Security and protection monitoring method, electronic device and computer readable storage medium
A technology for security monitoring and electronic equipment, applied in the field of electronic equipment and computer-readable storage media, security monitoring, can solve the problems of large limitations and poor security of security monitoring, and achieve the effect of avoiding leakage of privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
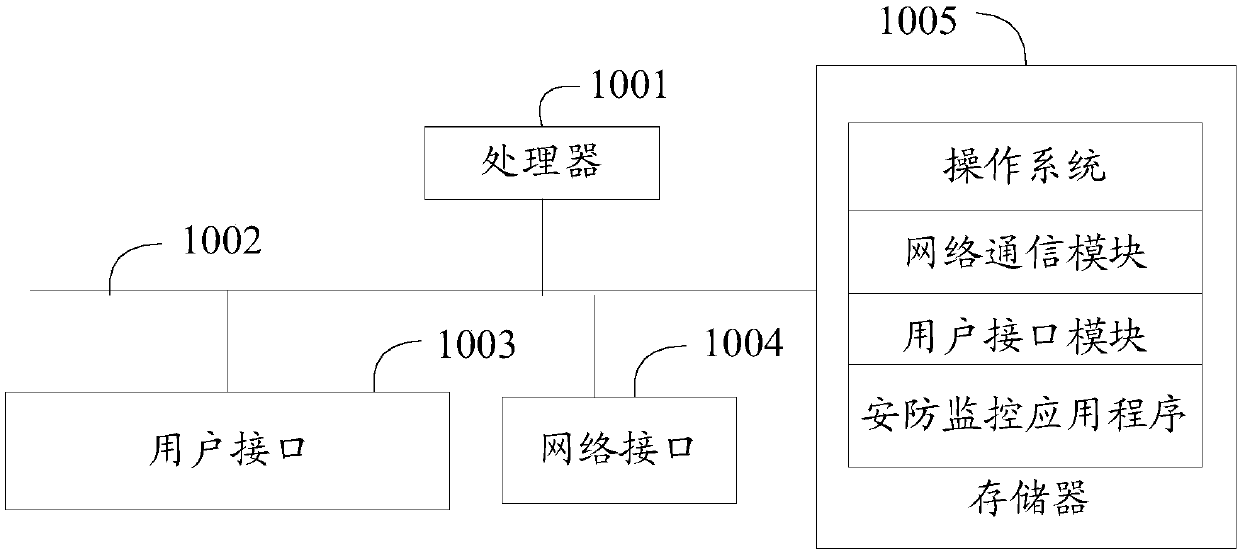
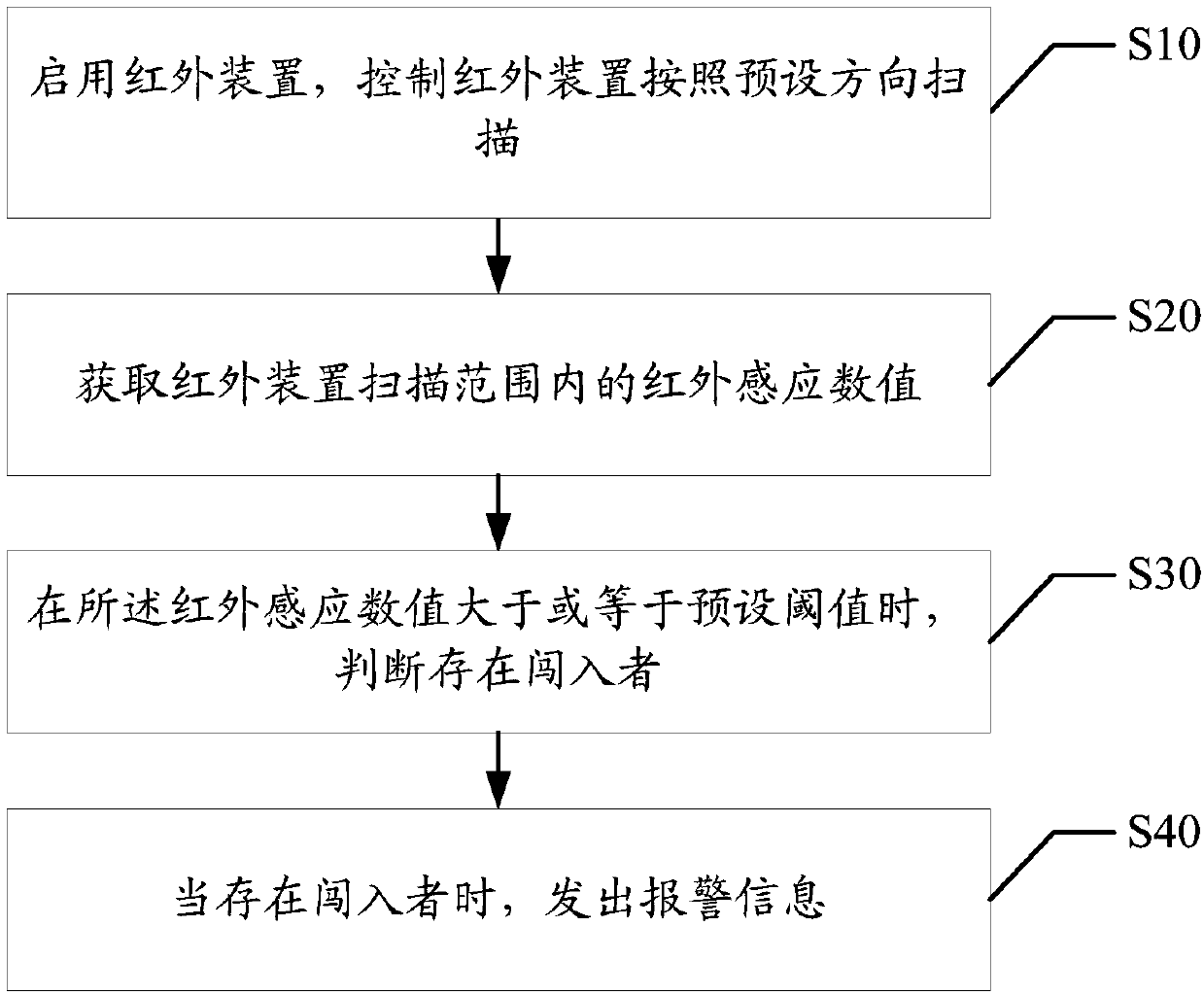
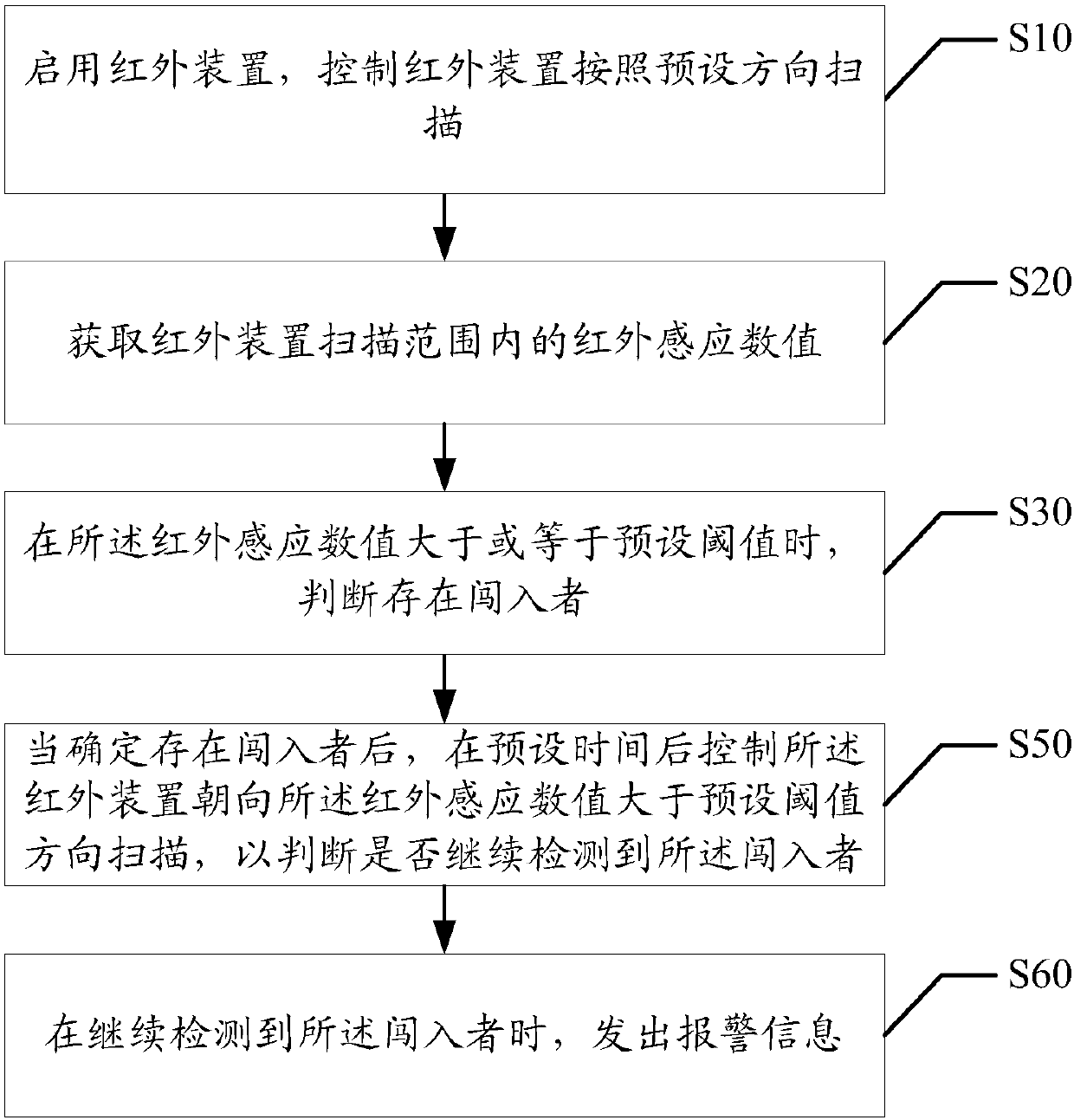
[0046] The main solution of the embodiment of the present invention is: enable the infrared device, control the infrared device to scan according to the preset direction; obtain the infrared sensing value within the scanning range of the infrared device; Intruder; when there is an intruder, an alarm message will be sent.
[0047] Most of the current security monitoring is video monitoring, but video monitoring involves the leakage of privacy, which makes security monitoring unsafe and easy to leak privacy. Based on the above problems, the present invention performs security protection through infrared means, scans the environment according to the infrared device, obtains the thermal induction value after the infrared device scans, and judges that there is an intruder when the value is greater than or equal to the pres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com