A method for updating terminal equipment program
A technology for updating programs and terminal equipment, applied in transmission systems, software deployment, electrical components, etc., can solve problems such as high operational complexity, leakage of important files, difficult operation, etc., to simplify the operation process and improve data security , the effect of process simplification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
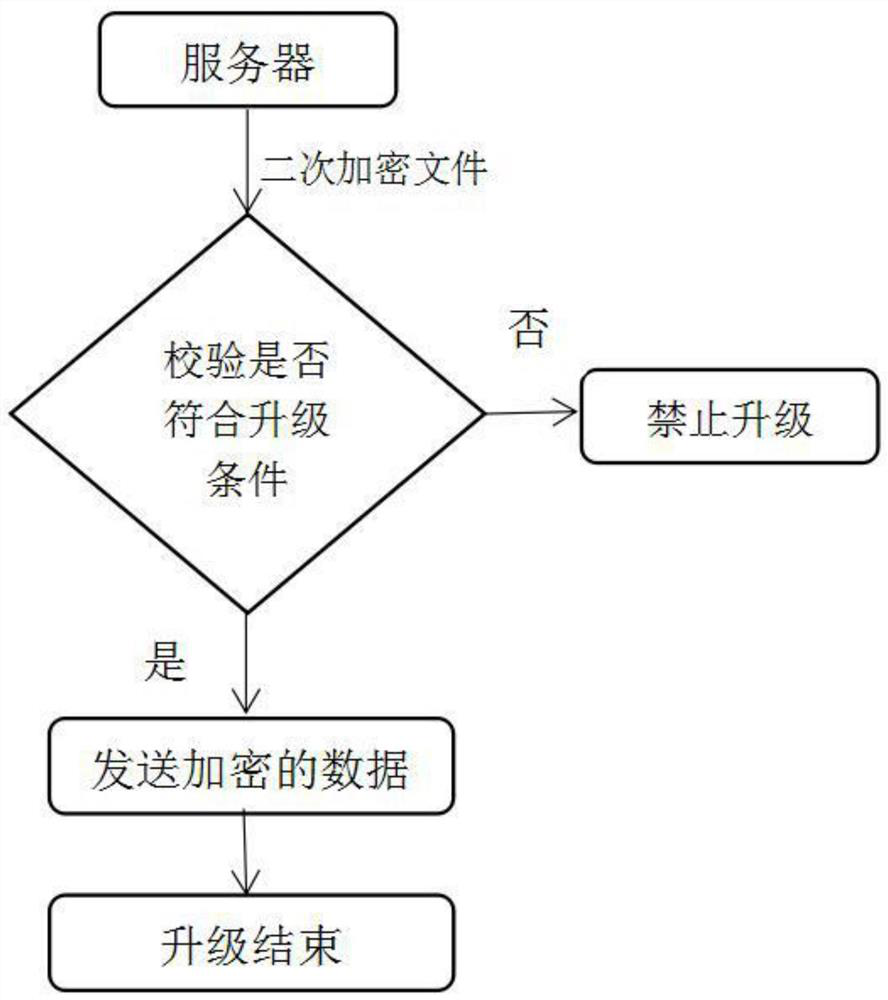
[0040] A method for updating a terminal device program, comprising the following steps,
[0041] 1) Establish an encrypted internal communication mechanism
[0042] Customize a dedicated encrypted internal communication mechanism based on the serial communication between the control terminal and the terminal connection.
[0043] 2) Encryption and decoding
[0044] Encryption module: Encrypt the update package twice. For the encryption process of the update program package, you can choose to encrypt it directly at the manufacturer to effectively prevent the update data from leaking.
[0045] Decoding module: the decoding module is installed on the control terminal, and the decoding module communicates with the terminal through a serial port. This decoding module is to decrypt the secondary encryption in the update program package.
[0046] 3) Get the update package
[0047] Acquisition module: an acquisition module is integrated on the control terminal, and the acquisition...
Embodiment 2
[0060] The difference between this embodiment and Embodiment 1 is: Step 6) Divide the update program package into several data blocks, send and decrypt them in batches.
[0061] details as follows,
[0062] The control terminal divides the update program package into several data blocks and sends them to the terminal according to the storage space and memory size of the terminal;
[0063] The terminal receives the data block correspondingly multiple times, and the data block received each time is decrypted and verified by the decryption module; if the verification is successful, the data is partially updated; if the verification fails, the data block received this time is discarded ;
[0064] Repeat receiving, decrypting and verifying until the file is received. After the file is received, the terminal verifies the integrity of the update package through the decryption module. If the integrity verification is successful, the program update is successful; if the integrity ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com