A two-stage merging method based on log-structured merging trees
A stage and log technology, applied in the field of information storage, can solve the problems of high read-write amplification rate access delay jitter, unsuitable for non-durable devices, unable to provide storage services, etc., to reduce the read-write amplification rate and solve the problem of write amplification And the effect of storage service performance degradation and device random read performance improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be described in detail below in conjunction with the accompanying drawings. However, it should be understood that the accompanying drawings are provided only for better understanding of the present invention, and they should not be construed as limiting the present invention.
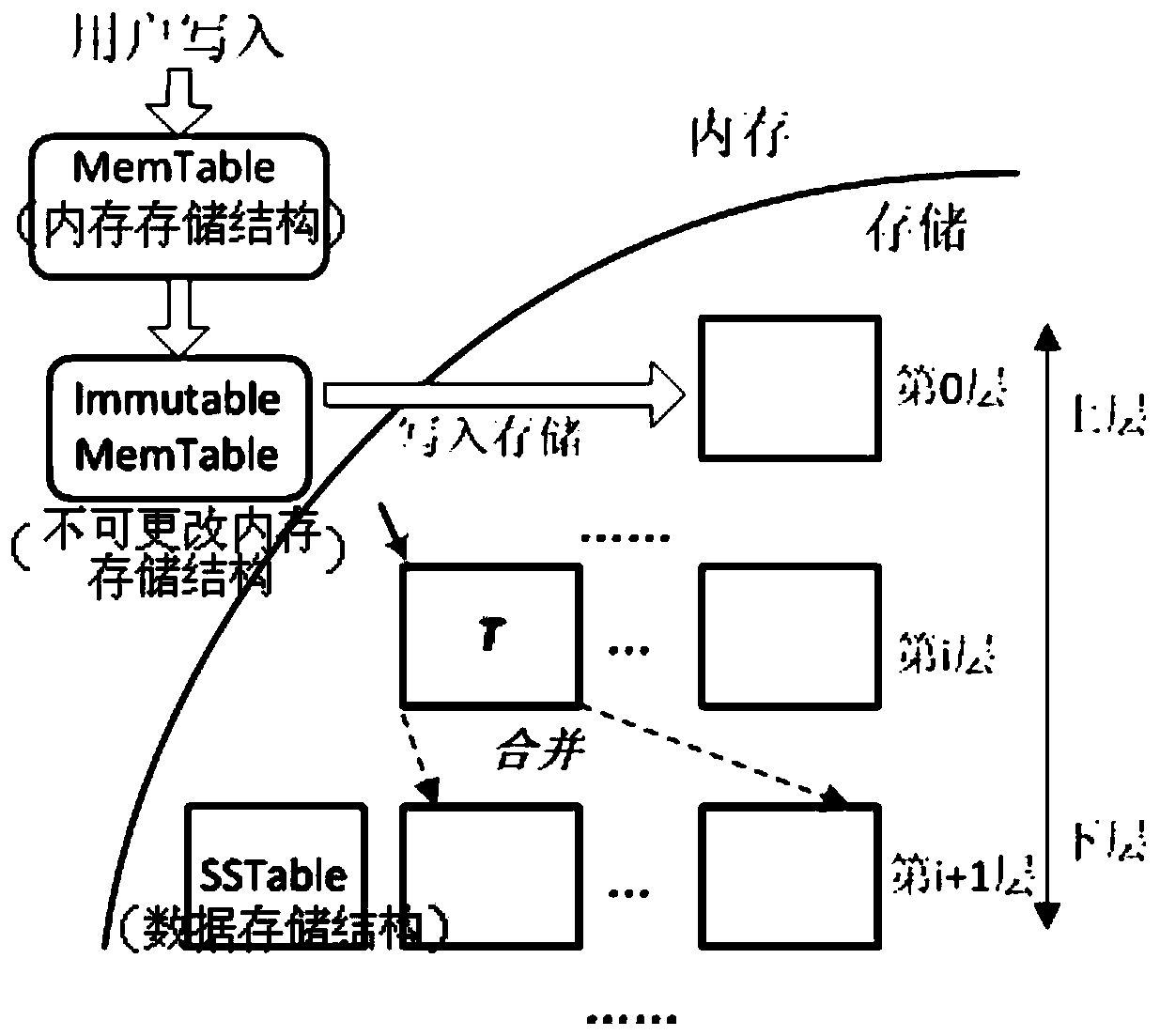
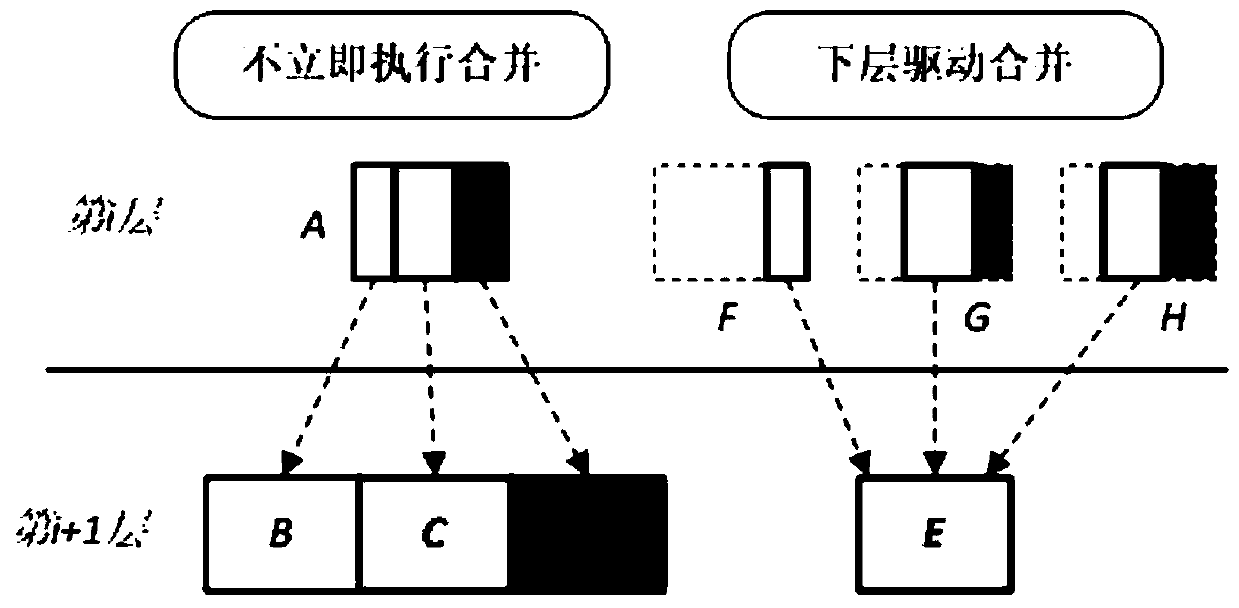
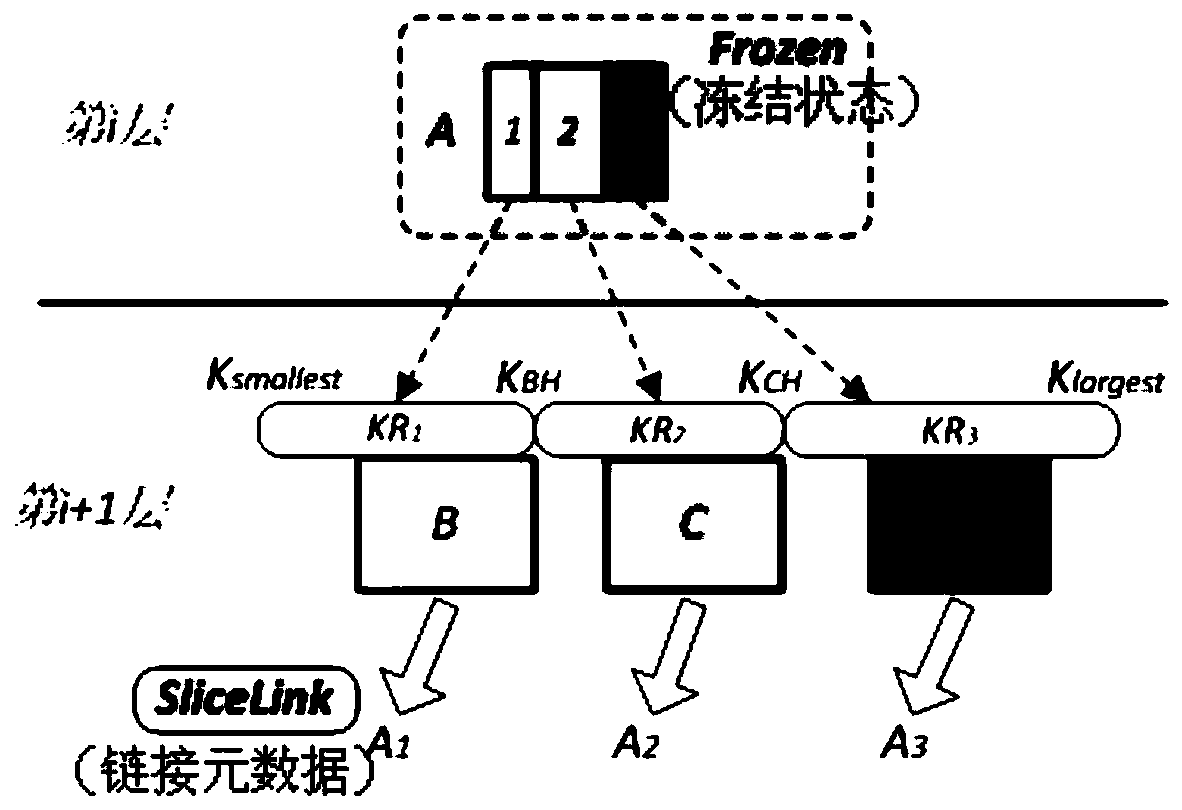
[0017] Such as figure 1 As shown, the two-stage merging method can be divided into two steps: the linking stage and the merging stage. When an upper-level file A is selected as the target file by the merging process, it starts to enter the linking stage. The merging operation at this stage does not need to be executed immediately, but Split the upper-level file A according to the key value range. Assuming that the upper-level file A needs to be merged with the lower-level files B, C, and D, the upper-level file A needs to be divided into three slices (Slice), and the key value range of each slice corresponds to the lower-level files B, C, and D respectively. When ther...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com