System and method for providing computer network security
A computer network and security technology, applied in transmission systems, electrical components, etc., to improve network security, facilitate detection of intrusions, and eliminate threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
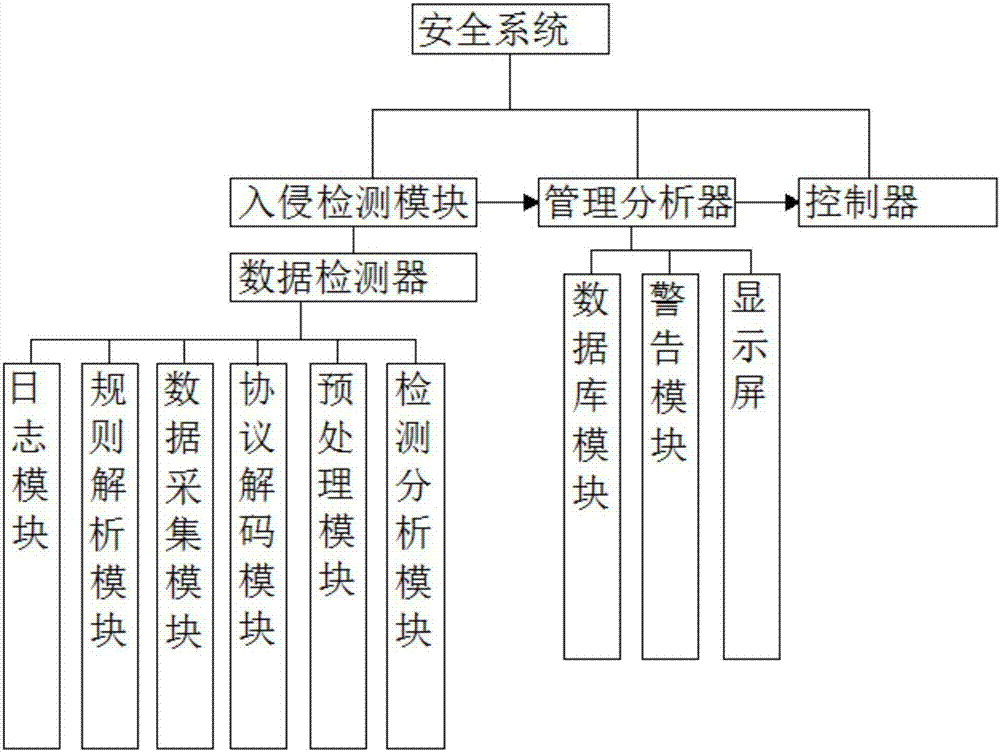
[0024] A system for providing computer network security includes multiple intrusion detection modules, multiple management analyzers, and controllers. The intrusion detection module is used to collect data transmitted on a target network segment, and manage the The intrusion rules preset by the analysis center perform real-time tracking and detection of intrusions from internal and external networks. The management analyzer is used to manage the data detector and at the same time is responsible for the analysis of alarm information. The controller is used for safety management. The center is guided by corresponding commands to configure network equipment, eliminate threats, block intruders, send warnings to intranet users, and fix vulnerabilities.
[0025] Specifically, the intrusion detection module includes a data detector, and the data detector includes a data acquisition module, a protocol decoding module, a preprocessing module, a detection analysis module, a rule analysis mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com