the data packet, in the embodiment of the present application, based on the identity in...
Embodiment 3
[0200] refer to image 3 , which shows a flow chart of the steps of another embodiment of the cluster precise rate limiting method of the present application, which may specifically include the following steps:
[0201] Step 310, receiving a data packet.
[0202] Step 320, judging whether the data packet is forwarded by the service entity or sent by the client; if the data packet is forwarded by the service entity, confirm that the data packet is not handled by itself If the data packet is a data packet sent by the client, then confirm that the data packet is a data packet of the client responsible for handling, and then enter step 350.
[0203]It can be seen from the first embodiment that in practical applications, if the data packet received by the service entity is a data packet of the client, the data packet will be forwarded to the service entity responsible for dealing with the client to which the data packet belongs, and in Before forwarding, the service entity cannot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com