Penetrating method and device of symmetric NAT
A symmetrical, one-way technology, applied in the field of communication, can solve the problems of symmetrical NAT and port-restricted NAT that cannot be punched, and achieve the effect of improving the success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
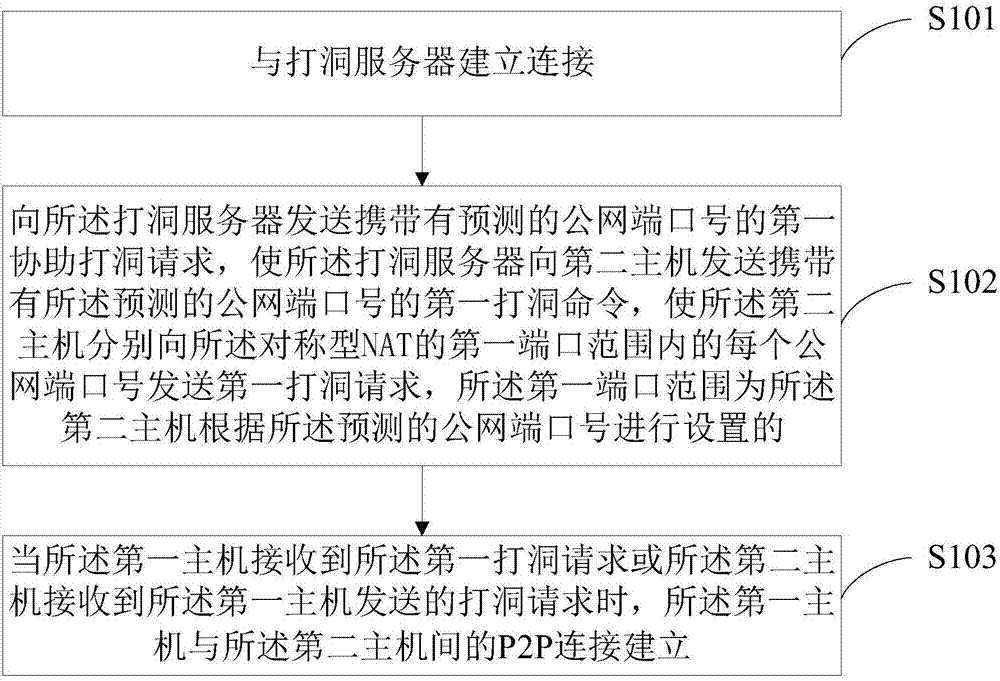
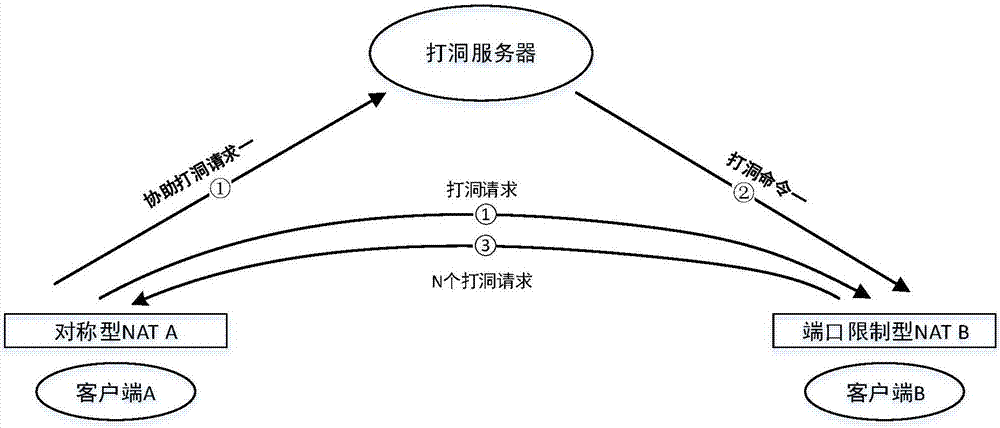
[0062] Based on the symmetric NAT penetration method disclosed in the first embodiment above, when the first host is the initiator of the hole punching request, and the NAT corresponding to the second host is a symmetric NAT,
[0063] In step S102: after sending the first assistance hole punching request carrying the predicted public network port number to the hole punching server, the method further includes:
[0064] receiving a second hole punching command carrying the NAT public network port number predicted by the second host sent by the hole punching server;
[0065] Set the second port range of the NAT corresponding to the second host according to the public network port number predicted by the second host, and send to each public network port in the second port range of the NAT corresponding to the second host respectively No. sends the second hole punching request;
[0066] When the second host receives the second hole punching request, a P2P connection between the f...
Embodiment 3
[0075] Based on the symmetric NAT penetration method disclosed in the first embodiment above, when the first host is the initiator of the hole punching request, and the NAT corresponding to the second host is a port-restricted NAT,
[0076] Before step S102: before sending the first assistance hole punching request carrying the predicted public network port number to the hole punching server, the method further includes:
[0077] sending a third hole punching request to the second host;
[0078] And, after step S102: after sending the first assisting hole punching request carrying the predicted symmetric NAT public network port number to the hole punching server, the method further includes:
[0079] A first hole punching request sent by the second host is received, and a P2P connection between the first host and the second host is established.
[0080] Specifically, when the first host is the initiator of the hole punching request, and the NAT corresponding to the second hos...
Embodiment 4
[0086] Based on the symmetric NAT penetration method disclosed in the first embodiment above, when the second host is the initiator of the hole punching request, and the NAT corresponding to the second host is a port-restricted NAT,
[0087] Before step S102: before sending the first assisting hole punching request carrying the predicted symmetric NAT public network port number to the hole punching server, the method further includes:
[0088] After the second host sends a second assist hole punching request to the hole punching server, receiving a third hole punching command sent by the hole punching server, and sending a fourth hole punching request to the second host;
[0089] And, after step S102: after sending the first assisting hole punching request carrying the predicted symmetric NAT public network port number to the hole punching server, the method further includes:
[0090] A first hole punching request sent by the second host is received, and a P2P connection between...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com