Image-based verification code implementation method and device
An implementation method and verification code technology, which are applied in secure communication devices, user identity/authority verification, digital data authentication, etc., can solve the problems of not preventing automatic recognition of machines, negative effects on user experience, and users cannot see characters clearly. Good user experience, strong security protection, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
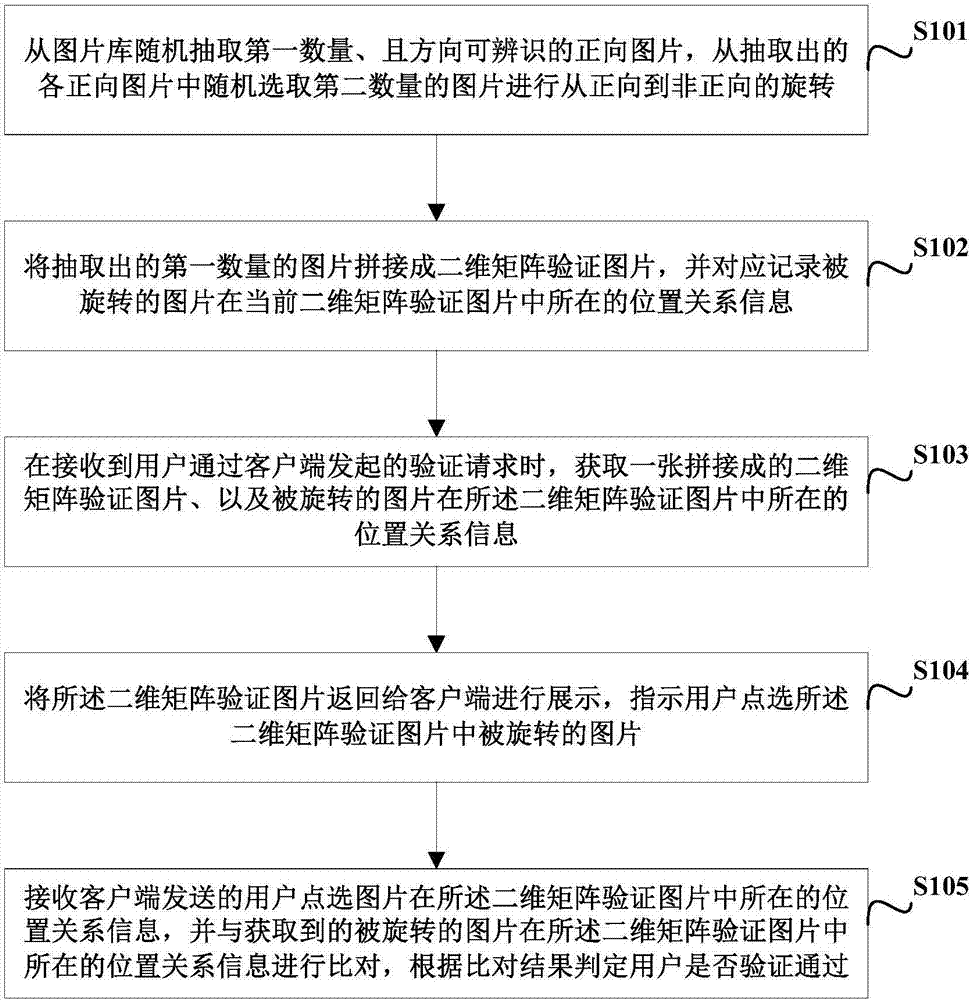
[0045] The present invention aims to provide a method and device for realizing a verification code based on a picture, which can effectively prevent malicious access of a machine, and at the same time, realize simple implementation and easy operation, and can bring good user experience.
[0046] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention. And in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
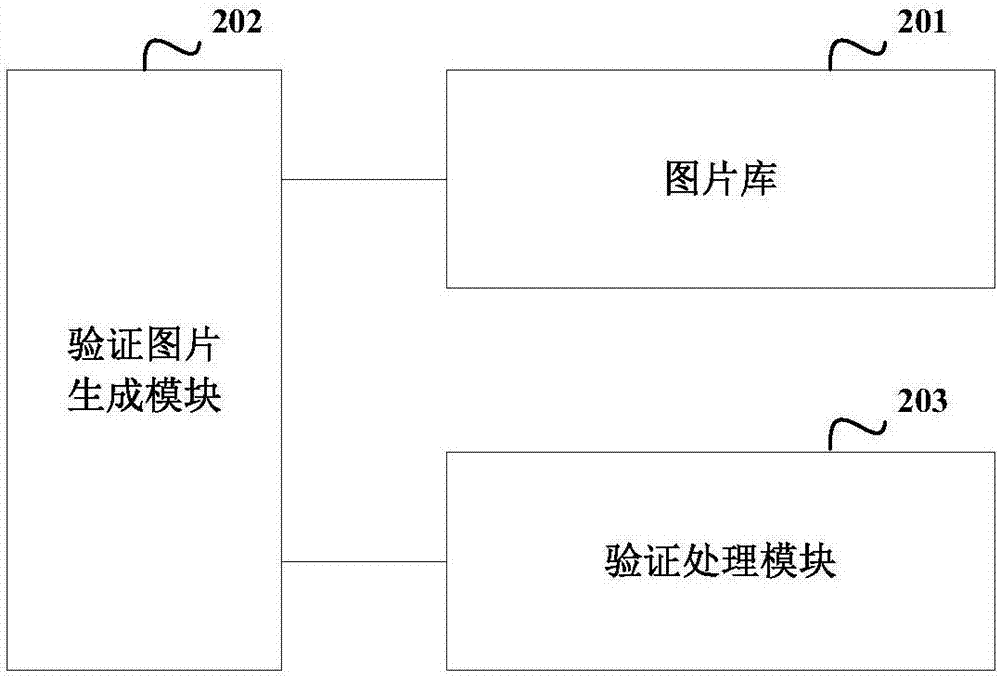
[0047] Such as figure 1 As shown, the image-based verification code implementation method provided by the embodiment of the present invention includes the following steps:
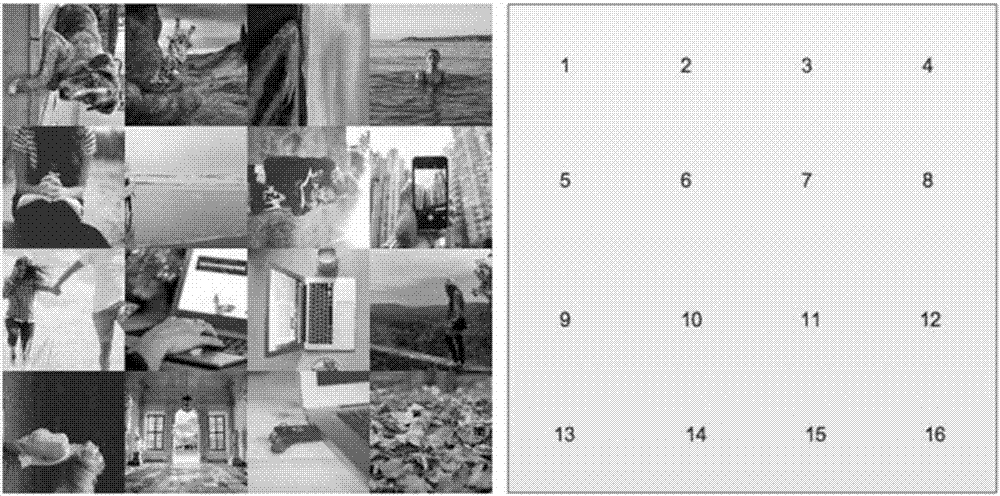
[0048] S101. Randomly extract a first number of forward pictures ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com