Access control method and system based on security state of terminal host
A technology of access control and security state, applied in the transmission system, electrical components, etc., can solve the problems of equipment insecurity, safety, and legality judgment of inaccessible equipment, and achieve the effect of precise access control and ensuring security
Inactive Publication Date: 2017-11-07
BEIJING VRV SOFTWARE CO LTD
View PDF4 Cites 7 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0002] The current access control domain is in accordance with 7 In terms of layer protocol division, it is mainly divided into access layer access control and network layer based on IP Access control, access layer control mainly includes 802.1x certified, but 802.1x There are certain flaws in certification, on the one hand due to 802.1x It is based on port-level authentication. Once the authentication is passed, no further access control can be done, causing certain security problems. On the other hand, if the port is connected to NAT equipment, as long as NAT If one terminal passes the authentication, the rest of the terminals are considered safe, and precise access control cannot be realized. However, access control at the network layer mainly includes PORTAL certified, PORTAL Authentication is easy to use, but there are also some disadvantages. It is impossible to judge the legality of the access device, but only to verify the legality of the user. Therefore, it is easy to cause the device itself to be insecure or have loopholes and viruses that threaten the network.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment approach
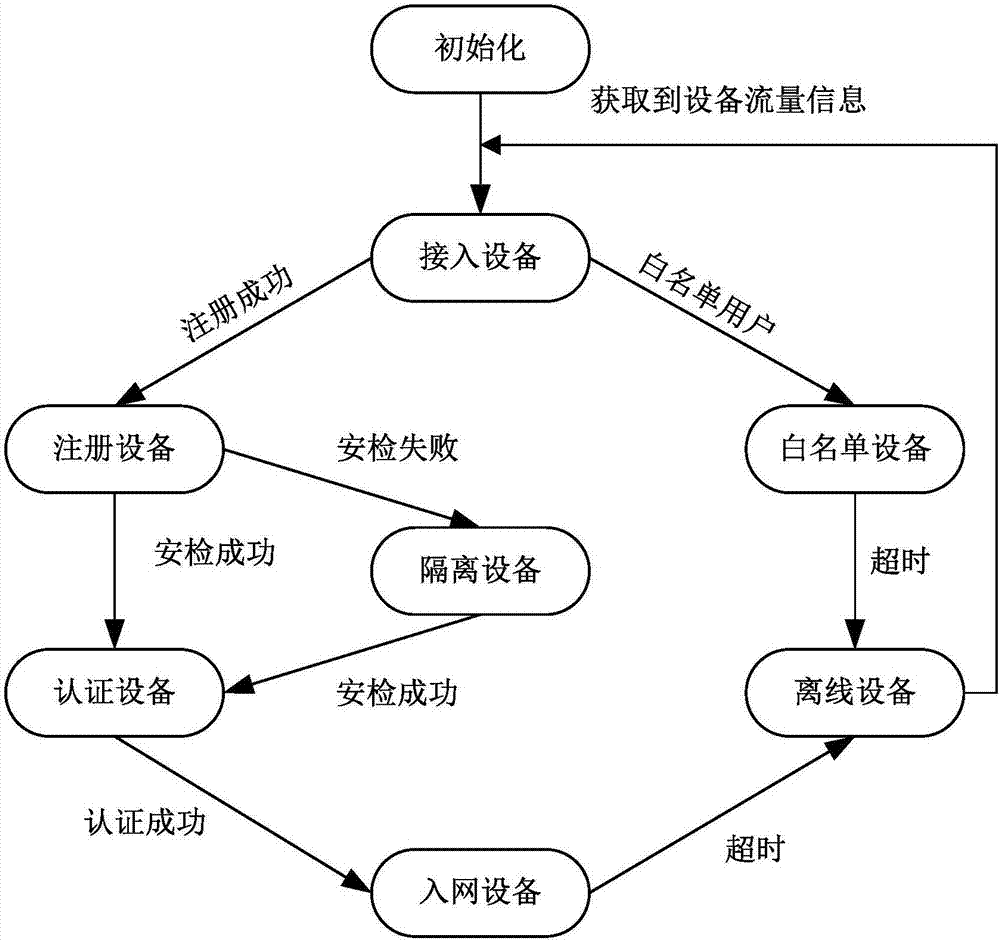
[0069] In a specific example 6, the access control method based on the security state of the terminal host in example 1, a preferred implementation of the "admission system performs state migration for the registered device according to the result of the security check", specifically includes the following figure 1 The steps not shown in are specifically:
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses an access control method based on a security state of a terminal host. The method comprises the following steps: judging an access state of an access terminal accessing network resources so as to judge to directly switch the access terminal to a network access device or enable the access terminal to enter an admission stage, wherein the admission stage comprises management registration, registration audit, security detection, authentication and authority management. According to the access control method disclosed by the invention, the objectives of device security, personnel security and network resource access security are achieved in stages, and the device network access flows are refined; the network access flows are more accurate by a plurality of states, accurate network access control of devices in different states is realized, and differential control of different users of different devices is realized.
Description
technical field [0001] The invention relates to the field of network security and access control, in particular to an access control method and system based on the security state of a terminal host. Background technique [0002] The current access control field is in accordance with 7 In terms of layer protocol division, it is mainly divided into access layer access control and network layer based on IP Access control, access layer control mainly includes 802.1x certified, but 802.1x There are certain defects in certification, on the one hand, due to 802.1x It is based on port-level authentication. Once the authentication is passed, no further access control can be done, causing certain security problems. On the other hand, if the port is connected to NAT equipment, as long as NAT If one terminal passes the authentication, the rest of the terminals are considered safe, and precise access control cannot be realized. However, access control at the netw...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L29/06
CPCH04L63/08H04L63/101H04L63/105
Inventor 杨华刘文超王斌宋成龙
Owner BEIJING VRV SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com