A virtual machine memory forensics method for xenserver platform
A memory forensics and virtual machine technology, applied in the field of virtual machine memory forensics, can solve problems such as difficult memory analysis and complex operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0119] It should be pointed out that the following detailed description is exemplary and intended to provide further explanation to the present application. Unless defined otherwise, all technical and scientific terms used herein have the same meaning as commonly understood by one of ordinary skill in the art to which this application belongs.
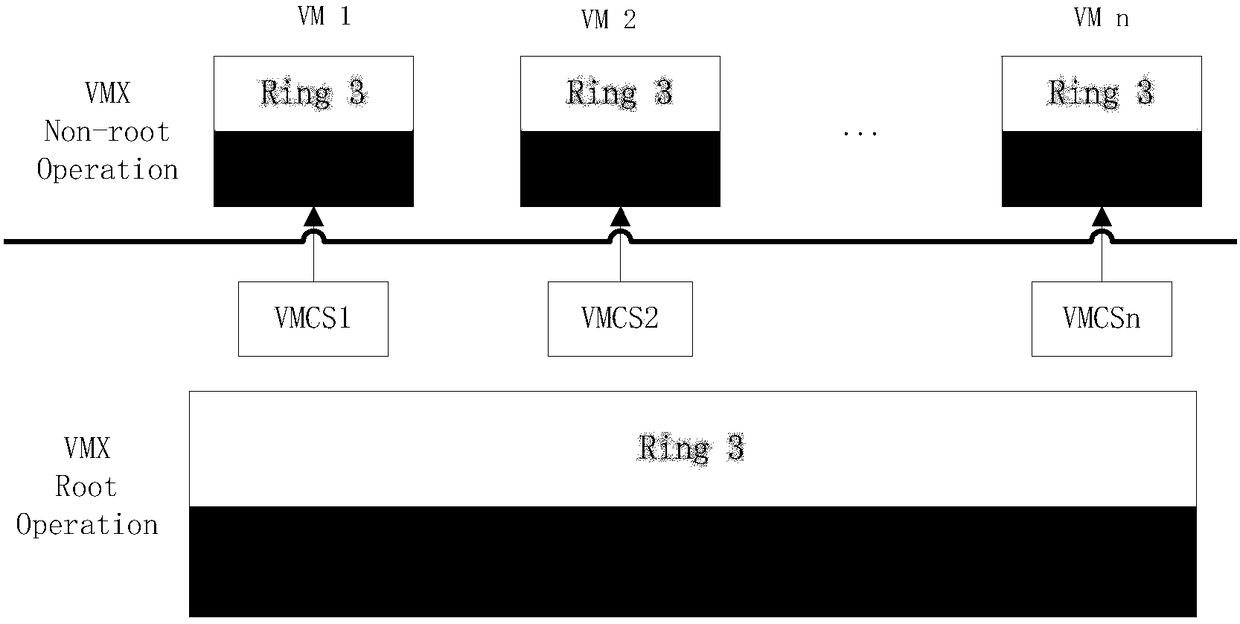
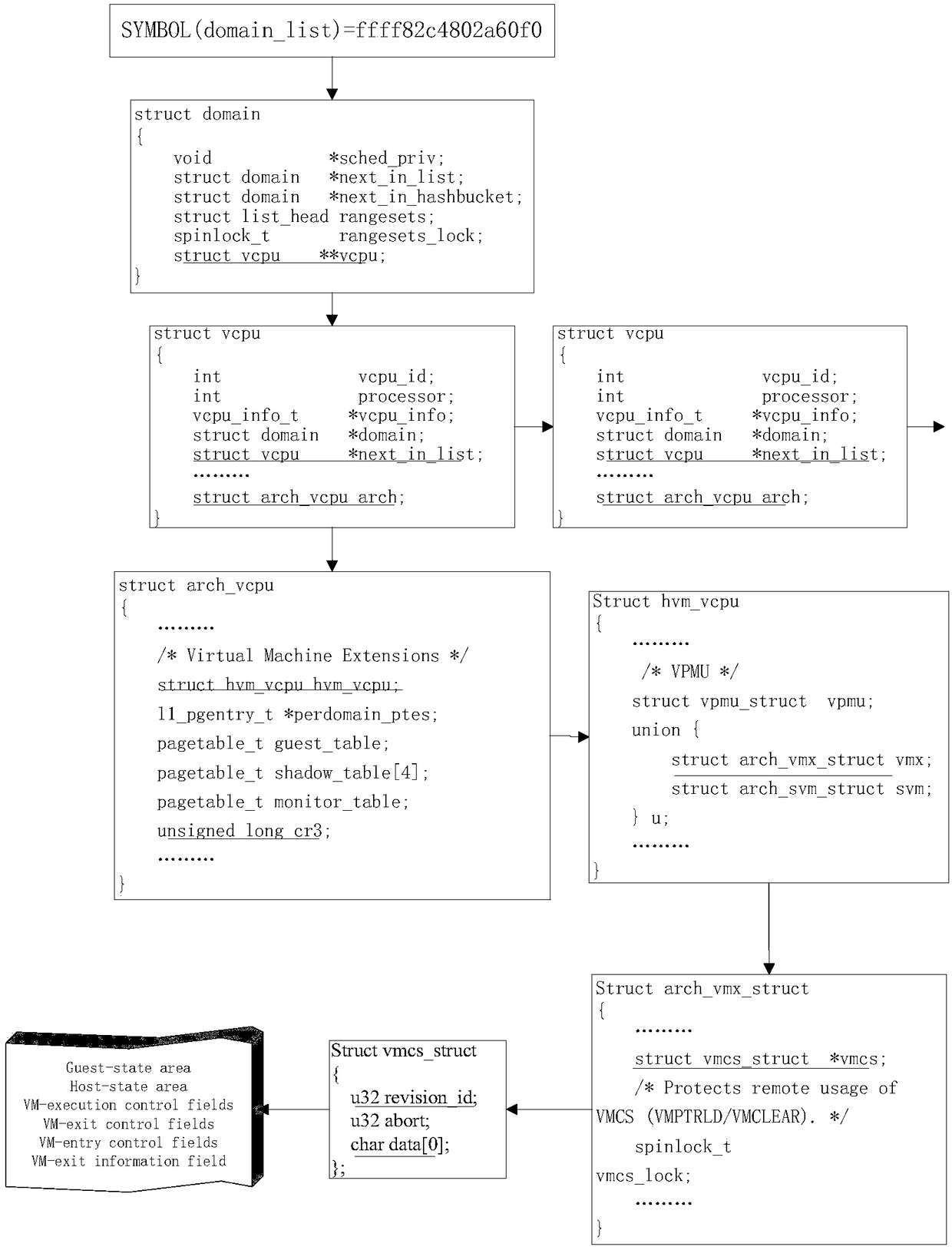
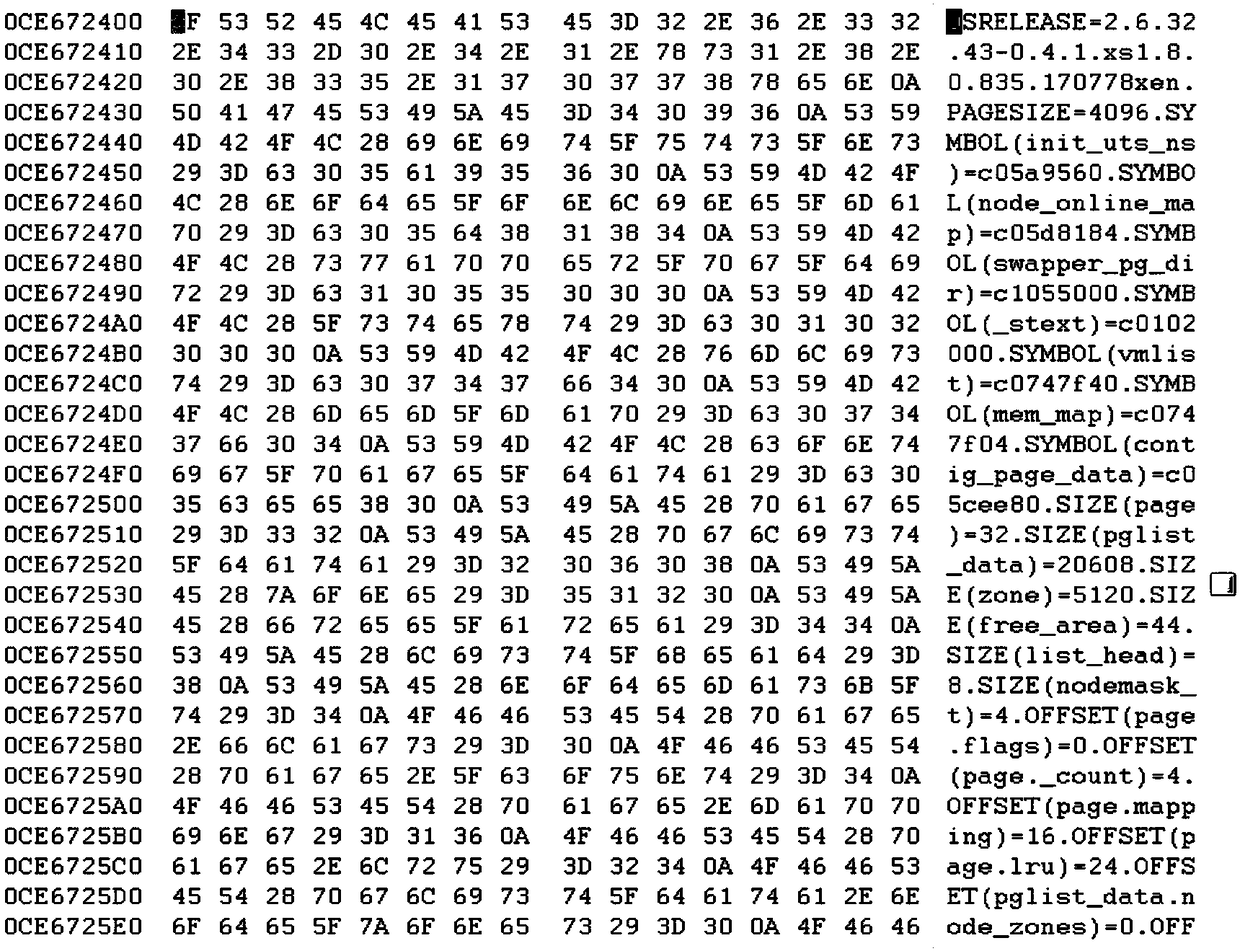
[0120] The concepts and technical terms involved mainly include virtual machines, XenServer, VMCS and EPT.
[0121] A virtual machine (Virtual Machine, VM) refers to multiple independent virtual hardware systems that are simulated on a hardware platform and have complete hardware system functions, running in a completely isolated environment, and can run on each virtual hardware system. Different operating systems, namely the guest operating system (Guest OS). These guest operating systems access actual physical resources through a virtual machine monitor (Virtual Machine Monitor, VMM). domain, interpreted as a domain in Chinese; vcp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com