Borrowing methods and electronic equipment
A technology of equipment and content, applied in the field of borrowing methods and electronic equipment, can solve the problems of high fees, mindful price, failure to meet user expectations, etc., achieve the effect of low fees and increase popularity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
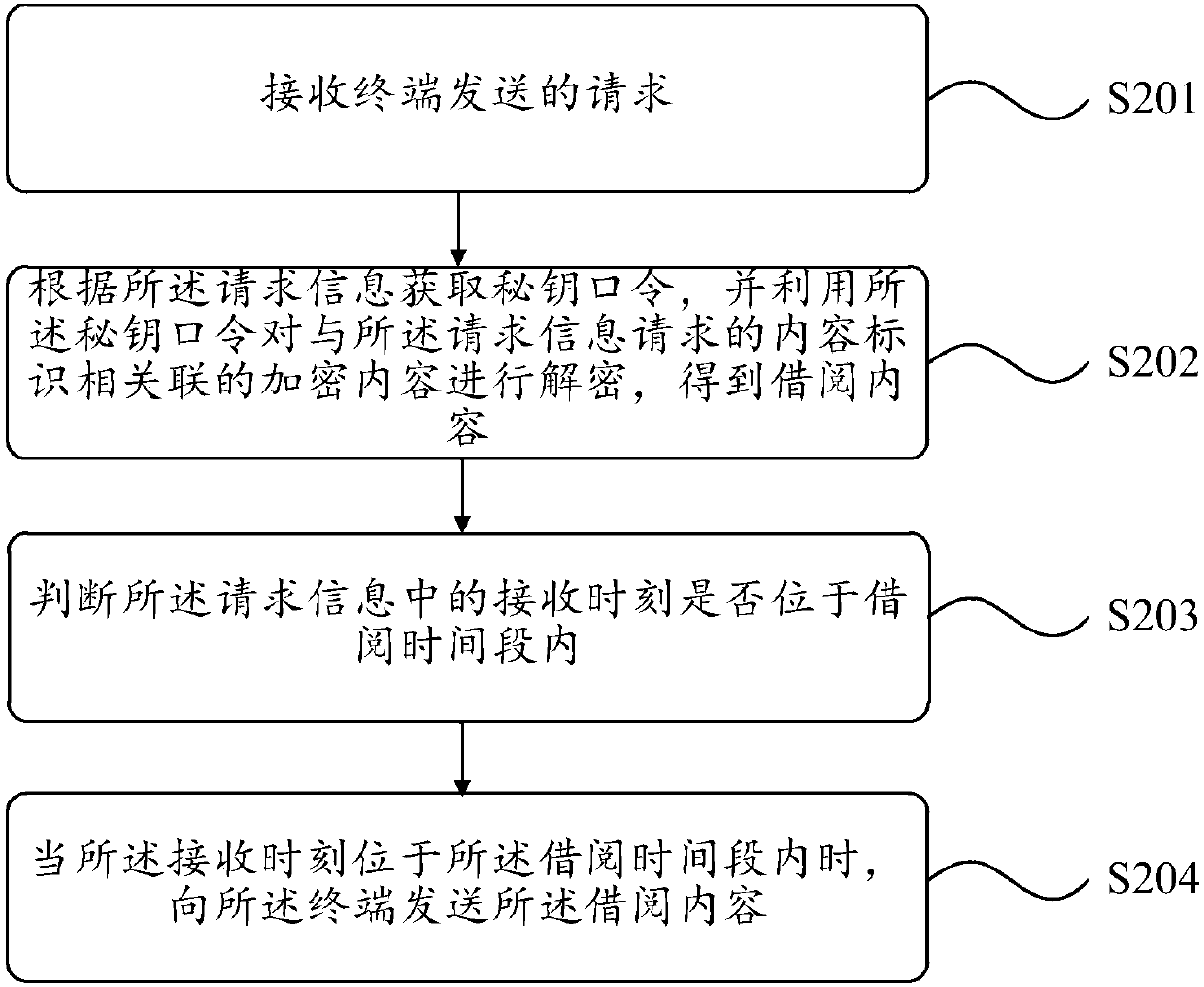
[0050] In order to facilitate the understanding of this embodiment, a borrowing method disclosed in the embodiment of the present invention is first introduced in detail. The first device used by this method includes a background or a terminal. The requested device, the terminal includes all devices that can access the Internet, such as mobile phones, tablet computers, etc. figure 1 A flow chart of a borrowing method is provided for the embodiment of the present invention, which can realize the reading of borrowed content that has been successfully borrowed, such as figure 1As shown, the method includes the following steps.
[0051] S201. Receive request information sent by a terminal.
[0052] S202. Obtain a secret key password according to the request information, and use the secret key password to decrypt the encrypted content associated with the content identifier requested by the request information to obtain the borrowed content.
[0053] Specifically, when the request...
Embodiment 2
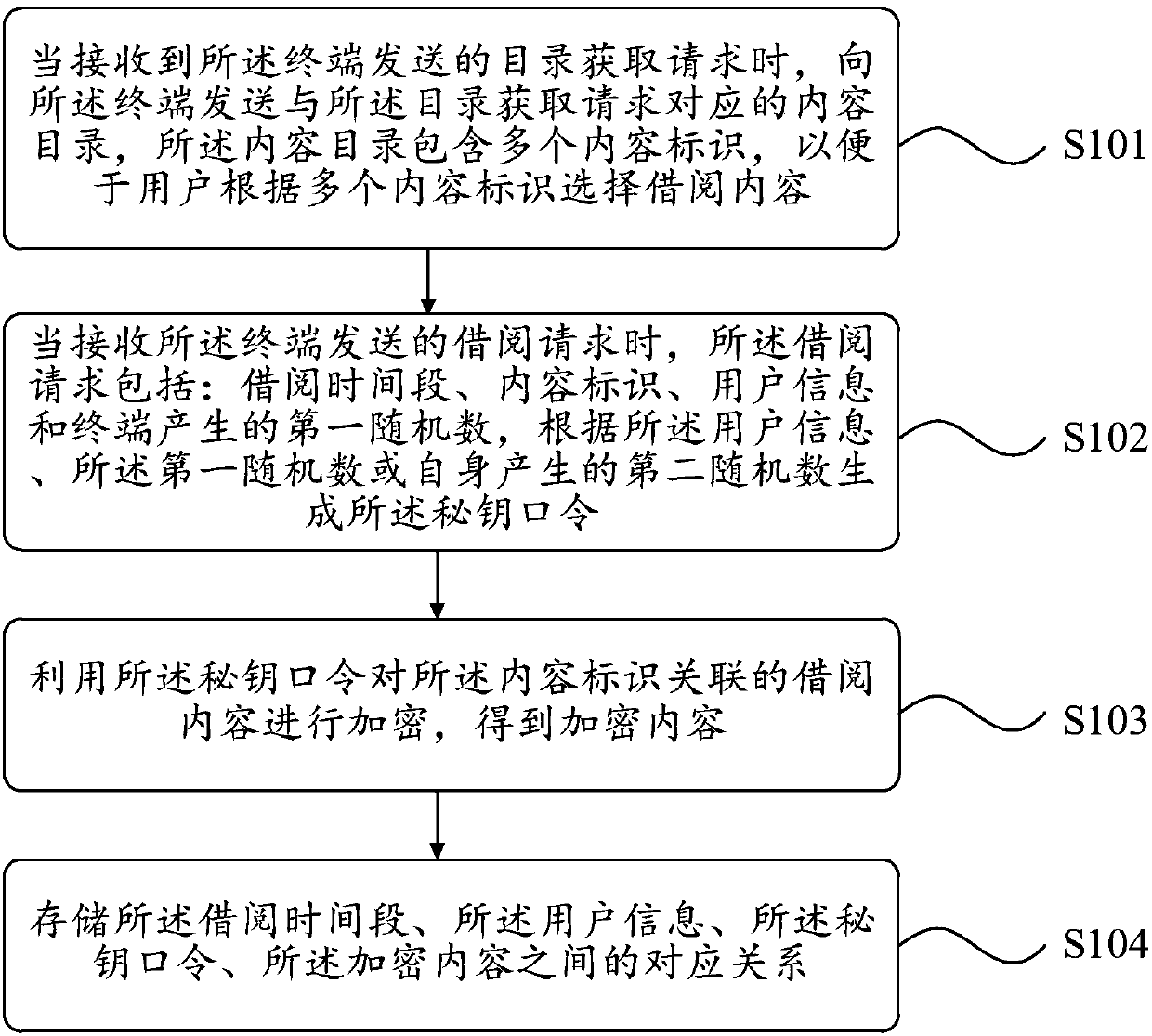
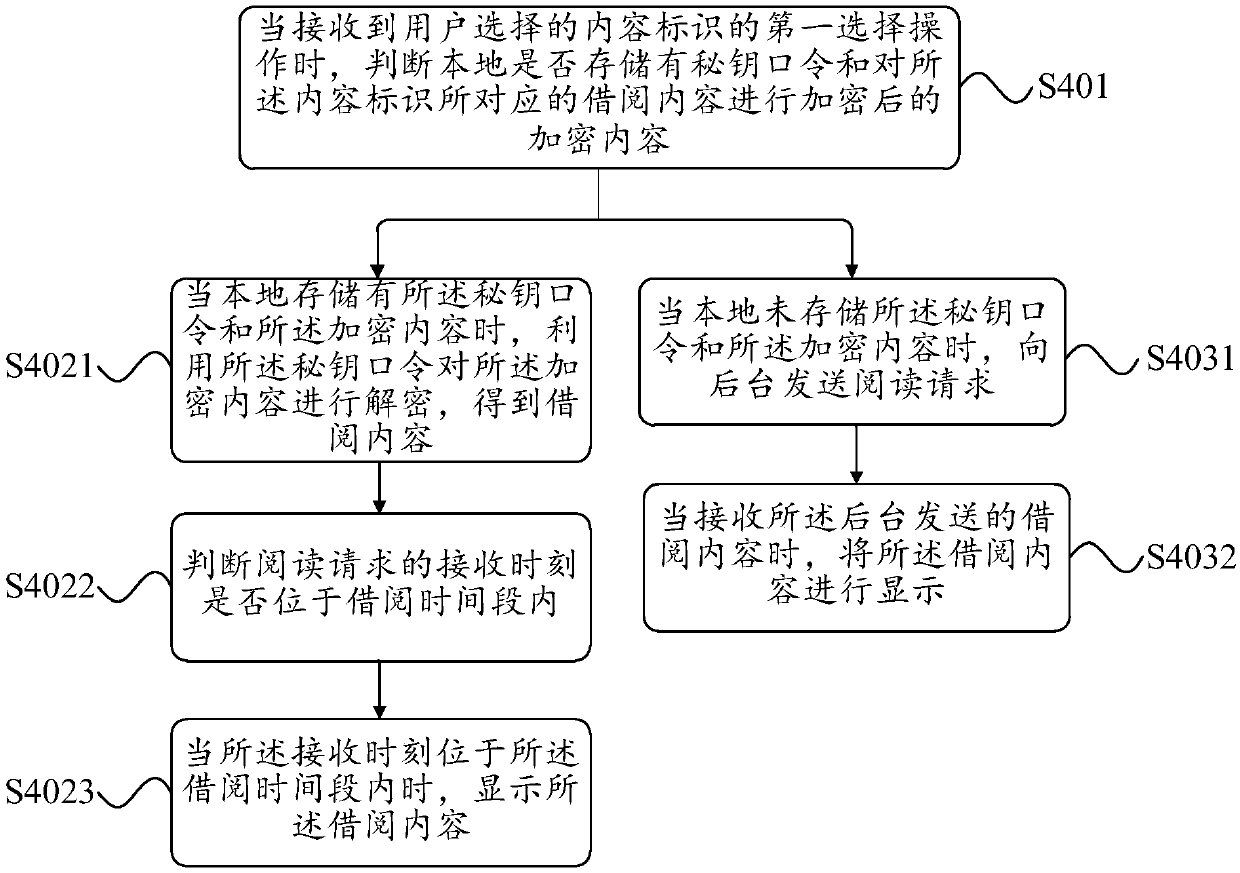
[0085] On the basis of the above-mentioned embodiments, another borrowing method disclosed in the embodiments of the present invention, the second device applied by the method includes a terminal, and the terminal includes all devices capable of accessing the Internet, such as mobile phones and tablet computers. image 3 A flow chart of another borrowing method provided by the embodiment of the present invention, which can realize the reading of borrowed content that has been successfully borrowed, such as image 3 As shown, the method includes the following steps.
[0086] S401. When receiving the first selection operation of the content ID selected by the user, determine whether the key password and the encrypted content of the borrowed content corresponding to the content ID are stored locally.
[0087] S4021. When the secret key password and the encrypted content are stored locally, decrypt the encrypted content by using the secret key password to obtain the borrowed conte...
Embodiment 3
[0101] On the basis of the above embodiments, in another embodiment of the present invention, a borrowing device is also provided, such as Figure 5 As shown, the device includes: a first acquisition module 11, a decryption module 12, a first judgment module 13 and a first sending module 14;
[0102] The receiving module 11 is configured to receive the request sent by the terminal.
[0103] The first obtaining module 12 is configured to obtain the key password according to the request information.
[0104] The first decryption module 13 is configured to use the key password to decrypt the encrypted content associated with the content identifier requested by the request information to obtain the borrowed content.
[0105] The first judging module 14 is configured to judge whether the receiving time in the request information is within the borrowing time period.
[0106] The first sending module 15 is configured to send the borrowed content to the terminal when the receiving t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com