Suspicious domain name detection method and device
A domain name detection and domain name technology, applied in the field of network security, can solve the problems of misclassification of normal domain names, difficulty in finding normal domain name samples and abnormal domain name sample sets, and inability to accurately identify abnormal domain names, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
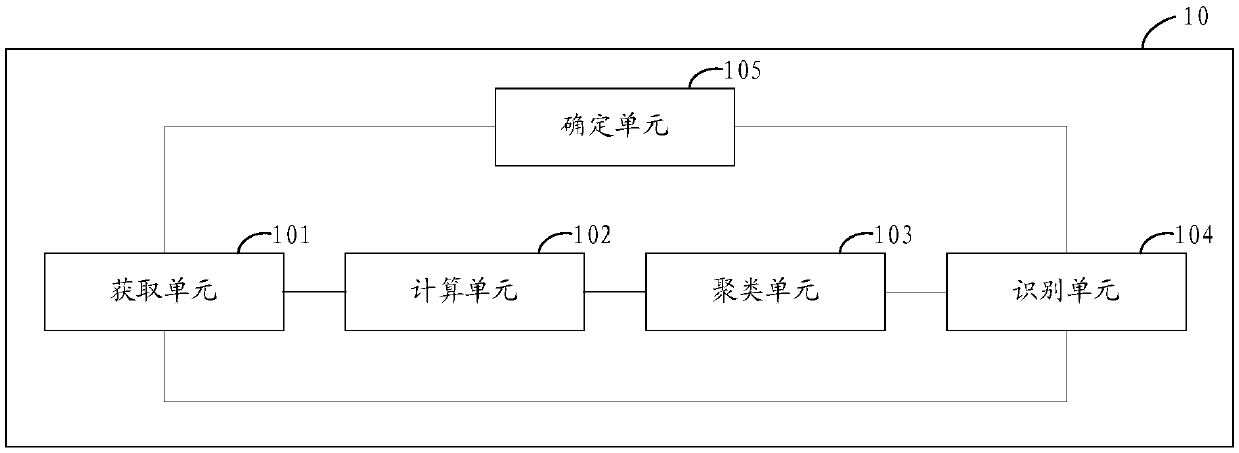
Image
Examples
Embodiment Construction
[0021] Embodiments of the present application are described below in conjunction with the accompanying drawings.
[0022] The embodiments of the present application are applied in the scenario of detecting the IP address corresponding to the suspicious domain name.
[0023] First of all, the description of the technical data used in the embodiments of this application is as follows:
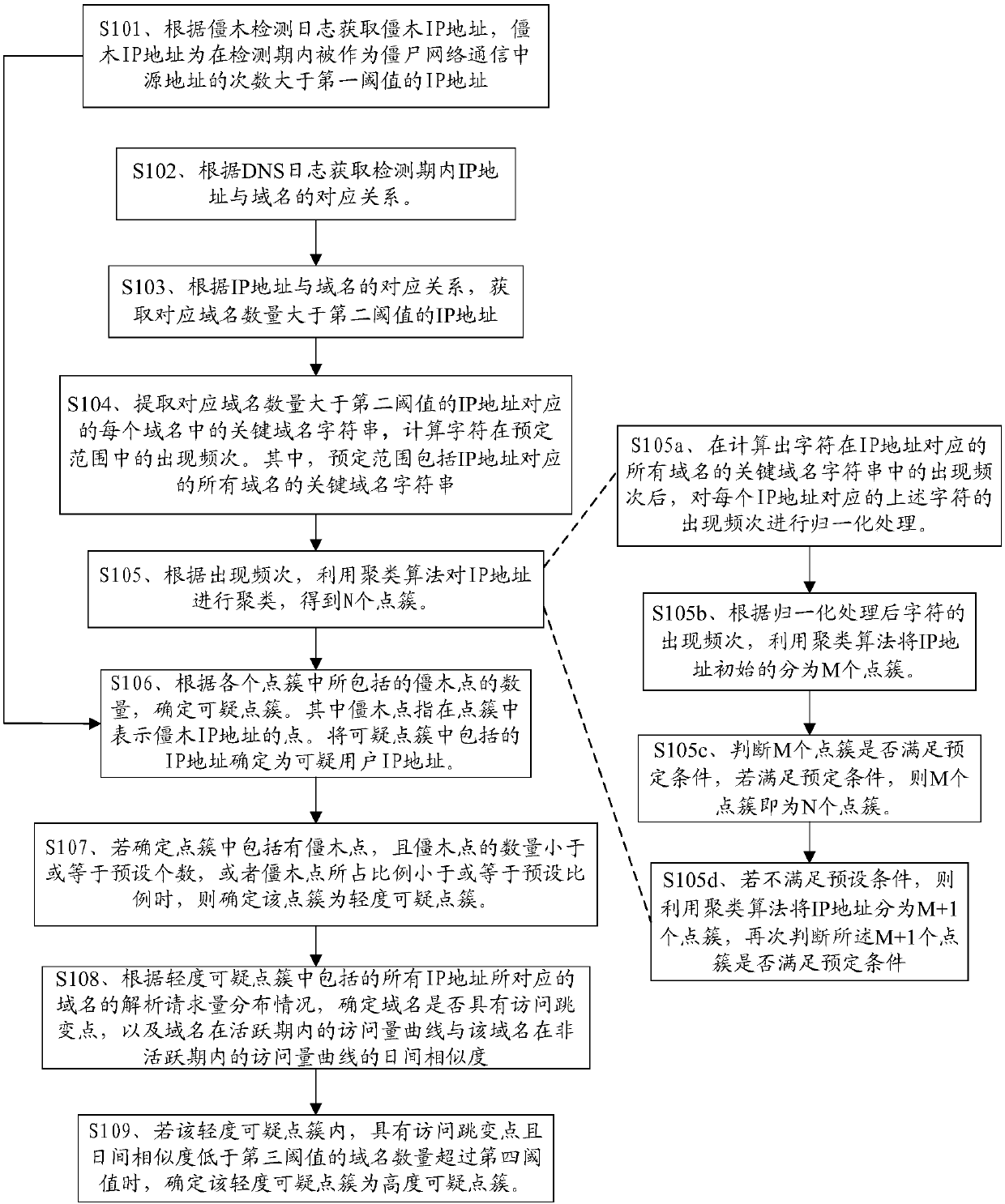
[0024] At present, in botnets and malicious software, in order to keep the communication between the controlled terminal program and the control terminal site in sync, the domain name conversion technology based on the DGA algorithm is widely used. Specifically, the controlled end and the botnet control end adopt the same domain name generation strategy, constantly register and use new domain names (for example, change and use new domain names every day) to evade detection, and the controller preempts these maliciously generated domain names in advance.
[0025] These domain names based on domai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com