Method and apparatus for detecting data collection omission in traffic collection device
A technology of traffic collection and equipment data, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problem that the collection method of data wandering is not unique, and achieve the effect of improving the supervision effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
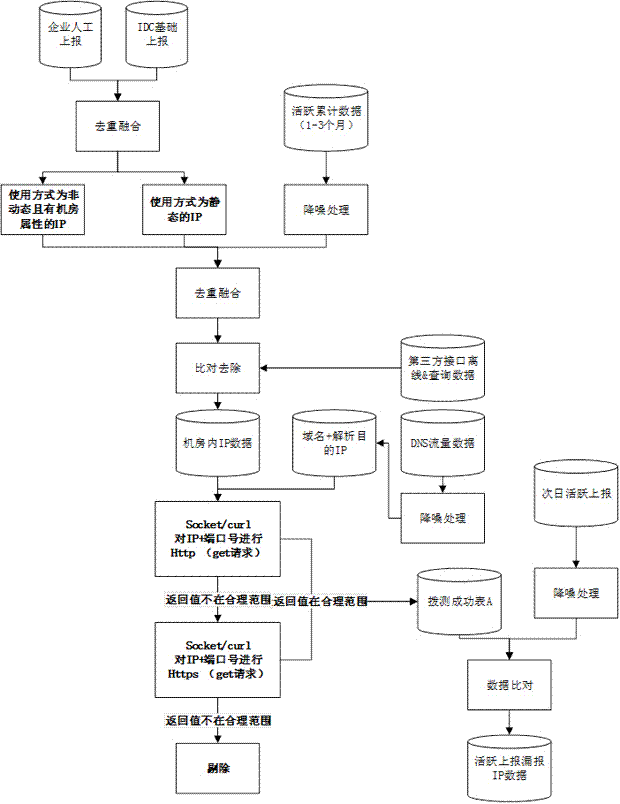
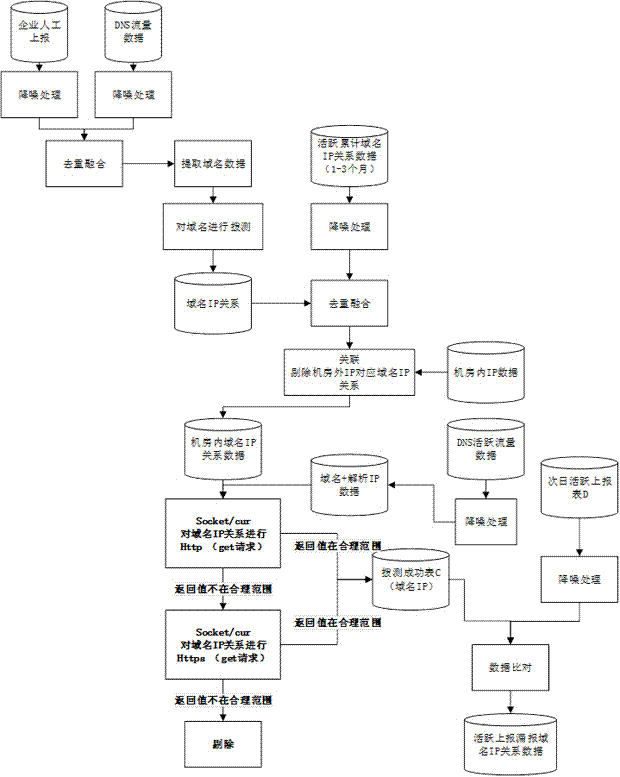
[0039] refer to figure 1 and figure 2 A method and device for detecting false positives in data collection of flow collection equipment according to the present invention includes: the first step of discovering false positives of active IP data, and the second step of finding false positives of active domain name data.
[0040] Step 1 The active IP data false negative discovery includes:
[0041] (1) For the underreporting of active IP data, it is necessary to obtain comprehensive IP data in the computer room in the province as a verification benchmark for the data underreported by the information security management system; the acquisition process of the IP benchmark table in the computer room of the information security management system is as follows: : a) From the IP data reported manually by the enterprise and on the basis of the enterprise IDC, find out the IP data that is used in a non-dynamic manner and has the property of the machine room; b) The IP data reported ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com