Patents
Literature
30results about How to "Protect privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method to enable tracking of consumer behavior and activity
InactiveUS20100313009A1Protect privacyEnsuring user privacyMarket predictionsDigital computer detailsMessage passingTraffic volume
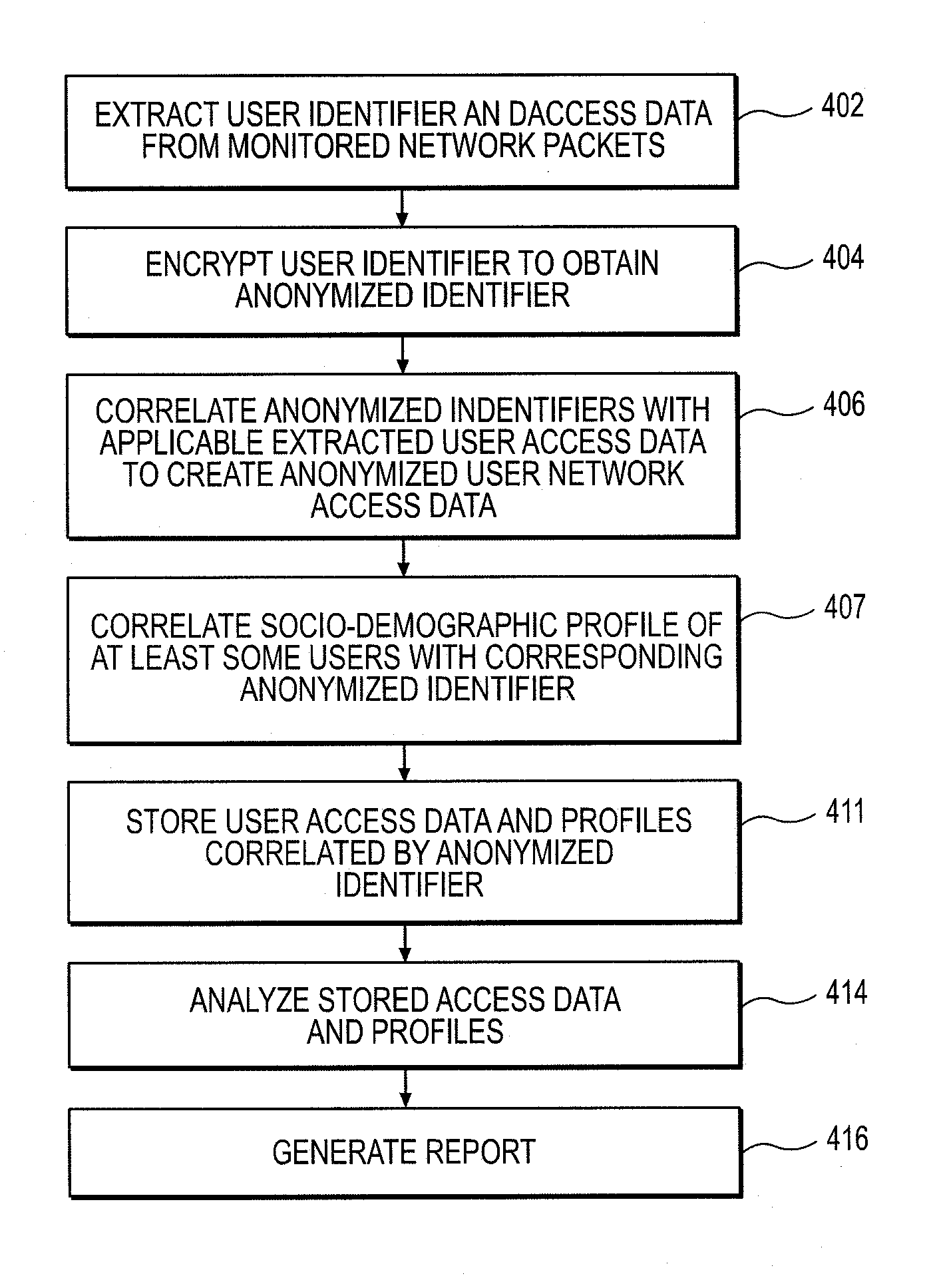
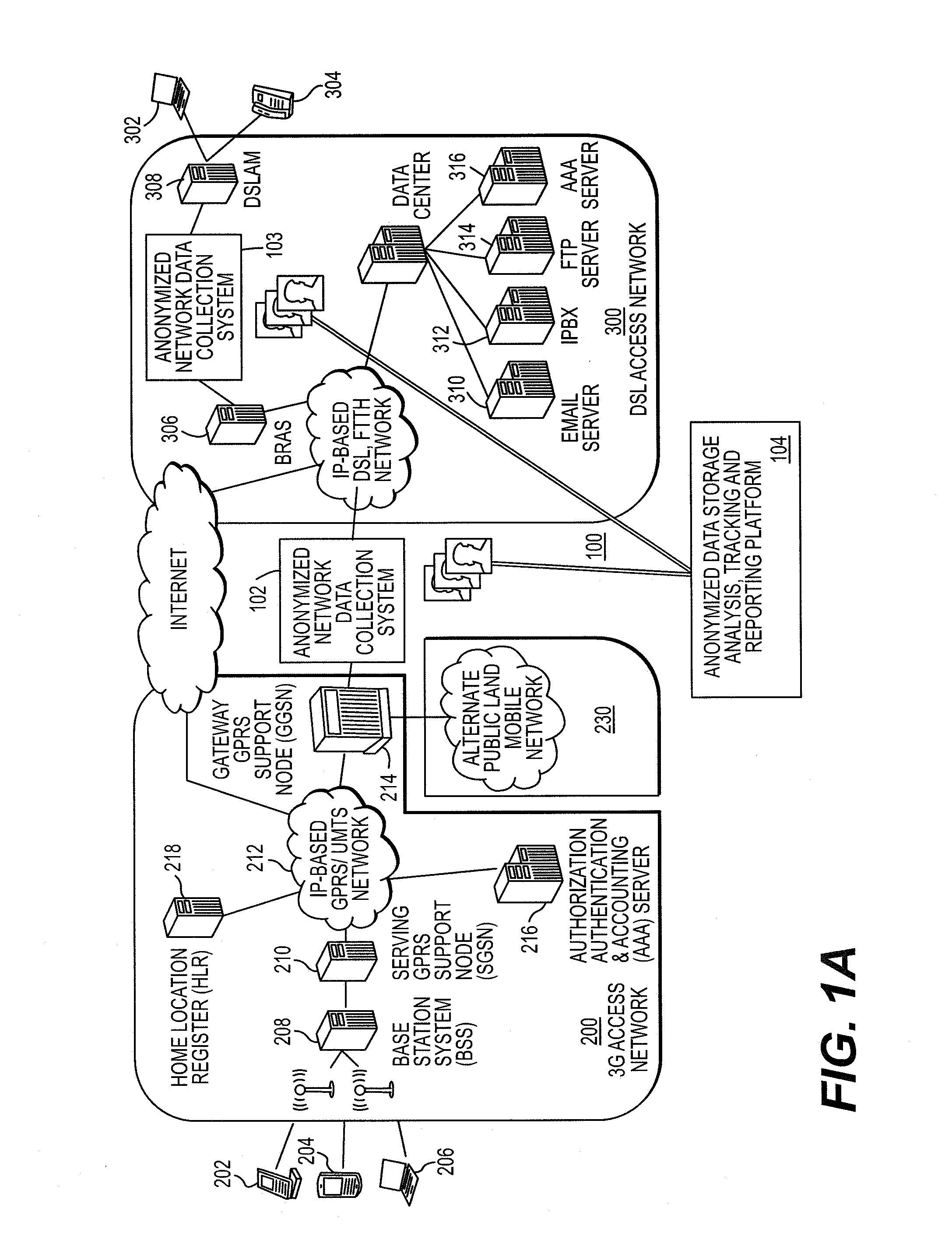
A method for collecting, processing and analyzing Internet and e-commerce data accessed by users of messaging devices such, for example, as mobile terminal users includes receiving network access data extracted from packetized traffic of a communication system. A portion of the extracted network access data is encrypted to anonymize the received network access data, obscuring information from which messaging device users' identities might otherwise be determined. The encrypted portion constitutes a unique, anonymized identifier that can be correlated to the messaging device user associated with the traffic. Network access data anonymized in this manner, once received, is processed for analysis. By referencing the identifier, anonymized network access data associated with any messaging device user is distinguishuable from anonymized network access data associated with all other messaging device user—allowing patterns of internet access activity of the users to be tracked and reported anonymously. By correlating the identifier to a socio-demographic profile, it is further possible to monitor a sample of users sufficiently large to represent an entire population sharing the same socio-demographic characteristic(s).
Owner:COMBET JACQUES +1
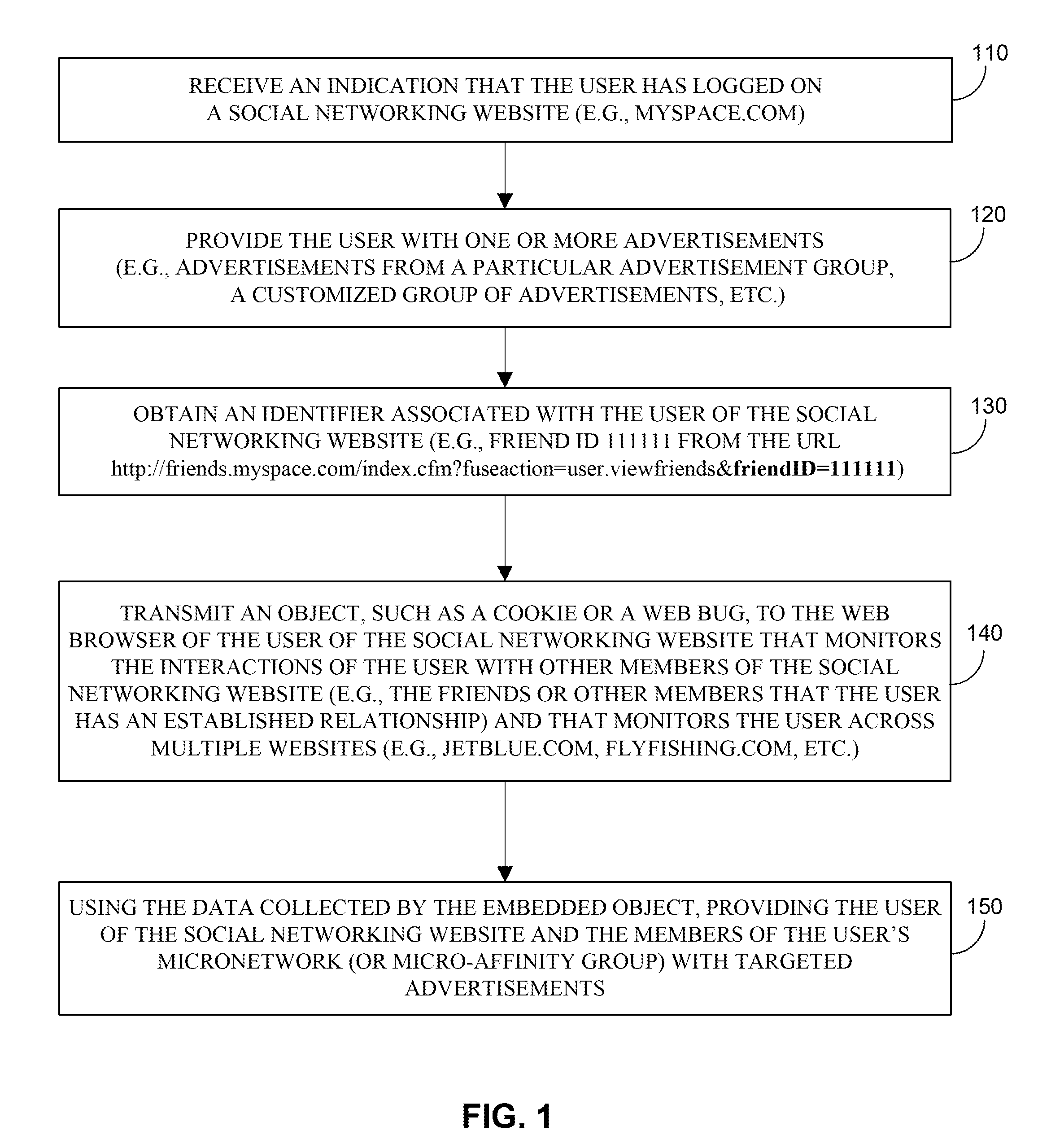
Systems and methods for targeting online advertisements using data derived from social networks
InactiveUS20110041168A1Protect privacyDigital data processing detailsUser identity/authority verificationUnique identifierInformation transfer
Systems and methods for targeting online advertisements using data derived from social networks are provided. In accordance with some embodiments, the method comprises: presenting a user at a user computer with a publicly accessible website that includes user-generated social networking content over the Internet, wherein the user is authorized to access features and the user-generated social networking content associated with the publicly accessible website upon inputting user information; in response to receiving user information from the user, displaying a webpage associated with the user; displaying at least one advertisement on the webpage, wherein the at least one advertisement embeds an object in the user computer and wherein the object is used to obtain a unique identifier associated with the user; using the object to construct a micronetwork of the members associated with the user, wherein the object obtains the unique identifier from each member that visits the webpage and the unique identifier from each member that establishes a relationship with the user; using the object to monitor information relating to the user, wherein the information includes actions executed by the user; retargeting advertisements for transmission to the user and the micronetwork based on information monitored by the object; and transmitting at least one retargeted advertisement to the user and the micronetwork associated with the user, wherein the at least one retargeted advertisement is transmitted using the unique identifier associated with the user and the unique identifier associated with each member of the micronetwork.
Owner:DSTILLERY
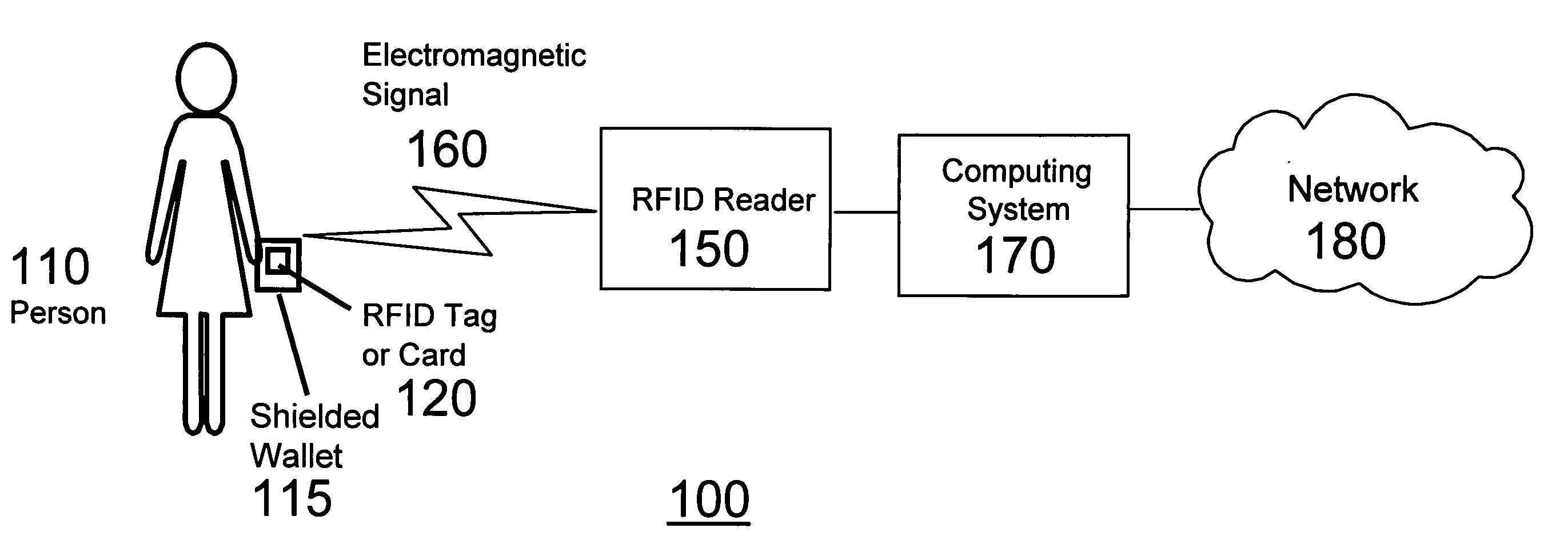
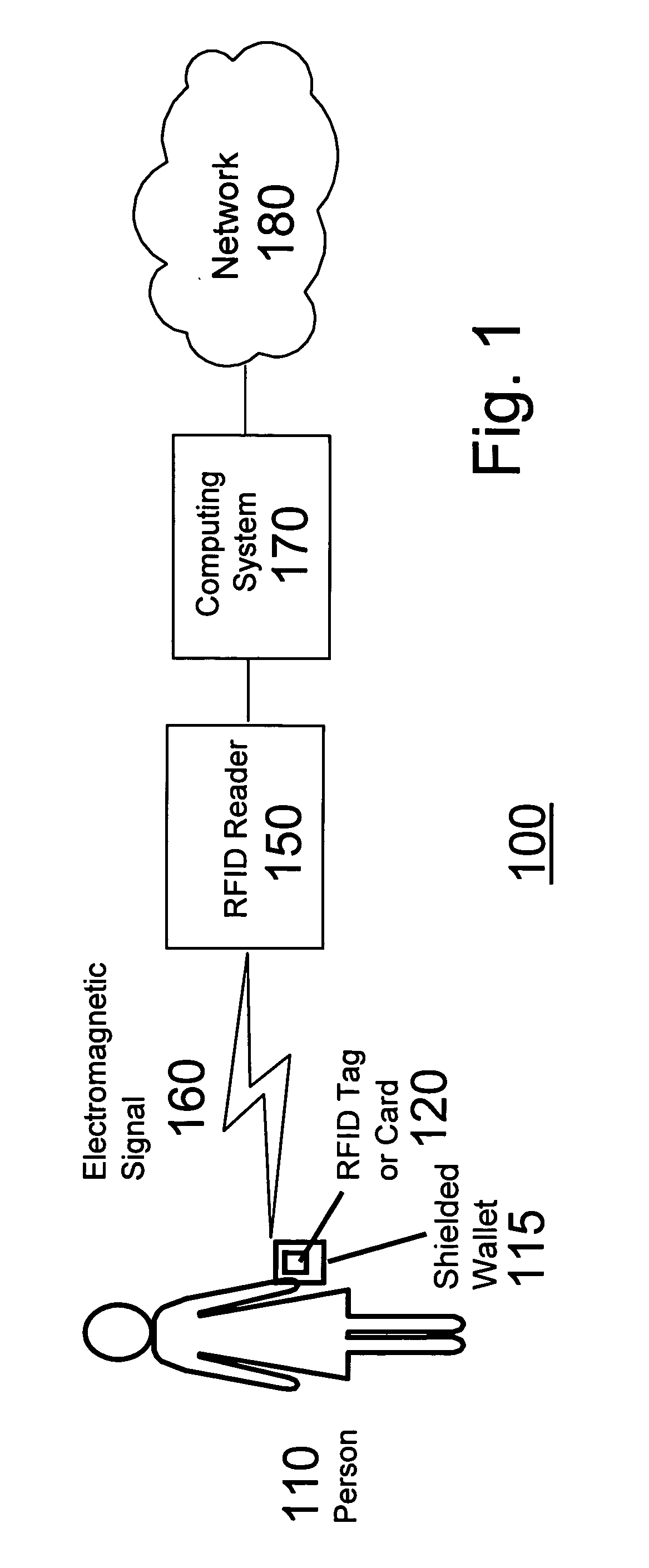
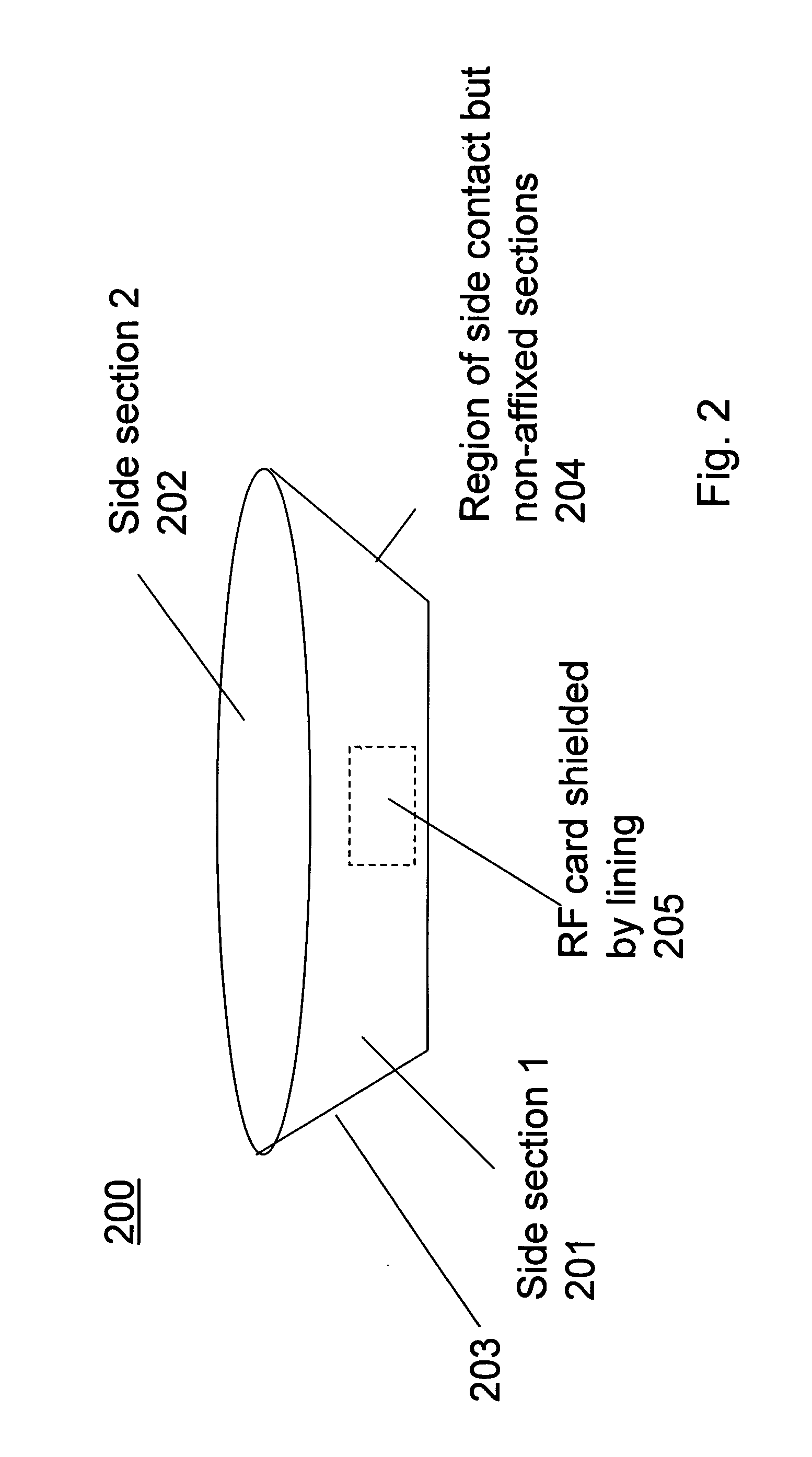
Shielding wireless transponders
InactiveUS20060044206A1Protect privacyPrivacy protectionAntenna supports/mountingsAntenna couplingsElectronic informationElectronic circuit
Provides protection to wireless portable transponders from an unauthorized interrogation by employing a mechanical member. Transponders include: cards, fobs and RFID tags that a persons may carry. Such transponders generally have means for receiving and storing electronic and other information, commonly in binary form using memories as in electronic circuits, etc. The invention is designed to provide privacy of electronic information and yet permit the information to be queried at the users discretion. The cards and tags can be protected from receiving or providing unauthorized or unwanted information. The invention provides a standard carrying case with radio wave shielding means that permit the owner to decide when reception / interrogation of personal or other information is desirable by placing the cards, fobs and RFID tags within the shielded region.
Owner:LENOVO (SINGAPORE) PTE LTD
Medical data storage server
InactiveUS20110161112A1Maintain privacyProtect privacyData processing applicationsMedical imagesAuthorizationMedical procedure
Provided is a method of documenting a medical procedure including receiving medical data captured during the medical procedure to be documented. Information indicative of an identity of at least one of a patient that is a subject of the medical procedure and a physician involved with the medical procedure is received. The medical data is stored in a non-transitory computer readable medium associated with the at least one of the patient and the physician. Access to the medical data stored on the computer readable medium is restricted, allowing the physician involved with the medical procedure to subsequently retrieve the medical data stored in the computer readable medium and view the medical data retrieved. Restricting access to the recorded medical data prevents another physician, who may not have been involved in the medical procedure, from viewing the medical data without first entering information indicative of authorization to view the medical data.
Owner:CODONICS
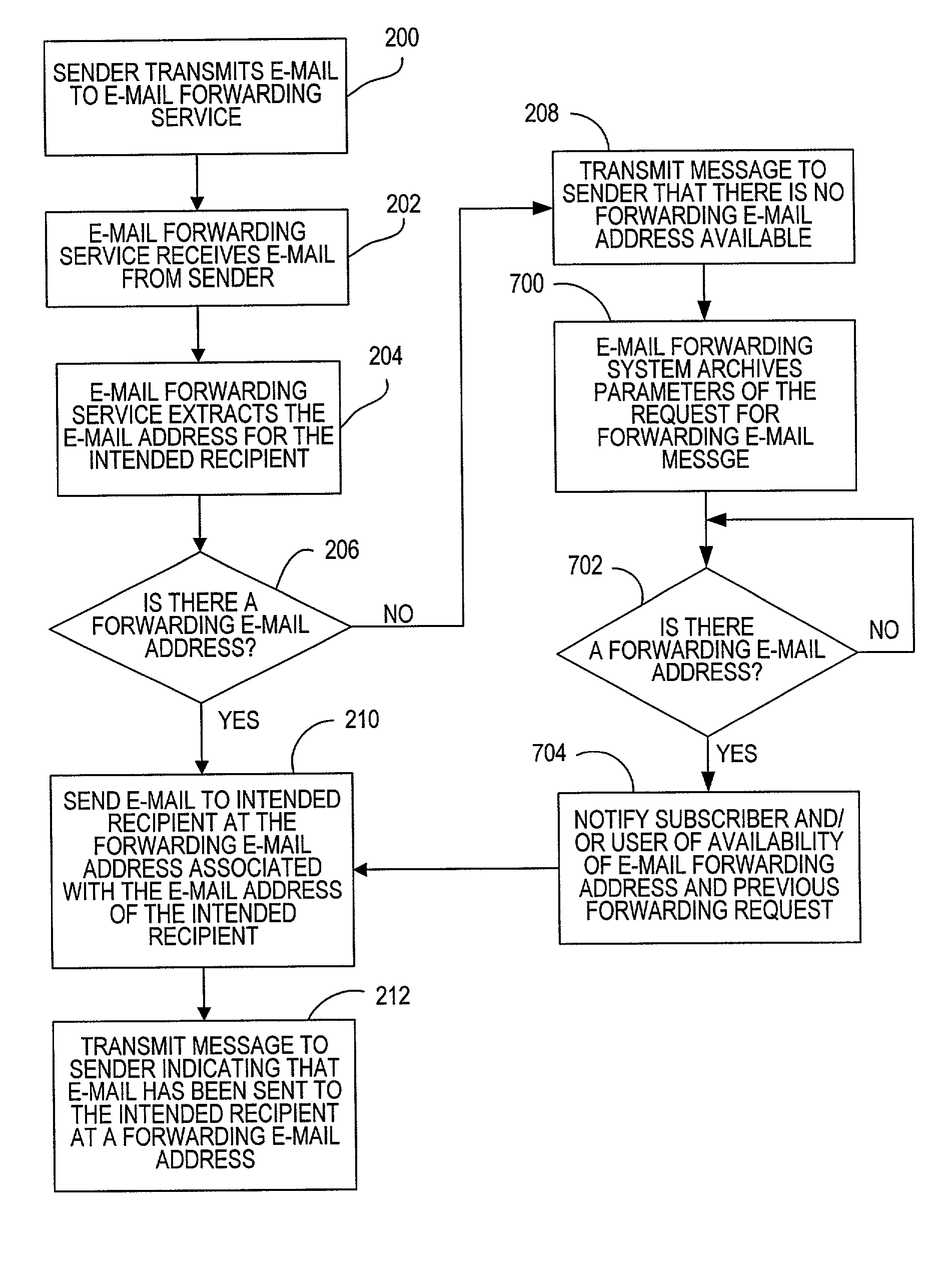
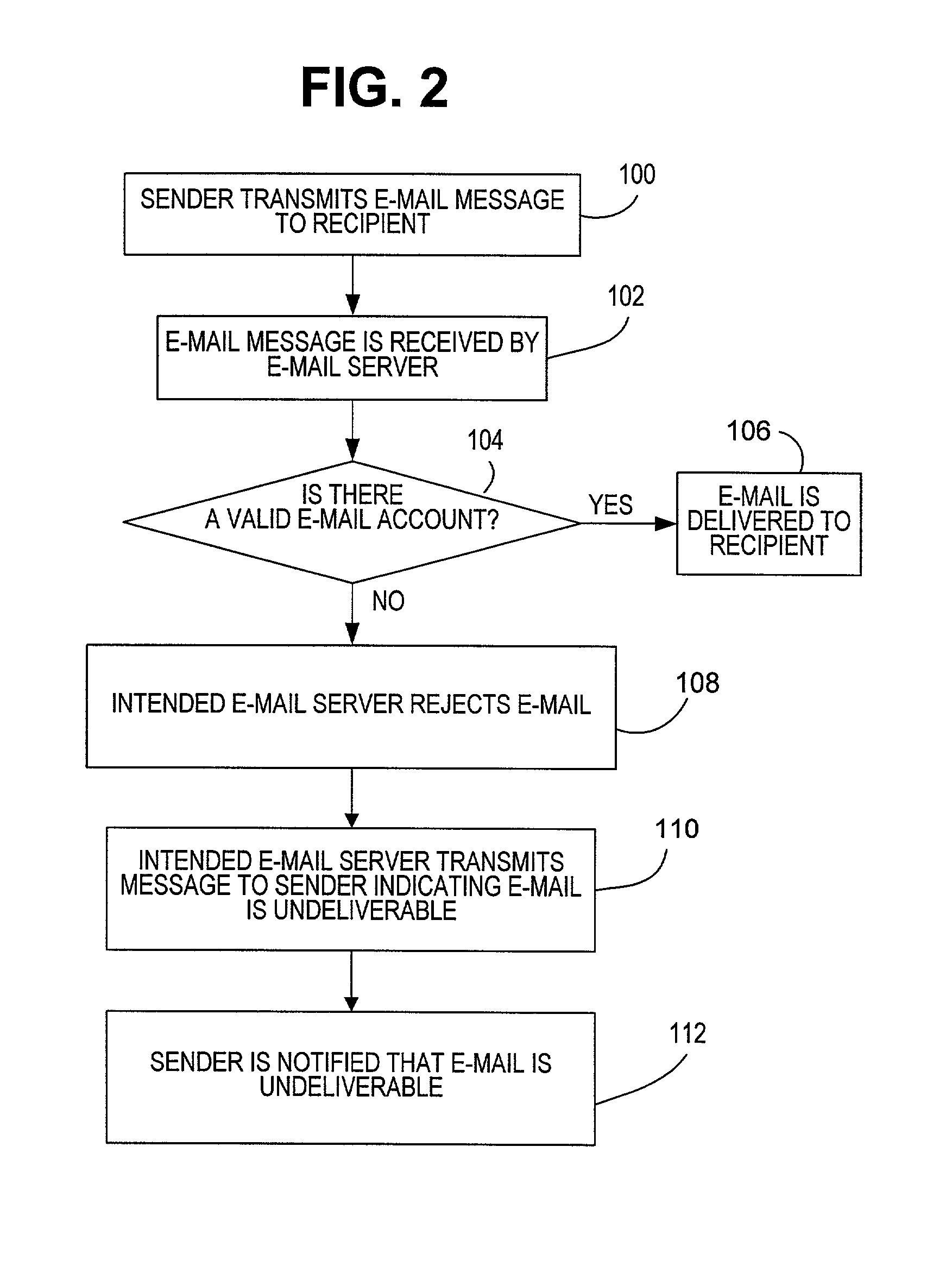
Method for providing address change notification in an electronic message forwarding system
ActiveUS6988129B2Enhance functionalityProtect privacyMultiple digital computer combinationsElectronic credentialsInternet privacyElectronic mail
A method and system for providing address change notification in an e-mail forwarding system by providing a pre-generated e-mail address change notification to recipients selected during registration in the e-mail forwarding system. The e-mail forwarding system operating when a message is received at an e-mail forwarding computer, the message identifying the first disfavored e-mail address. The e-mail forwarding computer parses the first e-mail address from the message to determine if there is a second preferred forwarding e-mail address associated with the first e-mail address. If there is a second e-mail address associated with the first e-mail address, the e-mail forwarding computer sends the e-mail message to a third computer associated with the second e-mail address.
Owner:CUFER ASSET LTD LLC
System and methods of location based service for people interaction
InactiveUS20130316735A1Avoid embarrassmentProtect privacyServices signallingLocation information based serviceUser privacyLocation-based service
System and methods for location based service for people interaction are disclosed. The system and methods allow people not only to connect to their known friends and contacts but also to meet those people unknown or unfamiliar. Direct and intrinsic users' interests can be discovered, categorized and aggregated during daily lives of users and used to improve users' social lives. Additional methods to guard and protect user privacies are also disclosed.
Owner:LI DAN +1
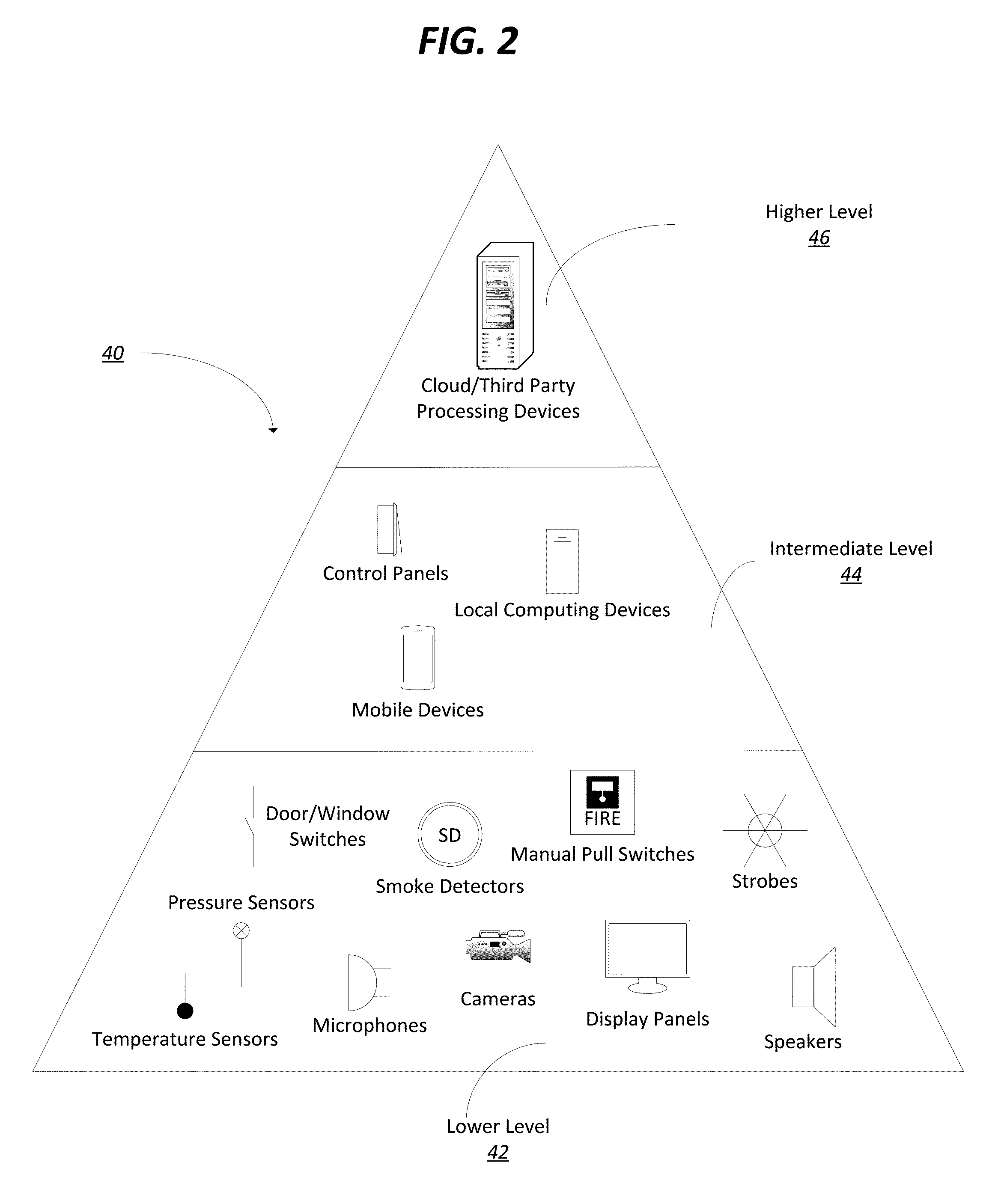
Intelligent smoke sensor with audio-video verification
ActiveUS20160133108A1Protect privacyReduce occurrenceNetwork connectionsFire alarm smoke/gas actuationProcess systemsAudio frequency
A method and system architecture for automation and alarm systems is provided. An intelligent fire detection sensor is provided that provides input data to a gateway device for processing and facilitates two-way communication with users and a third-party monitoring service. The system architecture is hierarchically organized, allowing devices to process system data differently at different levels of the hierarchy. Processing of at least some of the sensor data is overseen by the gateway device, which may determine, based on the processing, to activate one or more secondary sensors at the fire detector (such as an optical camera). The gateway device and fire detection sensor may interact cooperatively to process voice commands and / or gesture data, and to recognize false alarms.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
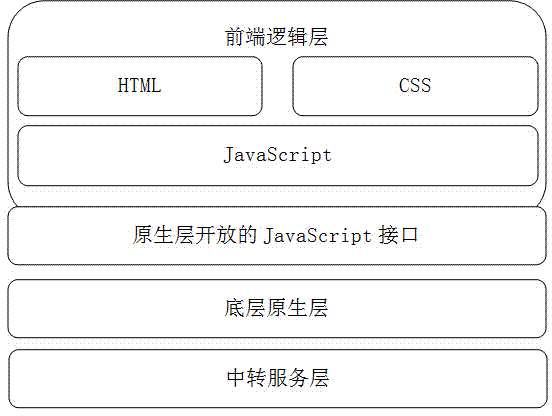
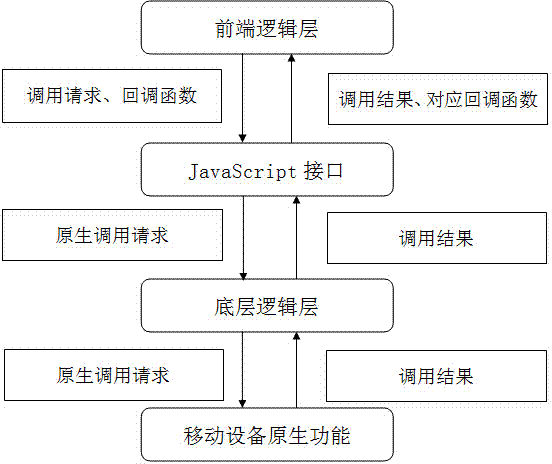
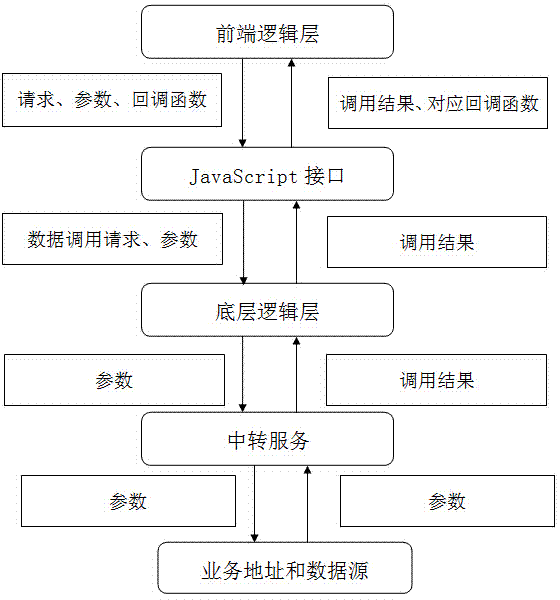
Cross-platform mobile application development framework system based on general-purpose module and transfer service
InactiveCN104239071AProtect privacyProtection securityTransmissionSpecific program execution arrangementsGeneral purposeSoftware engineering
The invention discloses a cross-platform mobile application development framework system based on a general-purpose module and a transfer service, and belongs to the field of the mobile Internet. The framework system is mainly composed of a front-end logical layer, a bottom-layer primary layer and a service transfer layer. The front-end logical layer realizes cross-platform application development through components composed of HTML, CSS and JavaScript, and calls the primary function of a mobile phone in cooperation with an open JavaScript interface of the bottom-layer primary layer. The bottom-layer primary layer is an open JavaScript interface of a front-end component gallery so that the primary function of the mobile phone can be called and a service address can be protected through the service transfer layer. The service transfer layer protects the backstage service address through transfer and distribution and realizes switchover of a test environment and a formal environment through configuration. Compared with the prior art, the development framework system can solve the problems that a developer can not freely carry out extension and the backstage service address and a data source are exposed, and is high in application and popularization value.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
Non-contact type safety card
InactiveCN1414516AProtect privacyControl autonomyRecord carriers used with machinesEngineeringElectrical and Electronics engineering
The safety card includes IC chip, antenna coil. The IC chip through the connection wire is connected to the antenna coil. The circuit of the ratio frequency card composed of the IC chip, the connection wire and the antenna coil is encapsulated in the plastic card. The character is that the switch is installed in the connection wire between the IC chip and the antenna coil. Thus, the card owner keeps the decision-making power whether the information contained in the card is allowed to output so as to protecting the private information.
Owner:商庆海
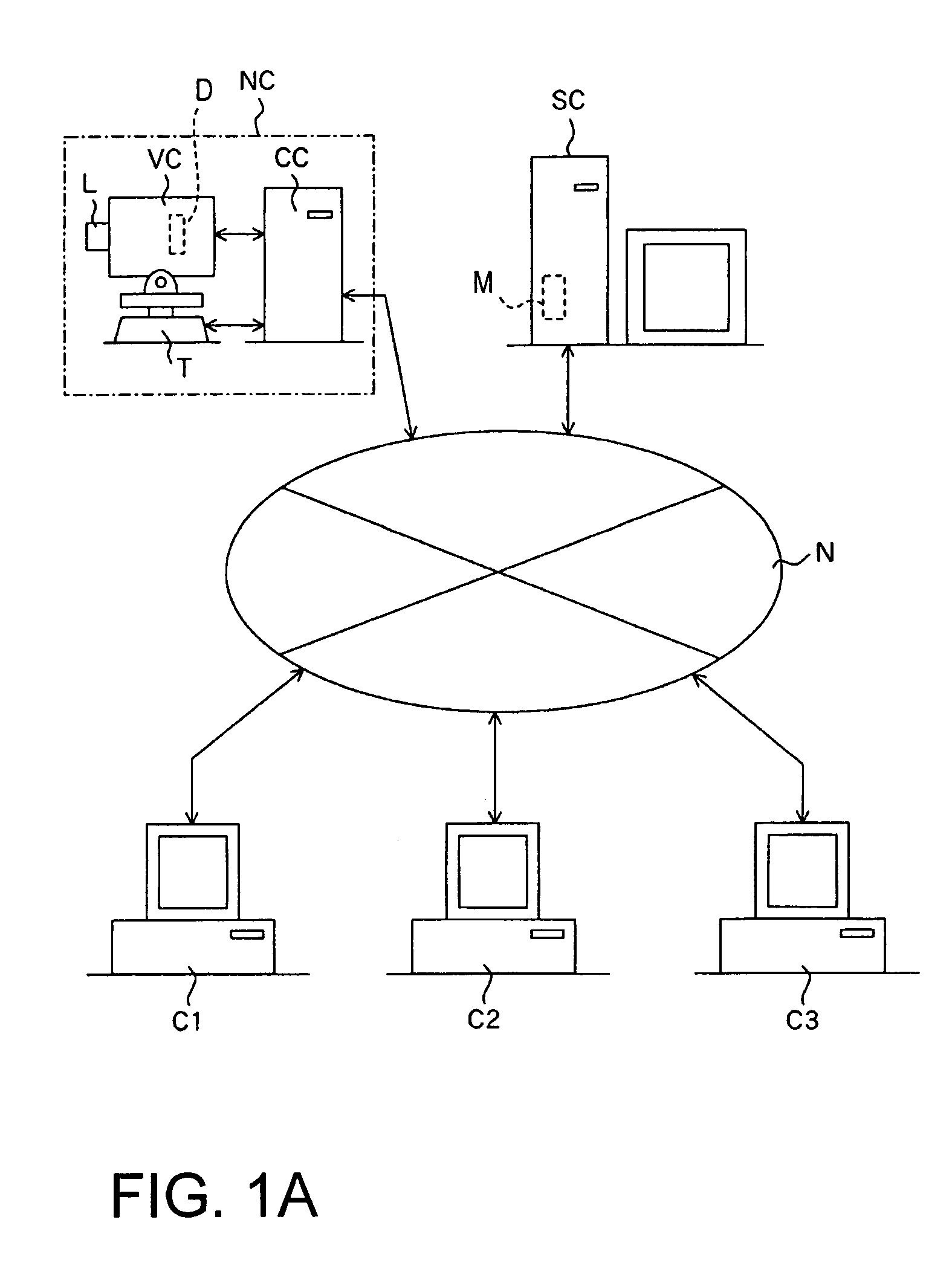
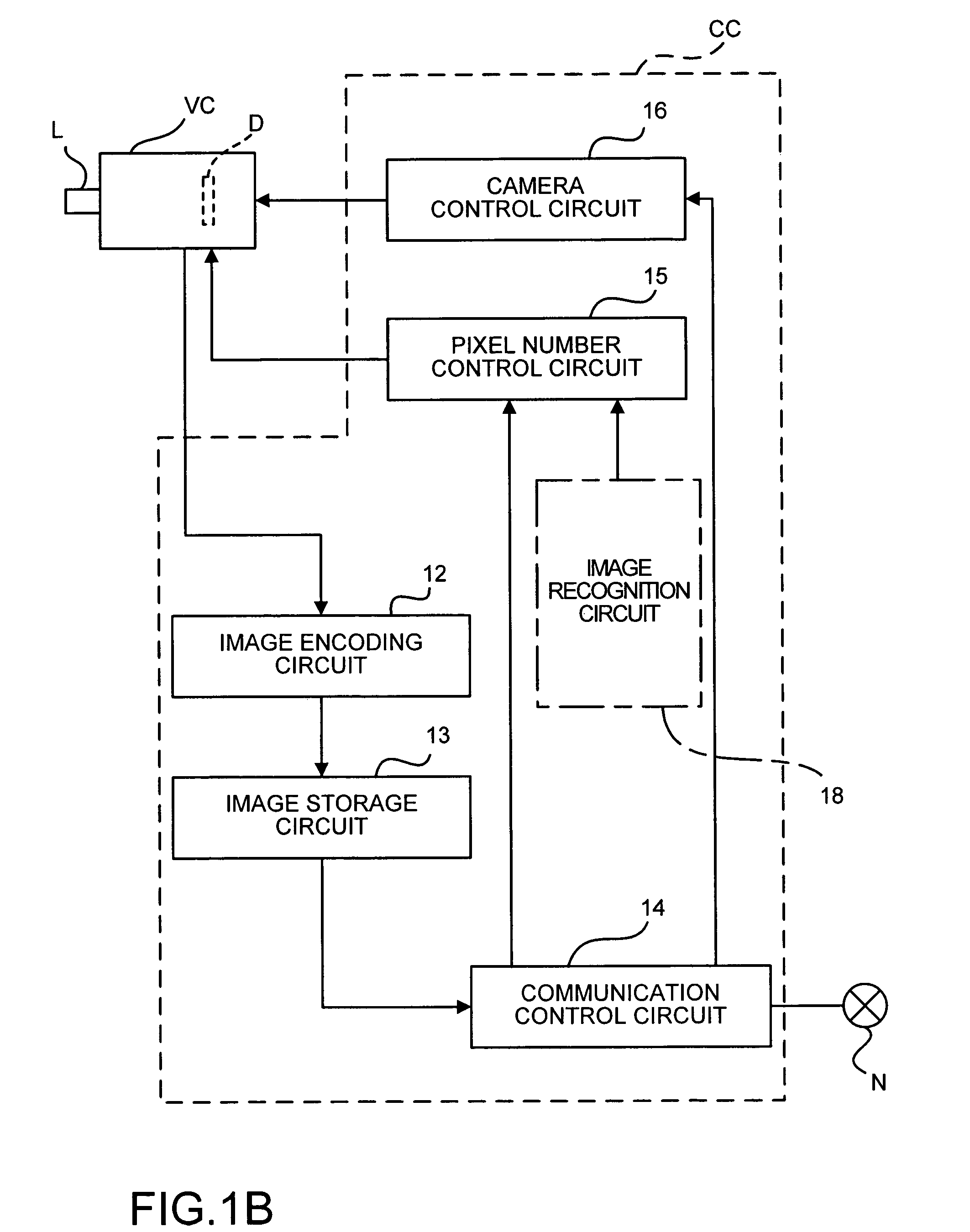
Image-taking apparatus capable of distributing taken images over network
ActiveUS7283161B2Prevent distributionProtect privacyTelevision system detailsPicture signal generatorsFrame rateComputer graphics (images)
An image-taking apparatus and an image-taking system are disclosed which can protect the privacy of a person whose image is taken, and which can avoid the distribution of images of unnecessarily large data volumes. The image-taking apparatus includes an image-taking optical system, an image-pickup device, a controller which performs, by using the image-pickup device, image-taking in a first mode and in a second mode in which image-taking is carried out with more pixels or at a lower frame rate than in the first mode. The controller determines whether a condition relating to image-taking matches a predetermined restriction condition, and restricts image-taking in the second mode or distribution of an image taken in the second mode when that restriction condition is met.
Owner:CANON KK
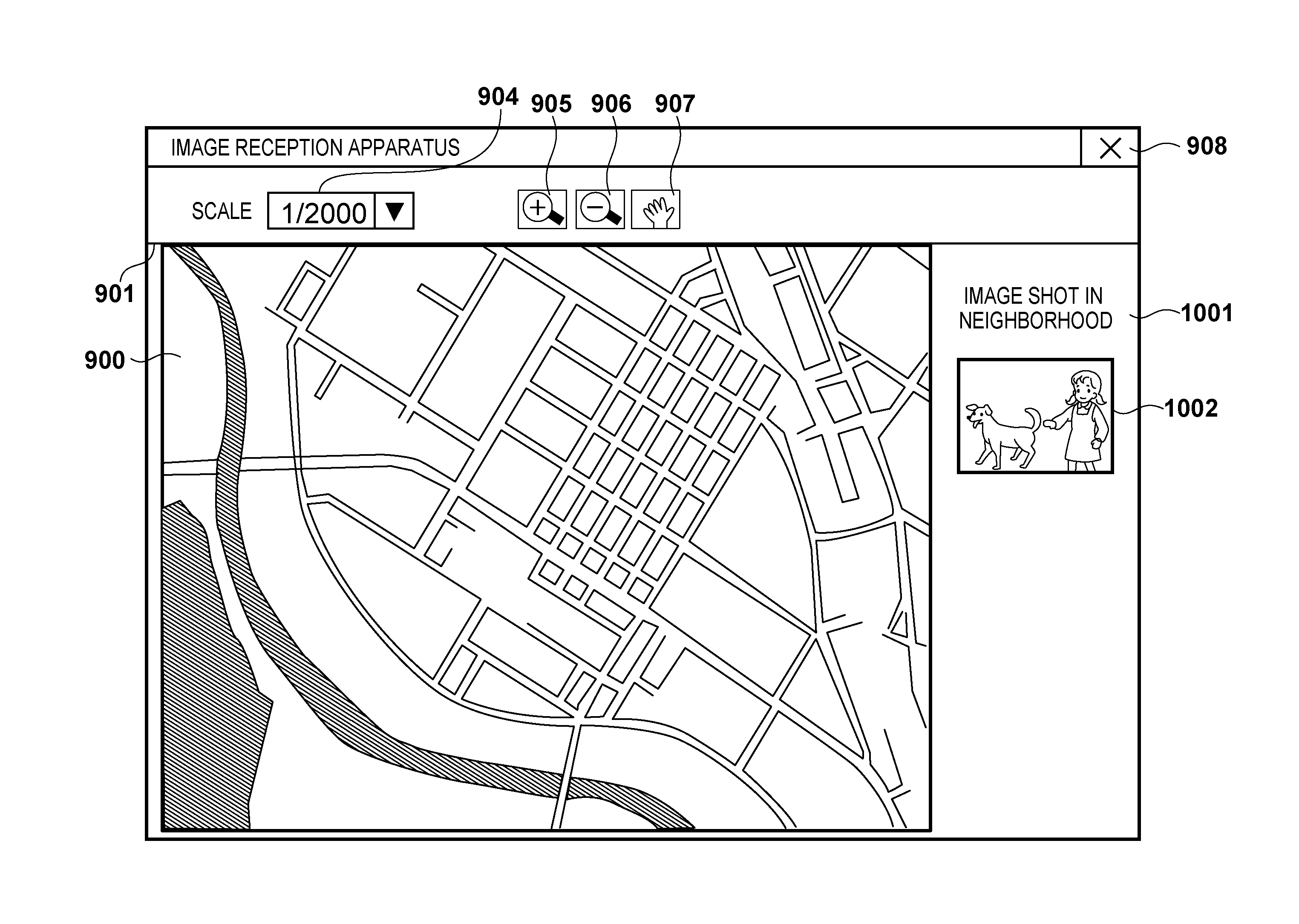
Image control apparatus, server and control method therefor
ActiveUS20120154418A1Protect privacyCathode-ray tube indicatorsNavigation instrumentsControl equipmentComputer graphics (images)
An image control apparatus wherein an acquisition unit acquires position information from attribute information of the image, a setting unit sets a display scale of a map when displaying the image on the map, and a generation unit generates display data for displaying the map and the image on a display device using the acquired position information and the set display scale, when the set display scale is lower than a predetermined display scale, the generation unit generates display data in which the image is laid out at a position corresponding to the position information on the map, and when the display scale is higher than the predetermined display scale, the generation unit generates display data in which the image and the map are laid out without laying out the image on the map.
Owner:CANON KK
Family Internet of things security control method based on CPK
ActiveCN105282179AProtection securityProtect privacyUser identity/authority verificationAuthenticated encryptionService information
The invention discloses a family Internet of things security control method based on a CPK, which relates to the security technology field in the family Internet of things. Based on the security mechanism of CPK, an ID certification module that is needed is generated through a CA certification center; the verification of legality to a device between different devices of a system is finished through verification information and signature provided by the ID certification module and signature verification methods; the exchange of secret keys is finished through key exchanging information and a private key and a public key that are provided by the ID certification module; and lastly, the transmission, the encryption and the decryption of service information are finished through coding data information and a coding method provided by the ID certification module, thereby finishing the security control function of the internal service data of the family Internet of things. According to the invention, the verifying coding method of CPK is applied in the method, thereby effectively ensuring the security of the internal data of the family Internet of things and the legality of a family Internet of things device.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
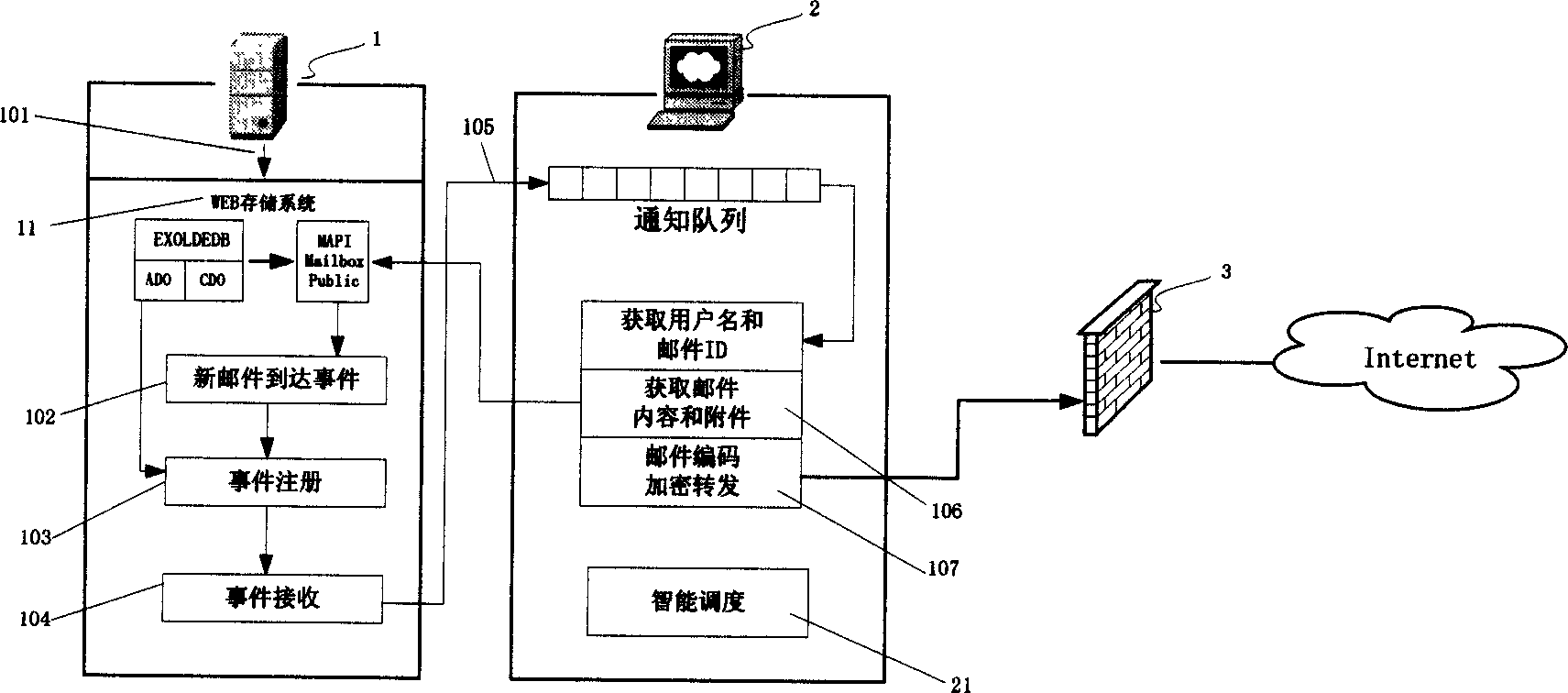
High-efficient intelligent system and method for acquiring e-mail in Microsoft Exchange e-mail server
InactiveCN1645844AReduce the burden onProtect privacyData switching networksInternet privacyMemory systems
The invention at least consists of MS exchange server and Push-mail exchange server. The system is connected with internet through fire wall. The memory system of Microsoft exchange captures the word of 'new mail is coming', through login and event reception, the ID and new user name are extracted and are inserted into 'notice array' of Push-mail exchange server to getting the content and attachment of mail. Finally the mail is encoded and encrypted for retransmission.
Owner:北京立通无限科技有限公司
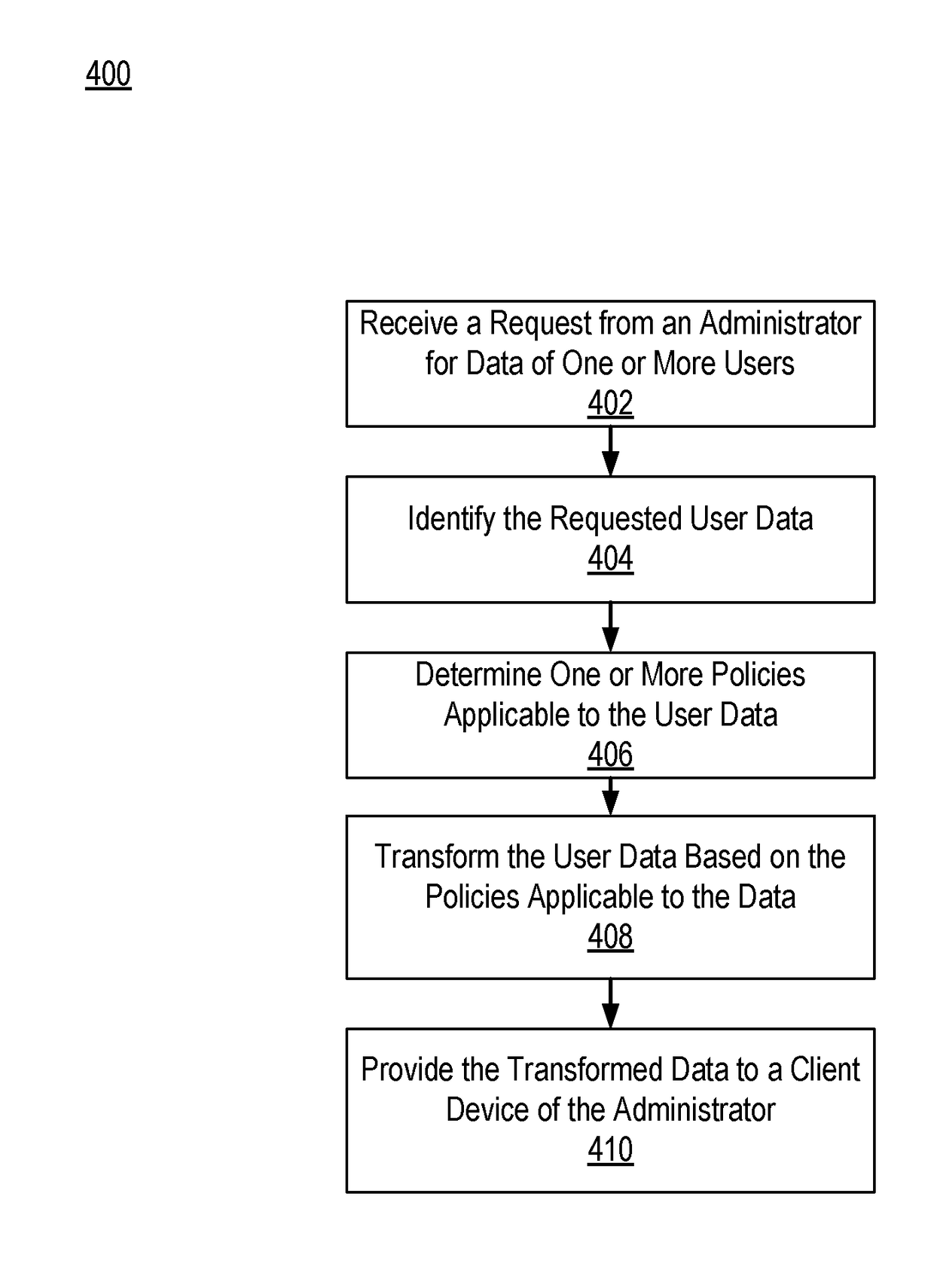
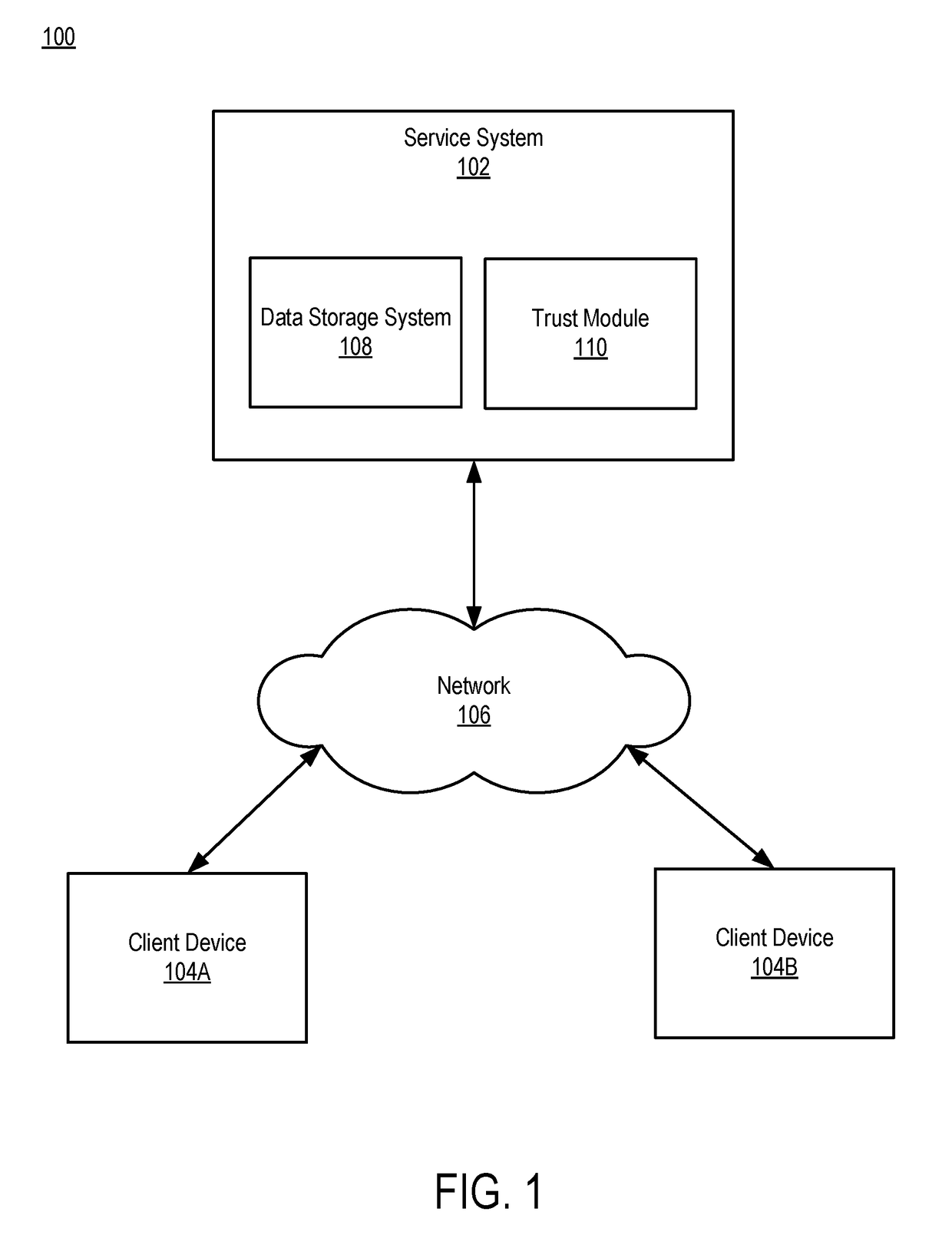
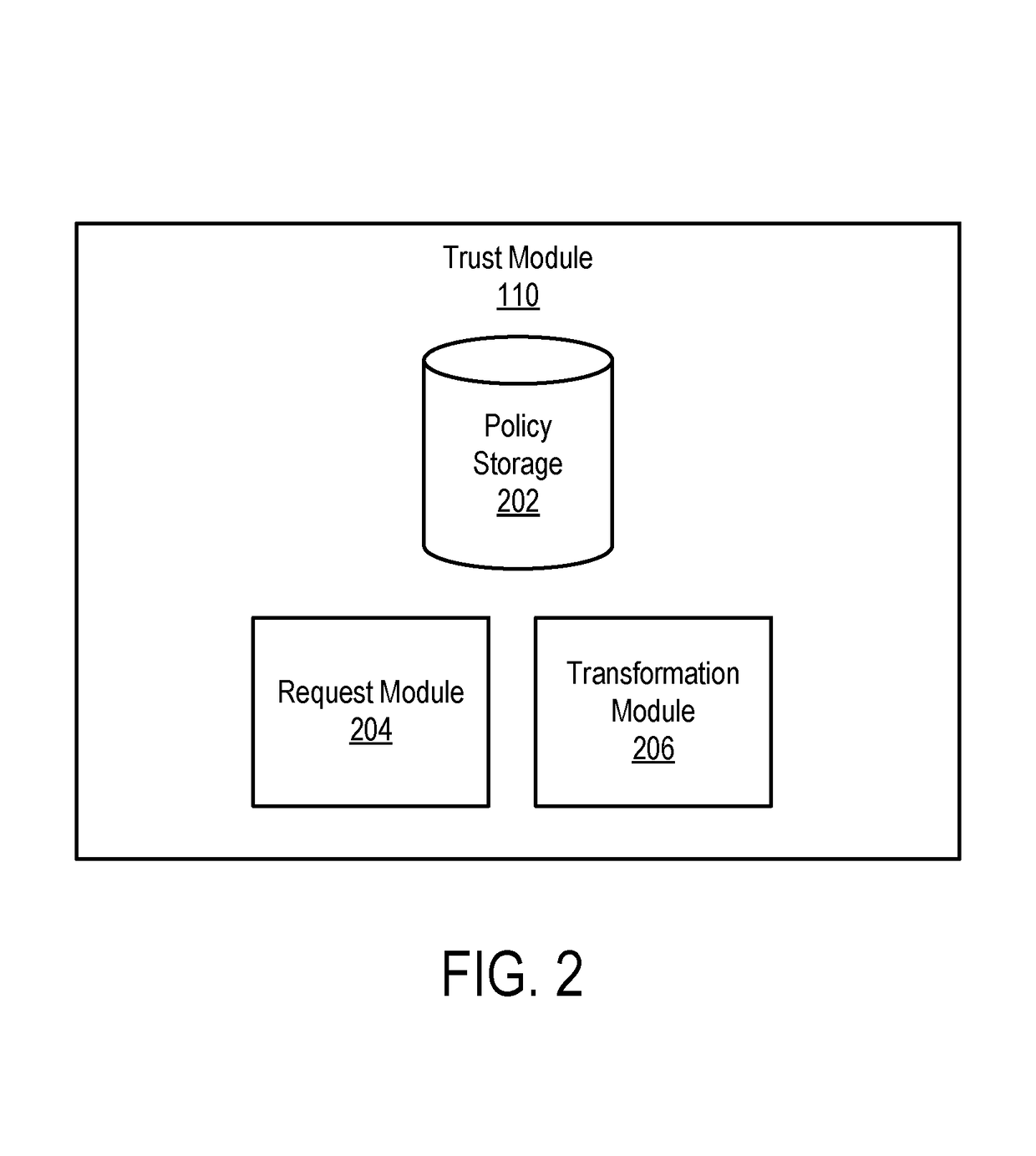
Providing access to user data
ActiveUS20180121447A1Improve functionality of applicationProtect privacyDigital data information retrievalDigital data protectionService systemData storage system
A service system provides users with access to online services. As part of providing the services to users, the service system stores data for users in a data storage system. When the service system receives a request from an administrator of the system for user data stored in the data storage system, the service system identifies the data requested by the administrator. The service system also determines policies that apply to the data. The determined policies indicate transformations that are to be performed on the data to protect the privacy of the users. The service system transforms the user data as indicated by the policies and provides the transformed user data to the administrator.
Owner:SALESFORCE COM INC
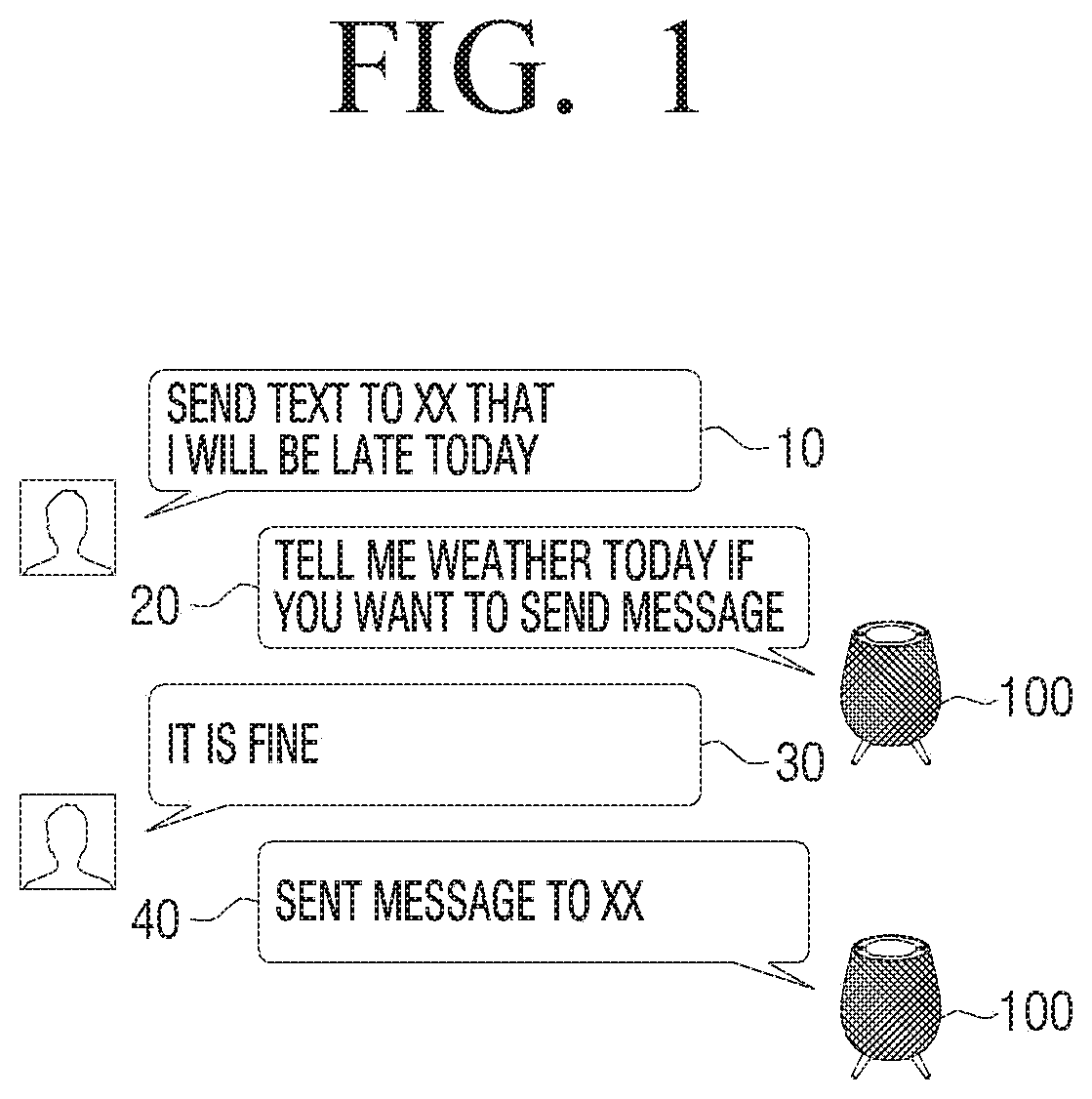
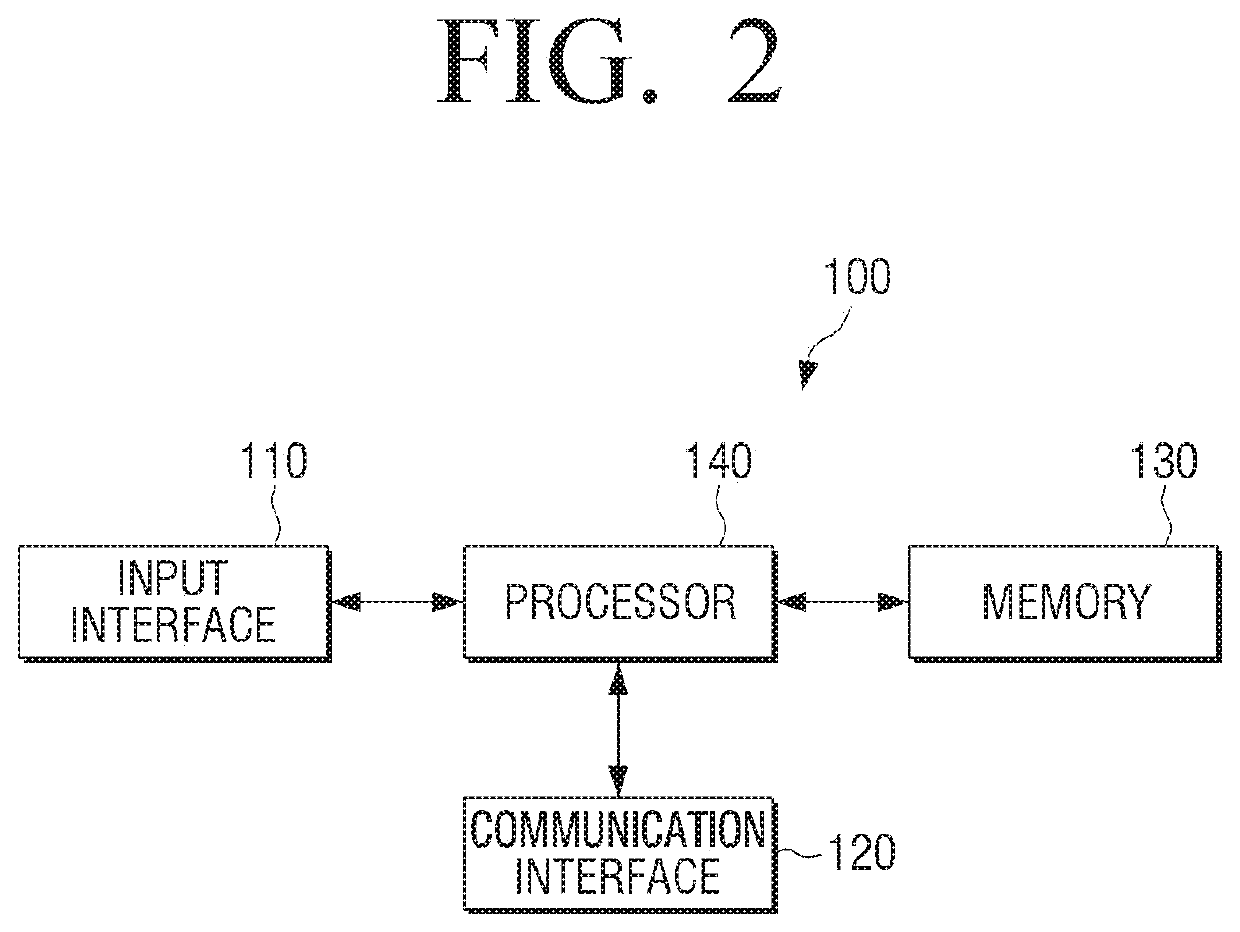
Electronic device and control method thereof
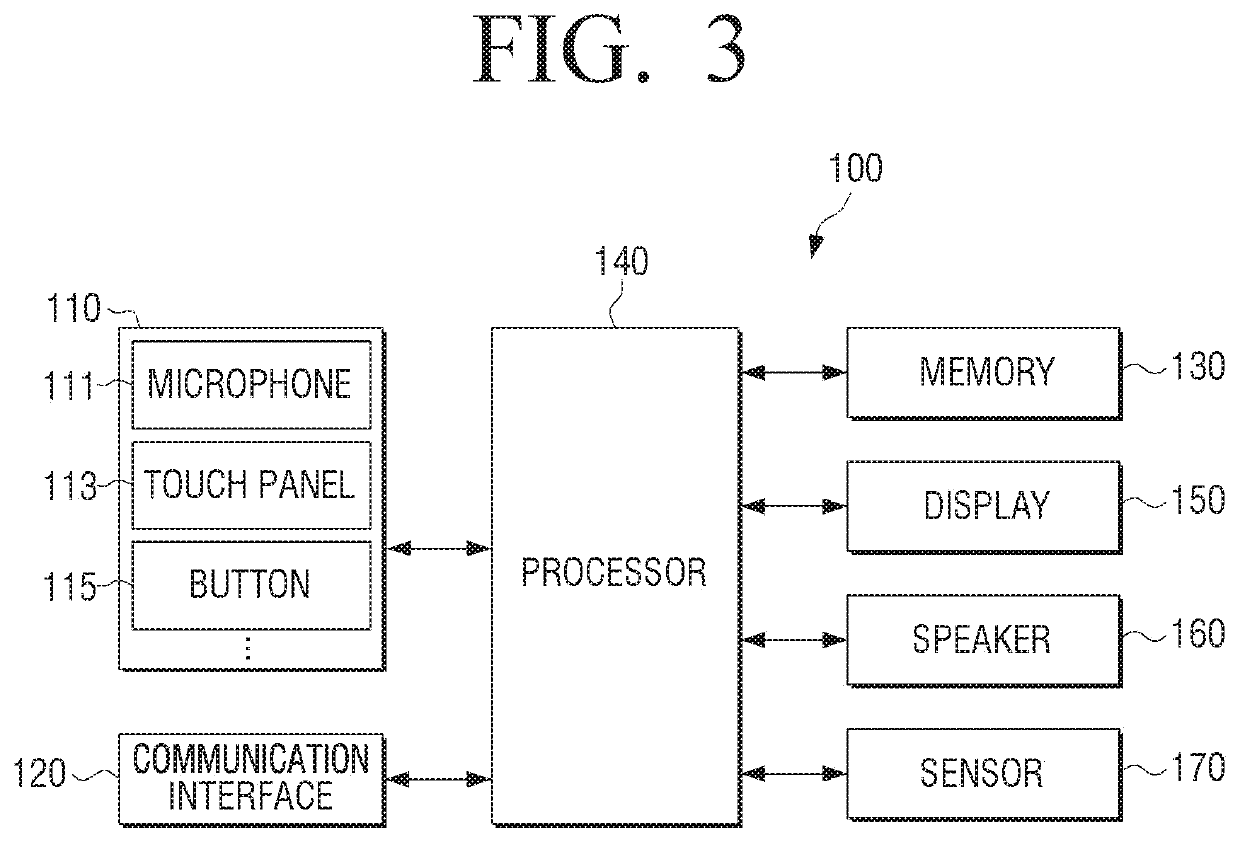
ActiveUS20200135213A1Protect privacyEnhanced securityInput/output for user-computer interactionDigital data authenticationCommunication interfaceEngineering
An electronic apparatus and a control method are provided, including an input interface, a communication interface, a memory including at least one command, and at least one processor configured to control the electronic device and execute the at least one command to receive a user speech through the input interface, determine whether or not the user speech is a speech related to a task requiring user confirmation by analyzing the user speech, generate a question for the user confirmation when it is determined that the user speech is the speech related to the task requiring the user confirmation, and perform a task corresponding to the user speech when a user response corresponding to the question is input through the input interface. Embodiments may use an artificial intelligence model learned according to at least one of machine learning, a neural network, and a deep learning algorithm.
Owner:SAMSUNG ELECTRONICS CO LTD
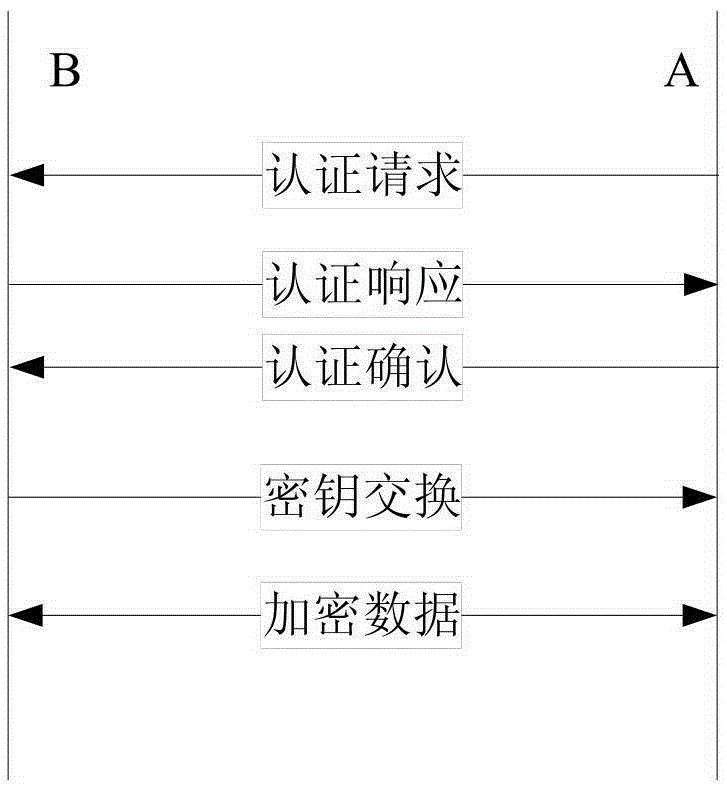
Method and system for automatically generating shared secret key
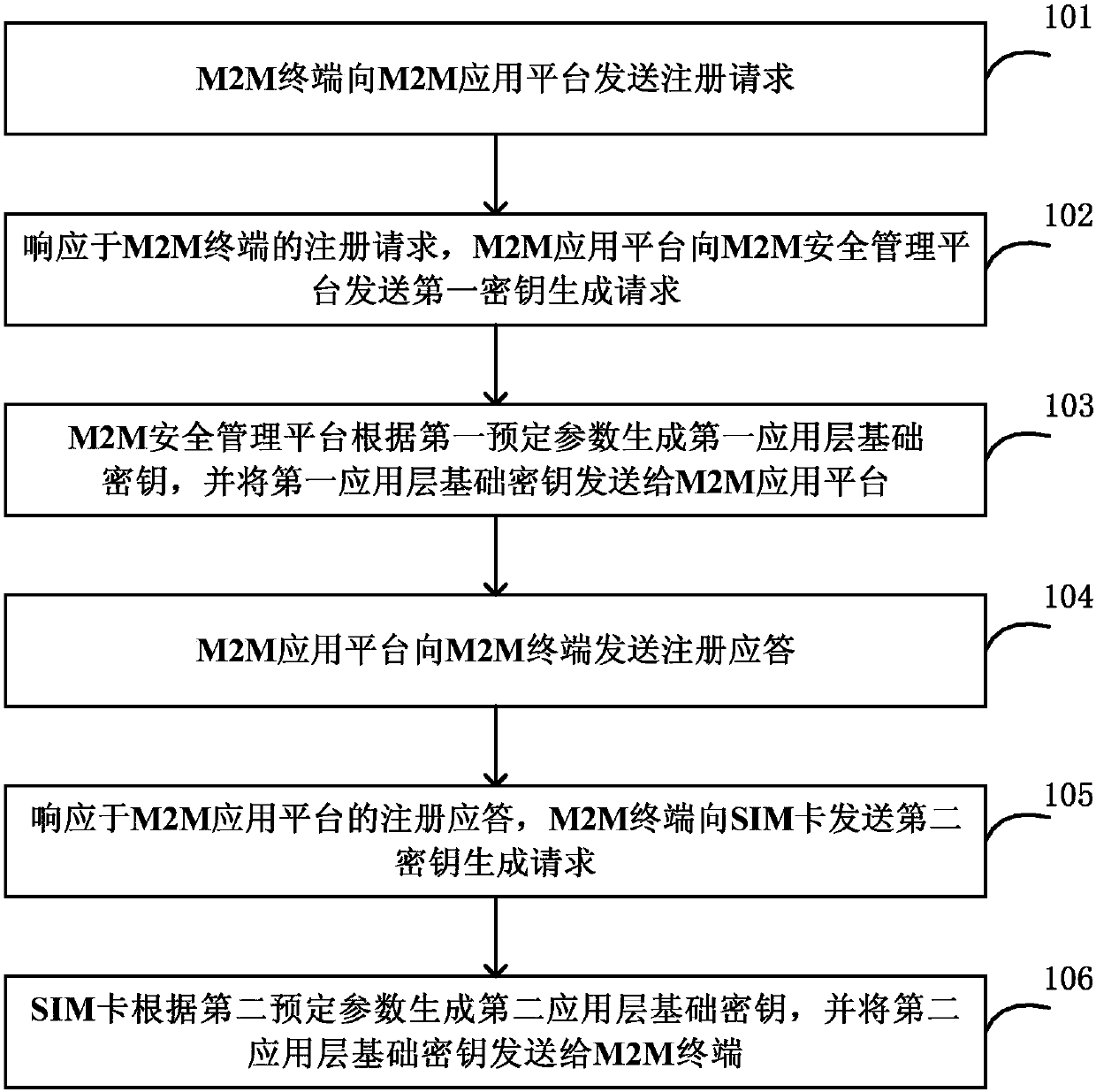
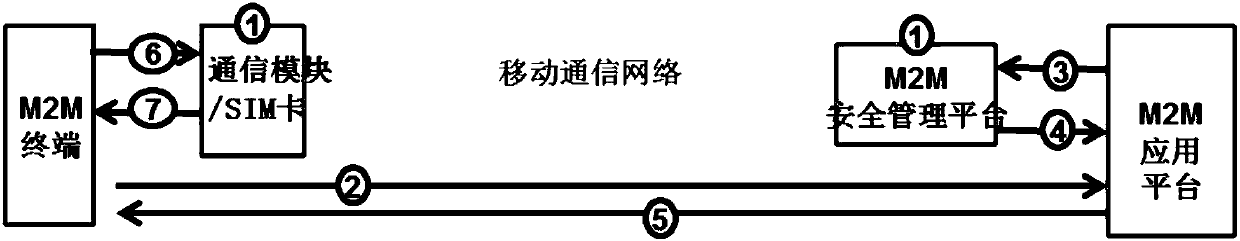
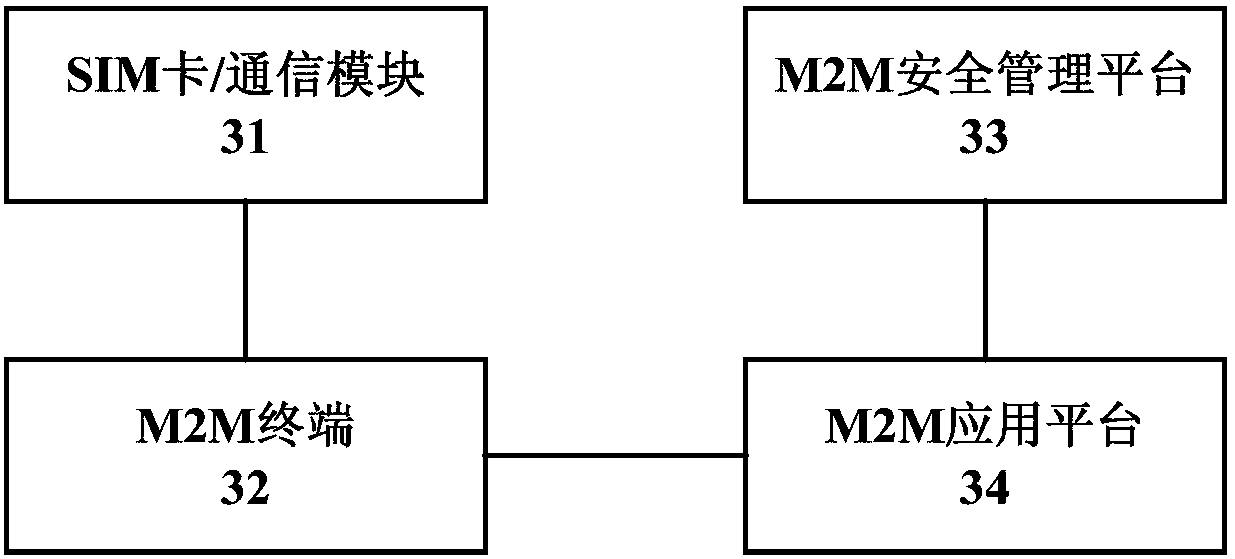
ActiveCN107592624AProtect privacyRealize automatic generationSecurity arrangementMachine-to-machine/machine-type communication serviceKey generationShared secret
The invention discloses a method and system for an automatically generating a shared secret key. The method comprises the steps: responding to a registration request of an M2M terminal, and enabling an M2M application platform to transmit a first secret key generation request to an M2M safety management platform; enabling an M2M safety management platform to generate a first application layer basic secret key according to a first predetermined parameter, and transmitting the first application layer basic secret key to the M2M application platform; responding to a registration response of the M2M application platform, and enabling the M2M terminal to transmit a second secret key generation request to an SIM card; enabling the SIM card to generate a second application layer basic secret keyaccording to a second predetermined parameter, and transmitting the second application layer basic secret key to the M2M terminal, wherein the first and second predetermined terminals are the same, and the first and second application layer basic secret keys are the same. According to the invention, the SIM card and the M2M safety management platform are triggered to generate the application layerbasic secret keys in the registration process of the M2M terminal in the M2M application platform, thereby achieving the automatic generation and updating of the application layer basic secret keys between the M2M terminal and the M2M application platform, and protecting the privacy of a system secret key.
Owner:CHINA TELECOM CORP LTD
Confidential information transmitting method used for common platform client side and confidential information transmitting device thereof
ActiveCN106685892AProtect privacyProtection of privacyTransmissionRecord carriers used with machinesClient-sideInternet privacy
The embodiment of the invention provides a confidential information transmitting method used for a common platform client side. The method comprises the steps that the coding algorithm of a two-dimensional code, the common platform client side and the target contact person in a contact list selected by a user are identified; the coding algorithm and the corresponding relationship with the common platform client side thereof are transmitted to the target contact person by a communication tool supported by the target contact person selected by the user so that the communication tool of the target contact person is enabled to receive the coding algorithm of the two-dimensional code and configure and save the coding algorithm of the two-dimensional code on the common platform client side; information for transmission inputted by the user is received through the common platform client side, and the two-dimensional code of the information for transmission is generated according to the coding algorithm corresponding to the common platform client side and the target contact person; and the two-dimensional code is transmitted to the publish page of the common platform client side. Meanwhile, the embodiment of the invention also provides a confidential information transmitting device used for the common platform client side. The privacy of the information can be effectively protected by the technical scheme.
Owner:BEIJING QIHOO TECH CO LTD +1
Multi-party real-time intercom system and data flow thereof
InactiveCN104105013ALess devicesProtect privacyStations for two-party-line systemsLoudspeakerDiscussion group
The invention discloses a multi-party real-time intercom system which comprises a terminal system, an amplification system, a second loudspeaker and a microphone. The invention further discloses a data flow of the multi-part real-time intercom system. The intercom system which is as low in price as an interphone but is different from other intercom systems, can be installed through one wire, can communicate in a talk-back mode through radio and can also build a discussion group capable of protecting privacy of customers is developed and achieved, and the intercom system can be conveniently used in the fields of bull sessions, villas, production lines and the like and is worthy of being widely popularized.
Owner:SICHUAN XINGSHIFA ENERGY SCI & TECH
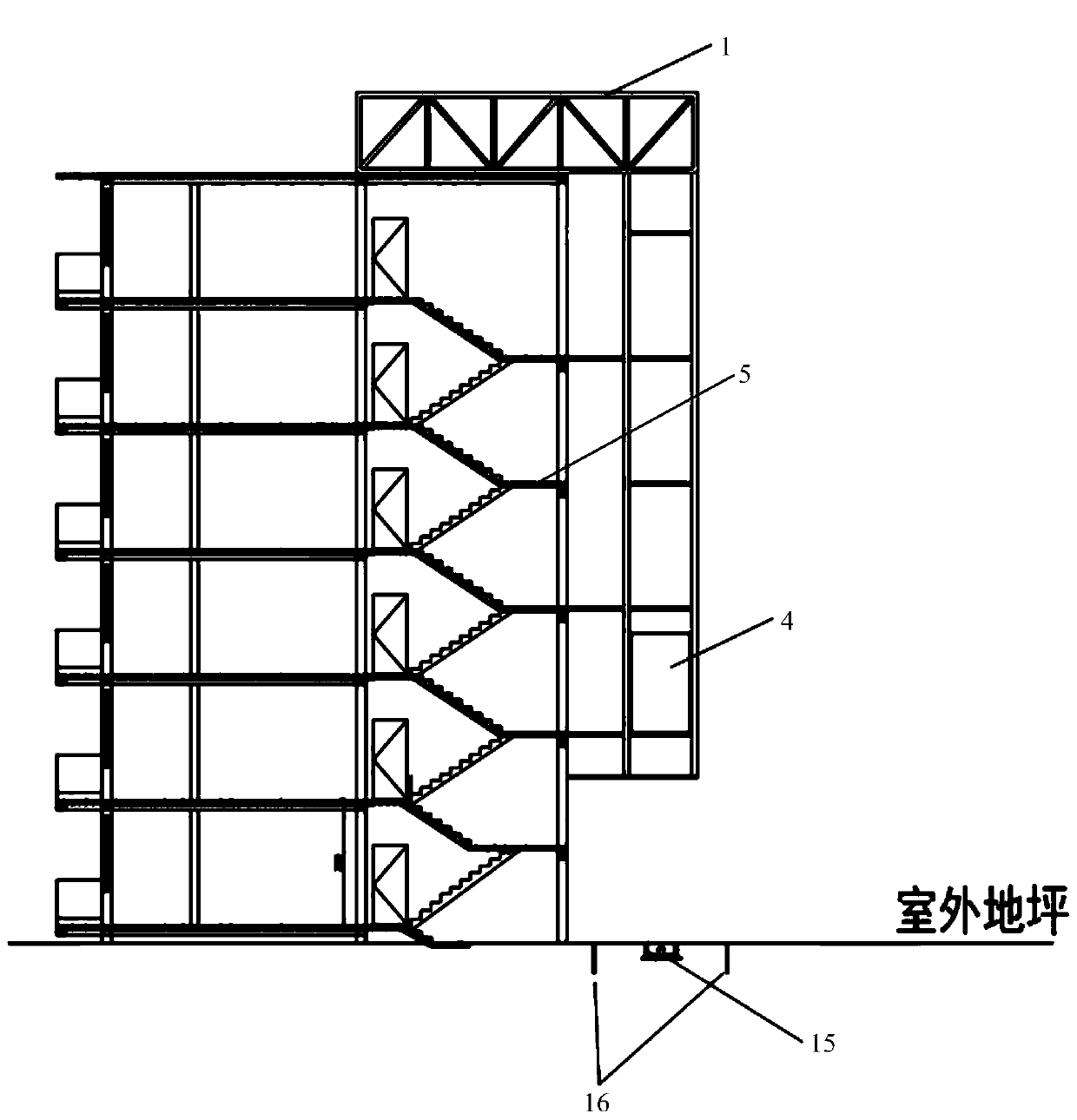
Novel roof steel truss suspension assembled elevator structure and construction method thereof
The invention relates to a novel roof steel truss suspension assembled elevator structure and a construction method thereof, and belongs to the field of house construction elevator engineering. The elevator structure comprises a roof steel truss, a steel frame shaft and steel coupling beams, wherein one end of the roof steel truss is connected with a column or beam of an original building, and theother end of the roof steel truss is connected with the top of the steel frame shaft; one ends of the plurality of steel coupling beams are connected with the original building, and the other ends ofthe steel coupling beams are connected with an upright of the steel frame shaft; the height of the bottom of the steel frame shaft away from the group is not less than 4m, a lift car is arranged in the steel frame shaft, and when needing to pick passengers to the ground, the lift car can be separated from the steel frame shaft and descend to the ground; and bolt connection is formed between the roof steel truss and the column or beam of the original building, between the roof steel truss and the steel frame shaft, between the steel frame shaft and the steel coupling beams, and between the steel coupling beams and the original building. According to the invention, the elevator structure and construction method solve the daylighting problem of residents at a ground floor without affecting the ground traffic, and people and vehicles can pass through the bottom of the elevator shaft.
Owner:SHANDONG UNIV
Water-proof sex massage device
InactiveCN1586446AReduce noiseProtect privacyVibration massageGenitals massageEngineeringSurface plate
The waterproof sex massage device includes rotating creeper, transmission mechanism to drive the rotating creeper, and controller for the rotating creeper. The rotating creeper and the transmission mechanism are set in front end of the controller, and the controller includes battery compartment, control box with circuit board and buttons, etc. The rotating creeper and the transmission mechanism are covered with elastic sealing jacket. The present invention has excellent waterproof performance, may be used in different environment, especially in bathing room, has less noise and is suitable for female.
Owner:广州广保顺景软胶制品有限公司
Home security management system based on Internet of things
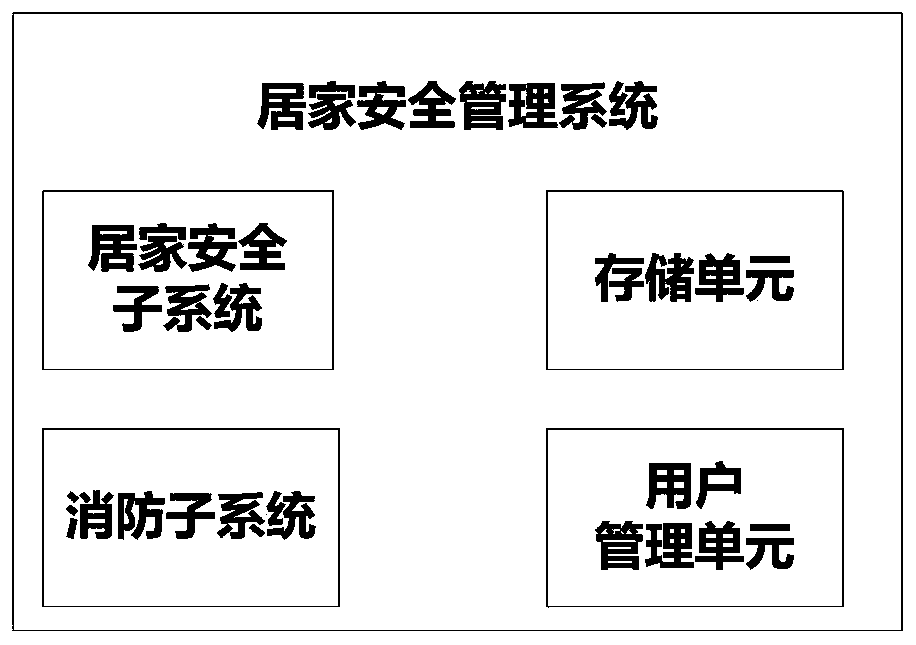
InactiveCN110201339AProtect privacyReduce lossesFire rescueFire alarm electric actuationSecurity managementData acquisition
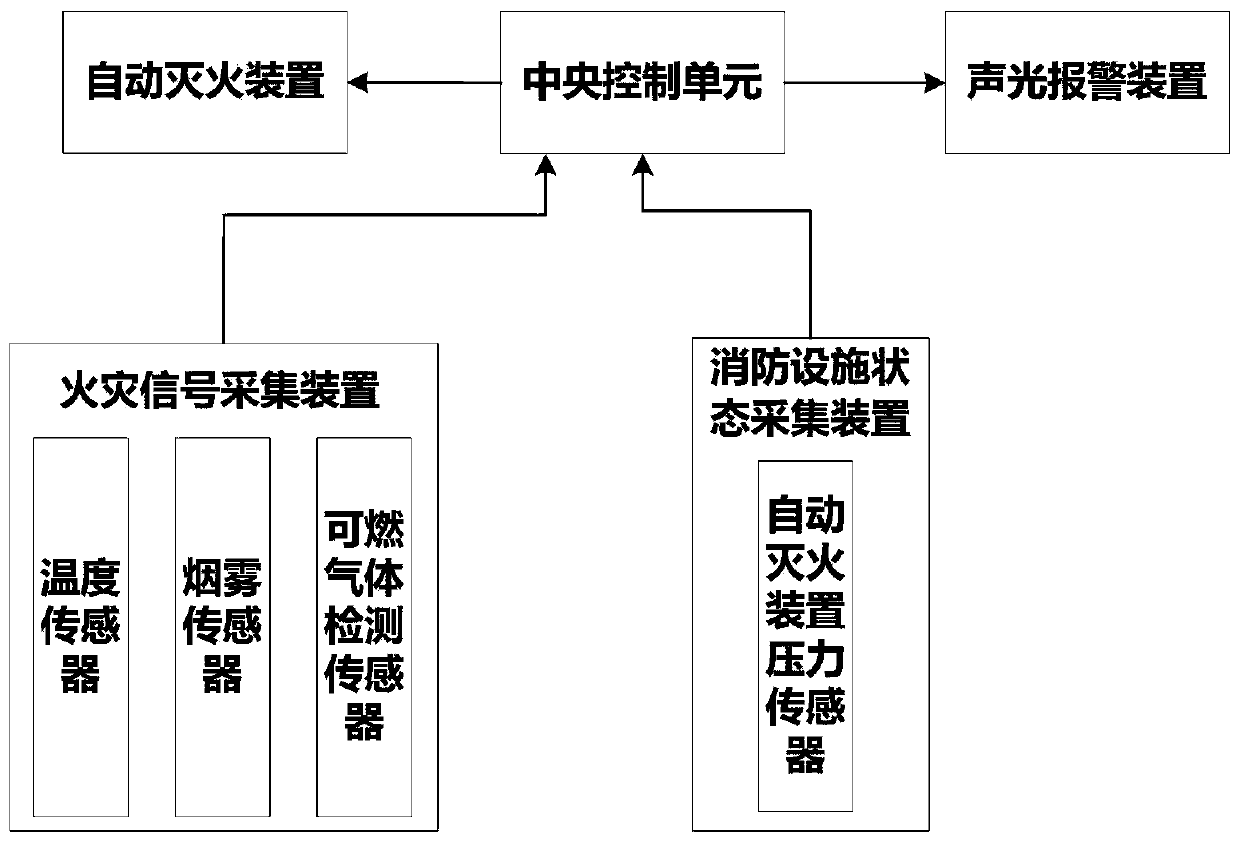
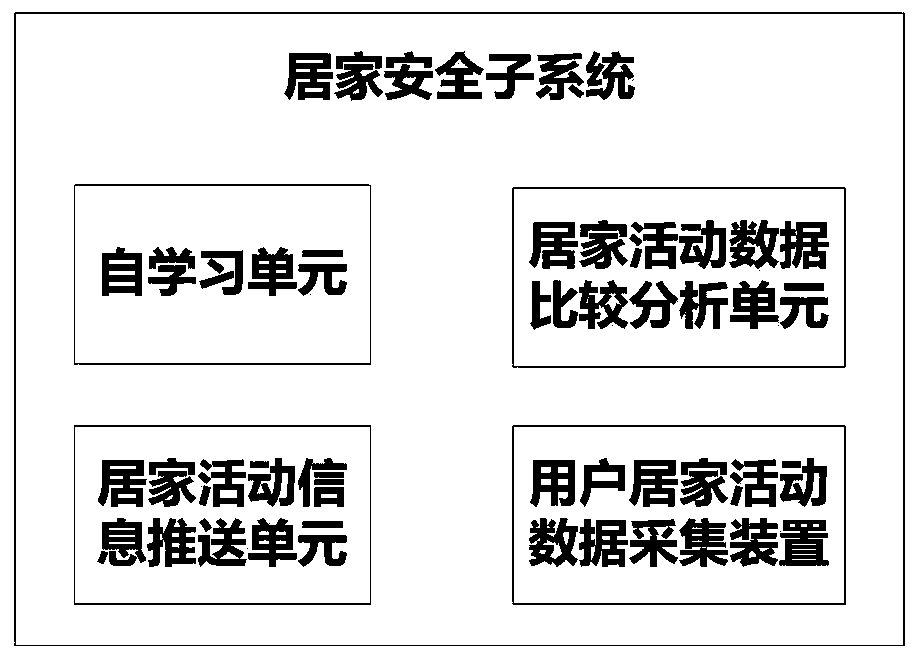
The invention discloses a home security management system based on Internet of things. The system comprises a user management unit, a storage unit, a home security subsystem and a fire fighting subsystem. The user management unit is used for user registration and system contact account registration, the storage unit is used for storing data of the home security subsystem and the fire fighting subsystem, the home security subsystem comprises a user home activity data acquisition device, a self-learning unit, a home activity data comparison analysis unit and a home activity information pushing unit, and the fire fighting subsystem comprises a fire signal acquisition device, a fire fighting facility state acquisition device, an acousto-optic alarm device, an automatic fire extinguishing device and a central control unit. Comprehensive home safety management is carried out from two aspects of the user and fire environment. The home security subsystem collects human body activity information of the user, can analyze health and security conditions of the user from the activity information, and pushes report information to the user through a bound contact account. The fire fighting subsystem analyzes the most suitable disposal method at present.
Owner:李成
Picture processing method and device
InactiveCN104484613AProtect privacyImprove privacyDigital data protectionInput/output processes for data processingImage processingComputer graphics (images)
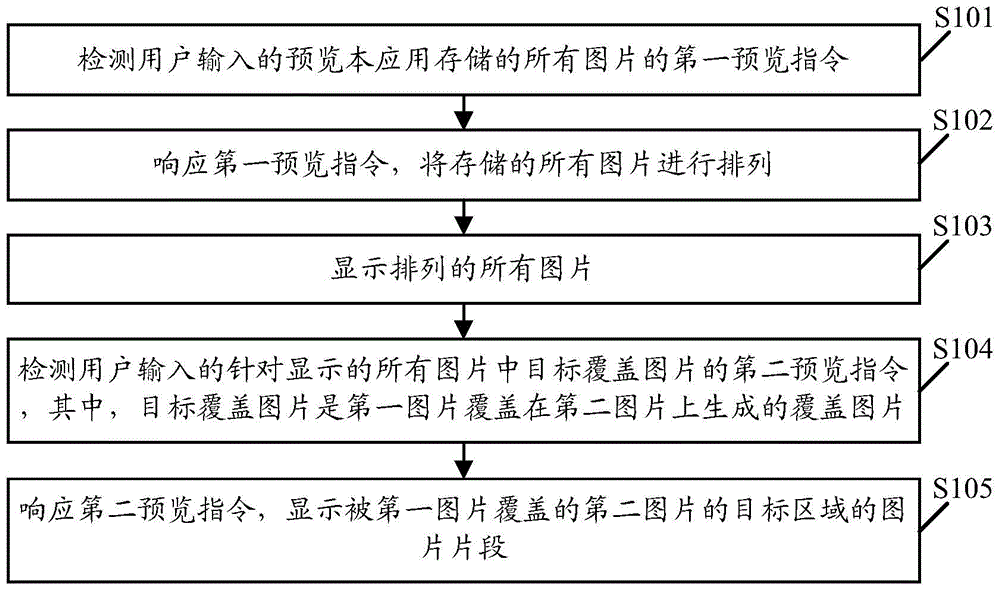
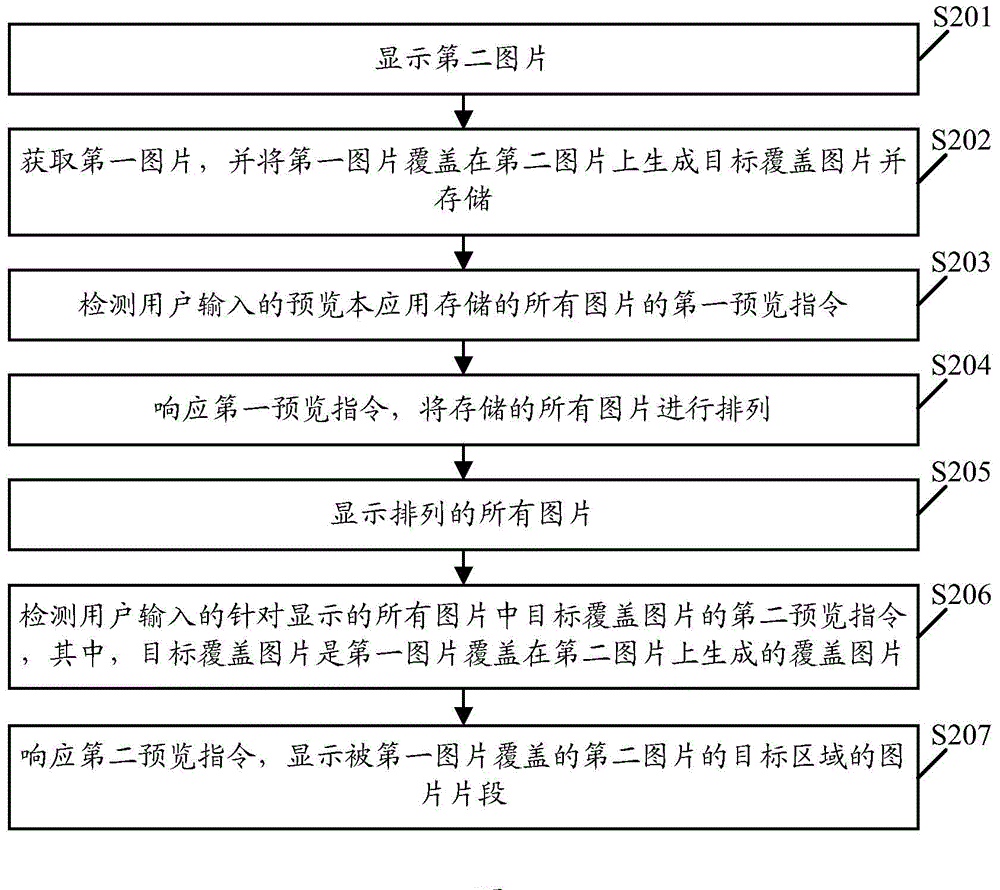
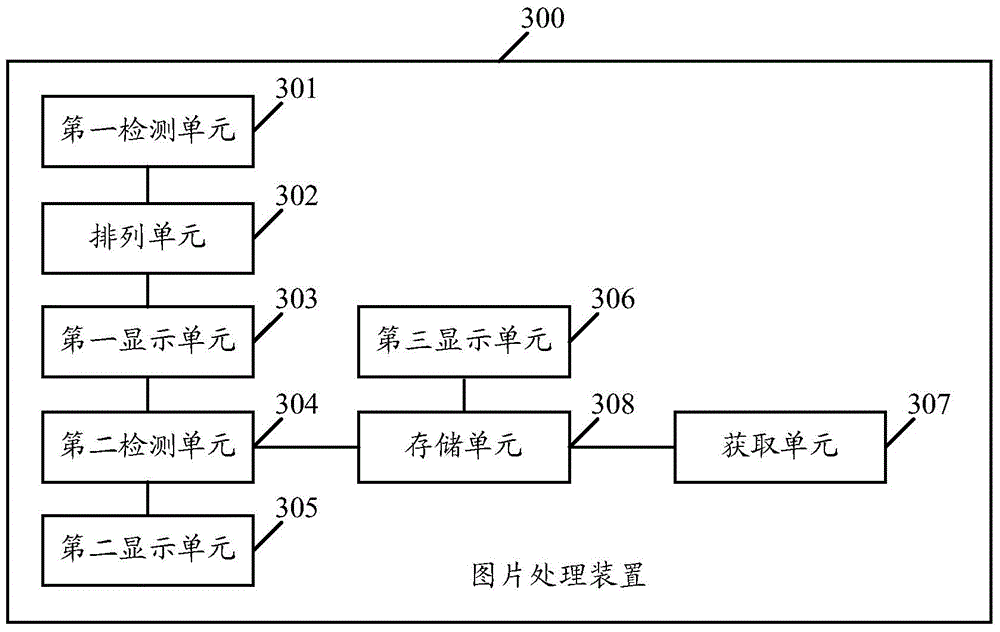
The embodiment of the invention discloses picture processing method and device. The method comprises the steps of detecting a first preview instruction input by a user for previewing all pictures stored in the application; responding to the first preview instruction and arranging all stored pictures; displaying all arranged pictures; detecting a second preview instruction input by the user for a target covering picture in the all displayed pictures, wherein the target covering picture is the covering picture formed by covering a second picture with a first picture; responding to the second preview instruction, ad displaying a picture segment of a target area of the second picture covered with the first picture. With the adoption of the picture processing method and device, the privacy of the pictures can be improved.
Owner:VOVIV TECH SHENZHEN
Identity card, information carrier and housing designed for its application
InactiveUSRE43333E1Avoid forgery and falsificationProtect privacyPayment architectureIndividual entry/exit registersHousing designIndividual data
Owner:VAN DER VALK ROBERT WILLEM
Medical resource sharing method and system
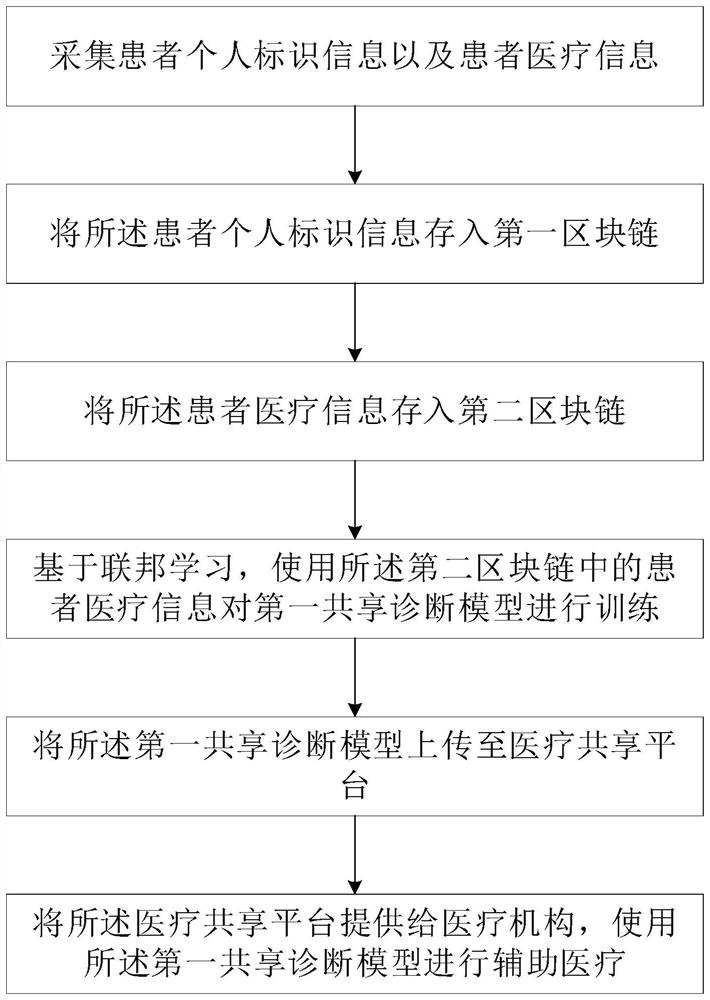
PendingCN114446454AProtect privacyAvoid leaking privacyMedical automated diagnosisDigital data protectionParamedicineDiagnostic model
The invention discloses a medical resource sharing method and system, and the method comprises the steps: collecting the personal identification information of a patient and the medical information of the patient, storing the personal identification information of the patient into a first block chain, storing the medical information of the patient into a second block chain, and carrying out the sharing of the medical resources based on federal learning. And training a first shared diagnosis model by using the patient medical information in the second block chain, uploading the first shared diagnosis model to a medical sharing platform, providing the medical sharing platform to a medical institution, and performing auxiliary medical treatment by using the first shared diagnosis model. According to the invention, on the premise that the privacy of the patient is fully guaranteed, medical resource sharing is realized, all medical institutions registered on the medical sharing platform can query the medical information of the patient, and the first diagnosis model provides data support for the medical institutions to carry out medical diagnosis, so that the medical institutions are helped to improve the accuracy of the medical diagnosis.
Owner:深圳市铱硙医疗科技有限公司
A method for system user to delegate others for security assistance
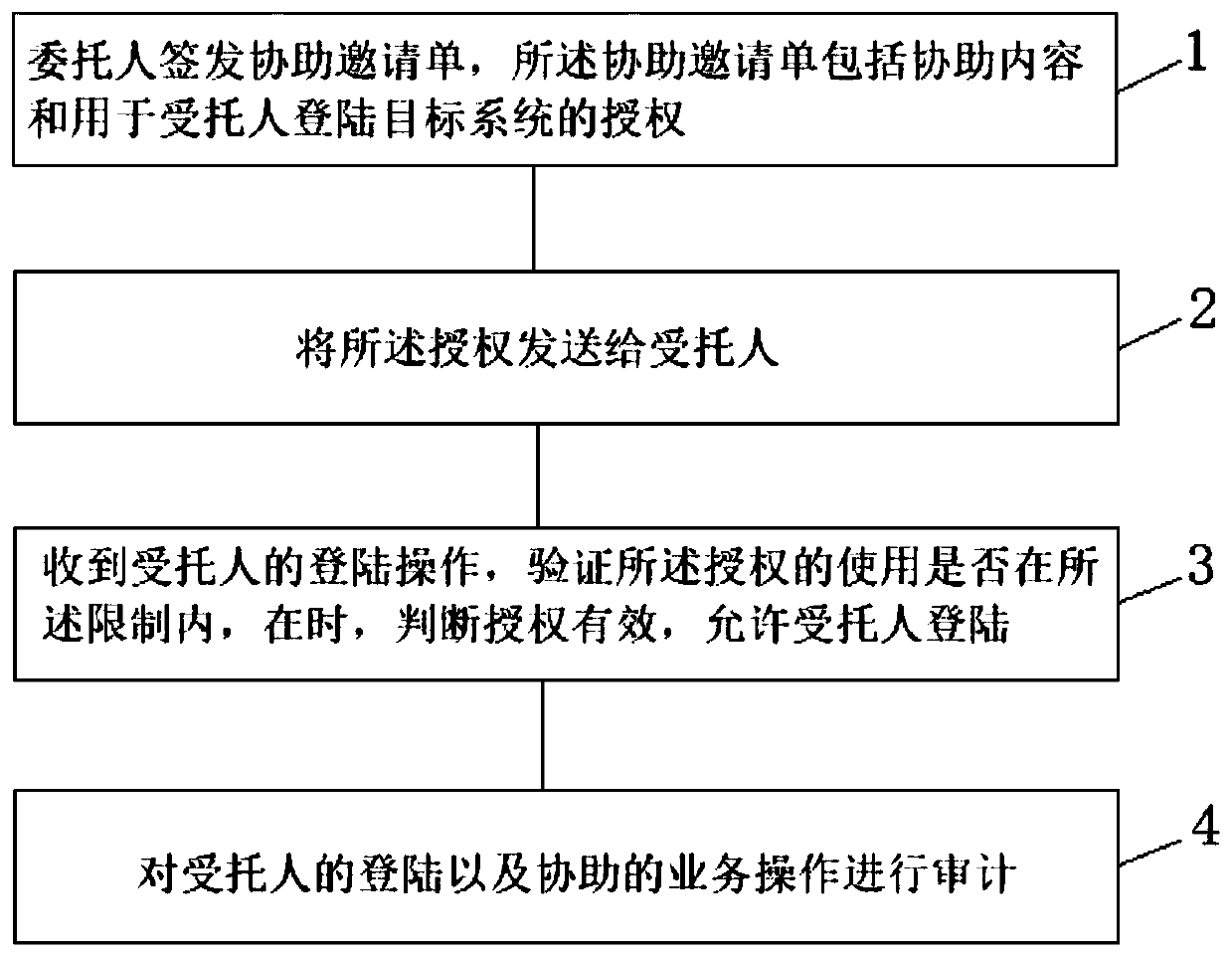
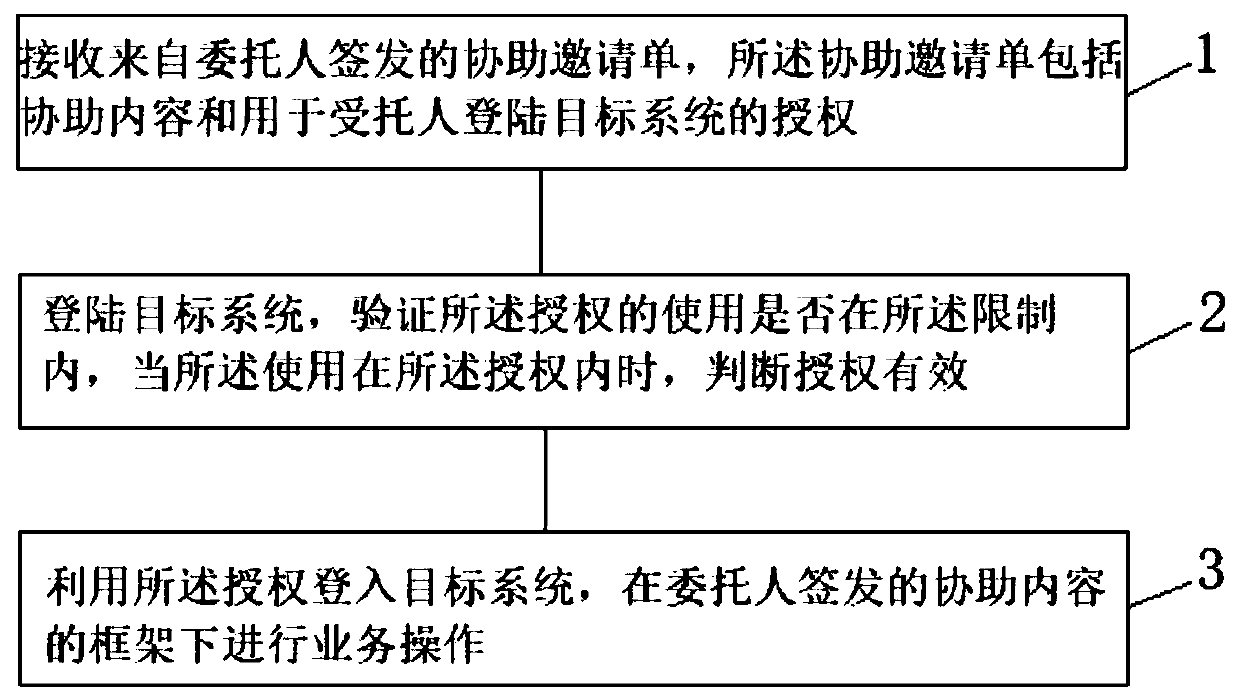
InactiveCN110781471APrevent leakageProtect privacyDigital data protectionDigital data authenticationExpiration TimeInternet privacy
The invention discloses a method for a system user to delegate others for security assistance, comprising the following steps: issuing an assistance invitation list by a delegator, the assistance invitation list comprising assistance content and authorization for a victim to log in a target system; sending the authorization to the trustee; and auditing the login of the supported person and the assisted business operation. According to the method, the assistance invitation list is sent to the entrusted person to enter the target system, so that leakage of a user account password is avoided, andthe privacy of the user is guaranteed; through the management of the assistance invitation list, the available IP segment, the maximum use frequency, the expiration time management, the available function module, the operation function and the accessible service data of the assistance invitation list are limited, detailed auditing is carried out on the operation assisted by an entrustee, and thesafety of the service data of the entrustee is guaranteed.
Owner:厦门海晟融创信息技术有限公司
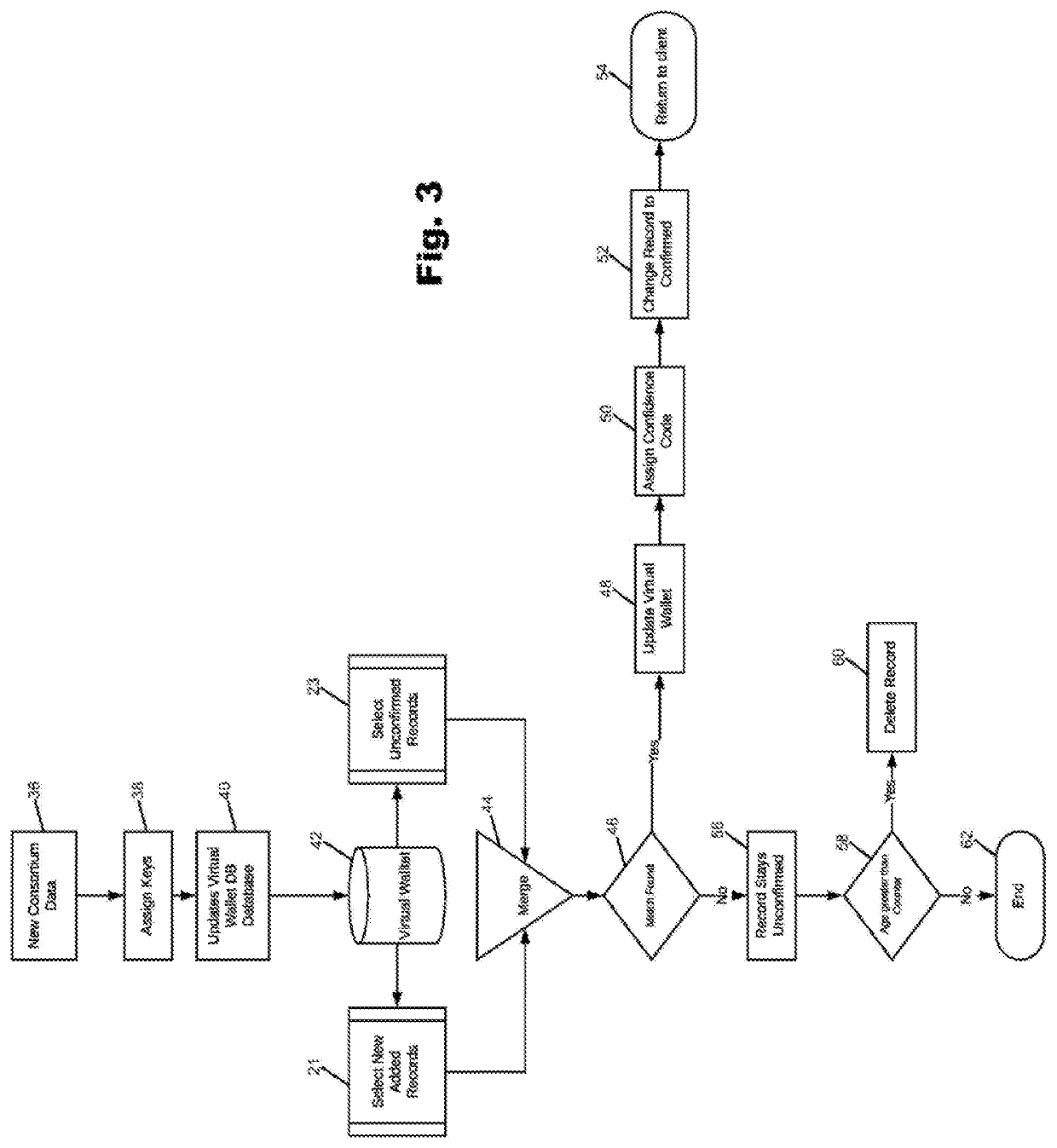
Point-of-Sale Consumer Resolution System
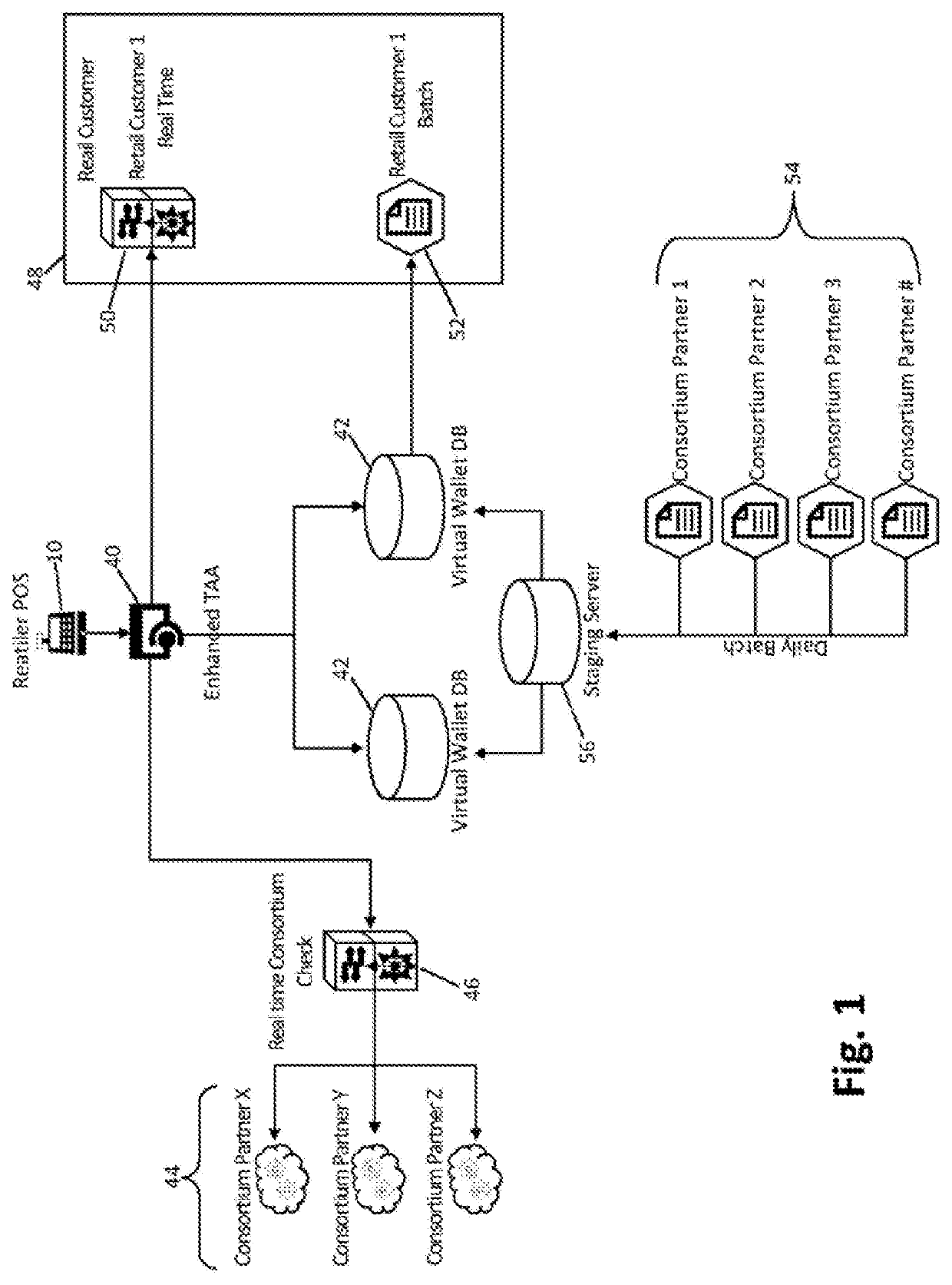
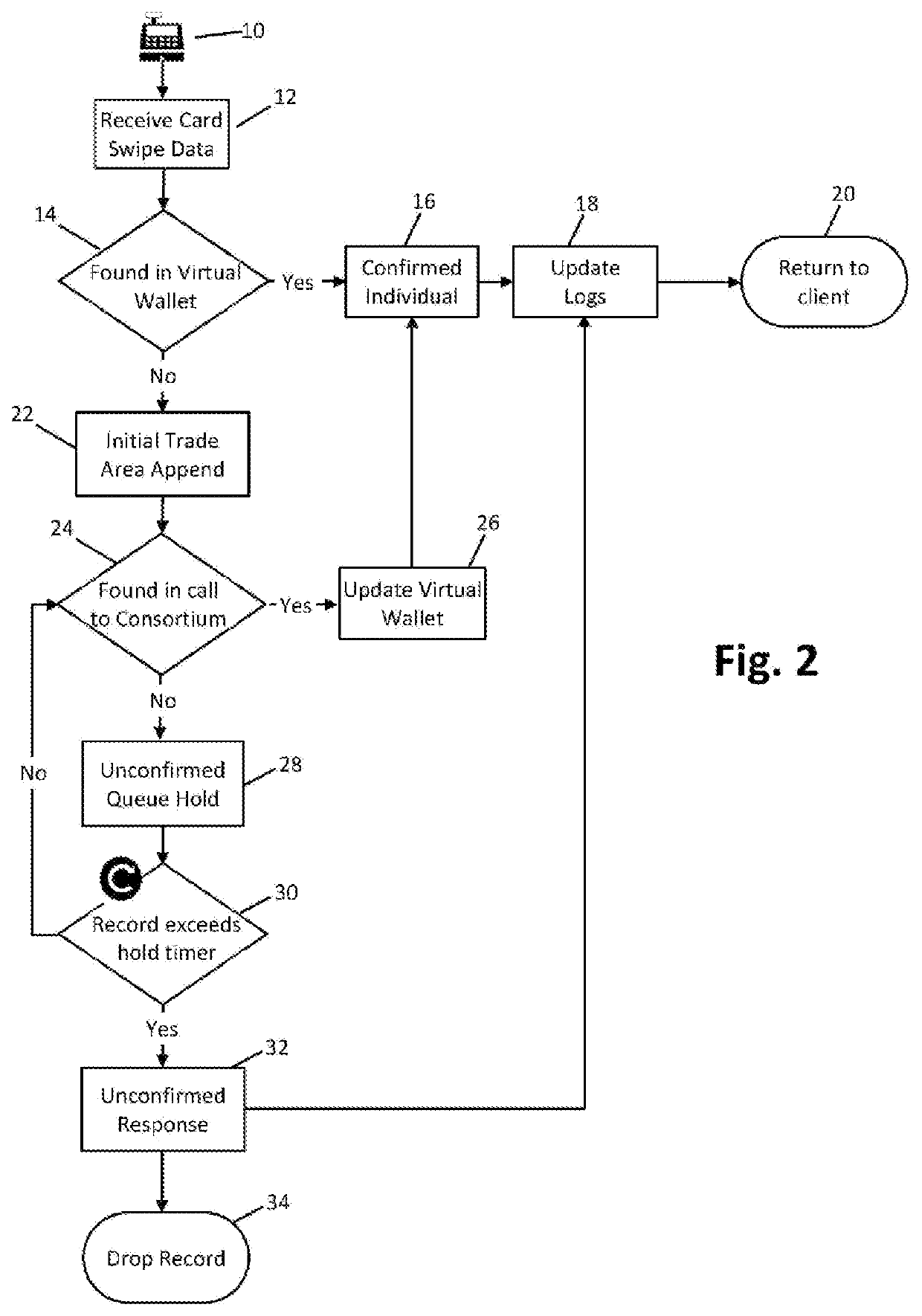
PendingUS20220058620A1Protect privacyComputer security arrangementsPoint-of-sale network systemsEngineeringData mining
A system for identifying a consumer at a retailer point of sale (POS) incorporates a virtual wallet database that contains consumer records. A consortium processor utilizes a database or databases with information known to the electronic tender provider but not available to the virtual wallet database. If the identifying data from the retailer POS hardware does not match any data from the virtual wallet database, an enhanced trade area append processor is employed to find a matching consumer within the retailer POS trade area. If a match is found, the applicable address is attached to the consumer data captured at the POS. A record is then sent to the consortium processor, which compares this data to its own records and returns a match or no-match result. The virtual wallet database is updated based on the match results.
Owner:ACXIOM LLC
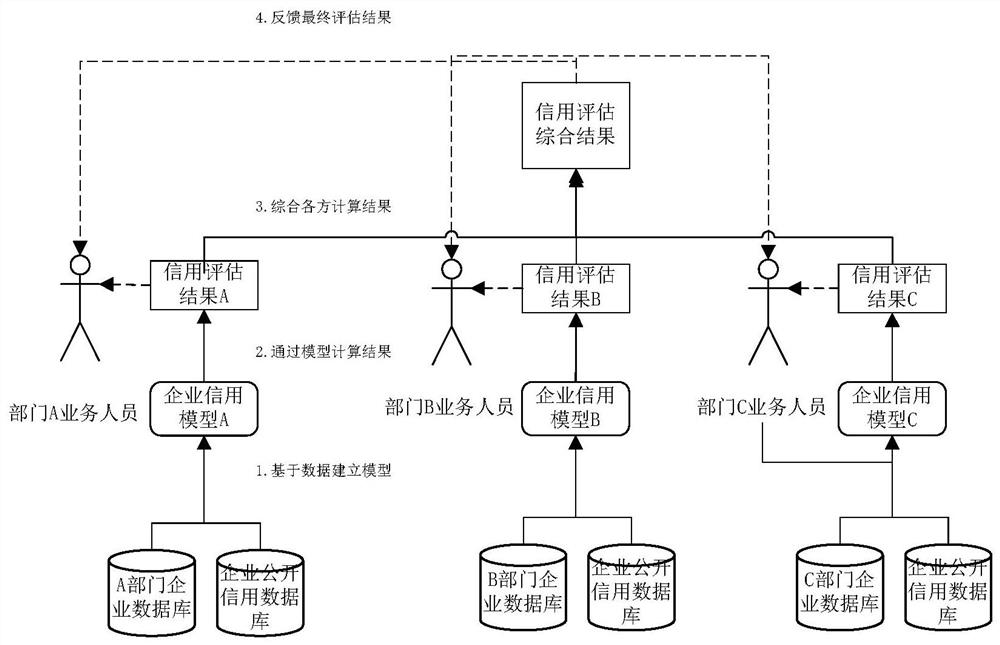
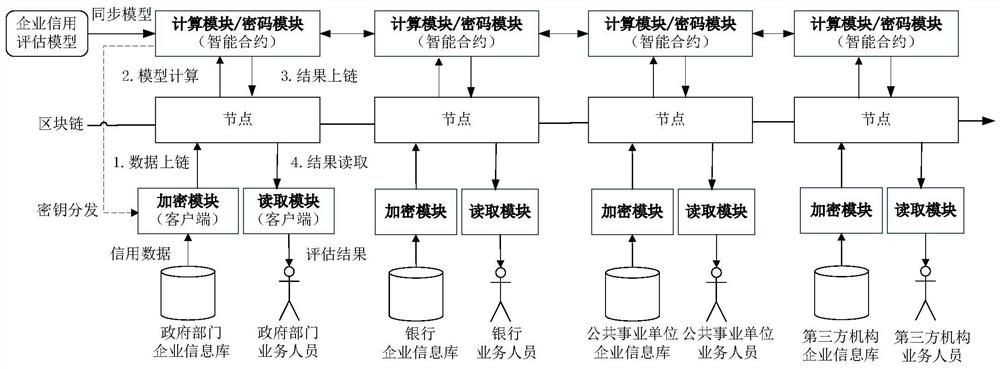
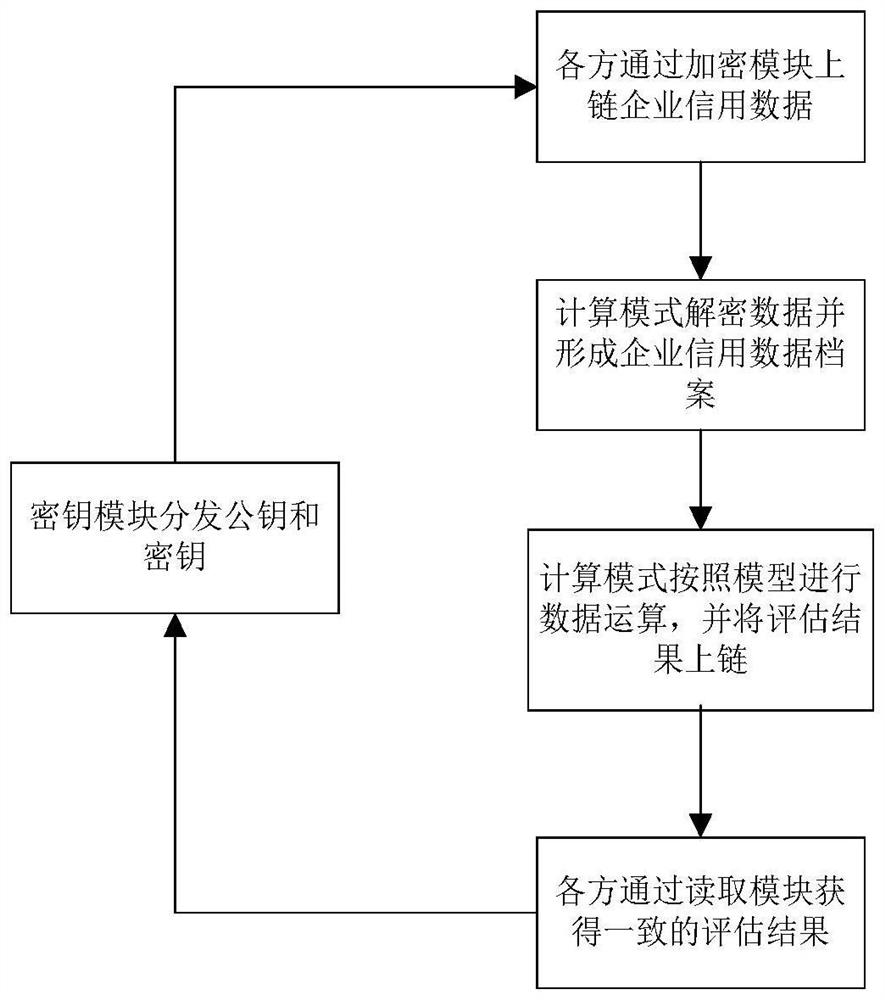
Enterprise credit data co-processing method and system based on intelligent contract
PendingCN114529385AProtect privacyIncrease motivationFinanceDigital data protectionData breachData science
The invention belongs to the technical field of enterprise credit risk assessment, and particularly relates to an intelligent contract-based enterprise credit data co-processing method, system and platform. Through the method recorded in the scheme and the system and the platform corresponding to the method, the enterprise credit data is subjected to uplink sharing through a dynamic asymmetric encryption algorithm, the privacy of the data is effectively protected, and the worry of data leakage of all parties is eliminated. The intelligent contract automatically completes reading and calculation of enterprise credit data, the whole process is not interfered by any party, and the right of each participant to obtain a result and the obligation of providing data are guaranteed; the enterprise credit evaluation results obtained by all parties are consistent, and the quality of the results can be obtained according to the quality of the data provided by any party, so that the motivation of all parties for improving the high-quality data can be effectively improved.
Owner:广州软件应用技术研究院
Onboard voice outputting device, voice outputting device, voice outputting method, and computer-readable storage medium
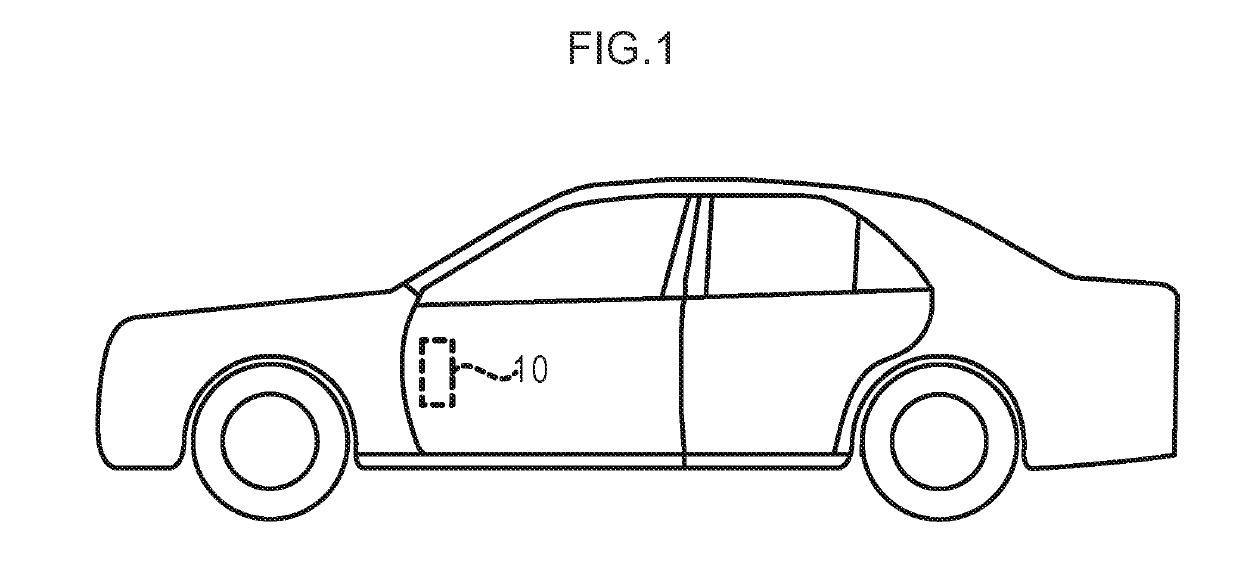
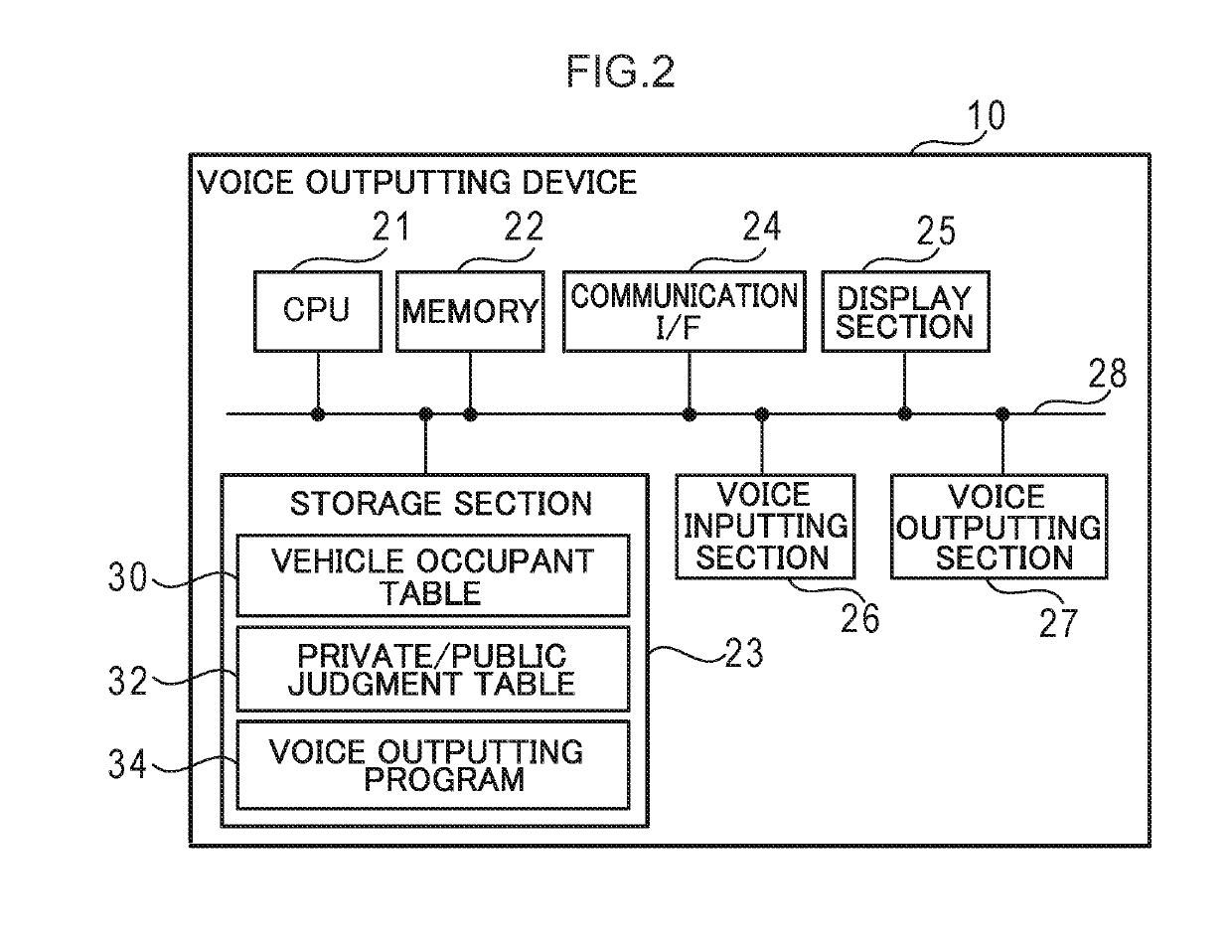
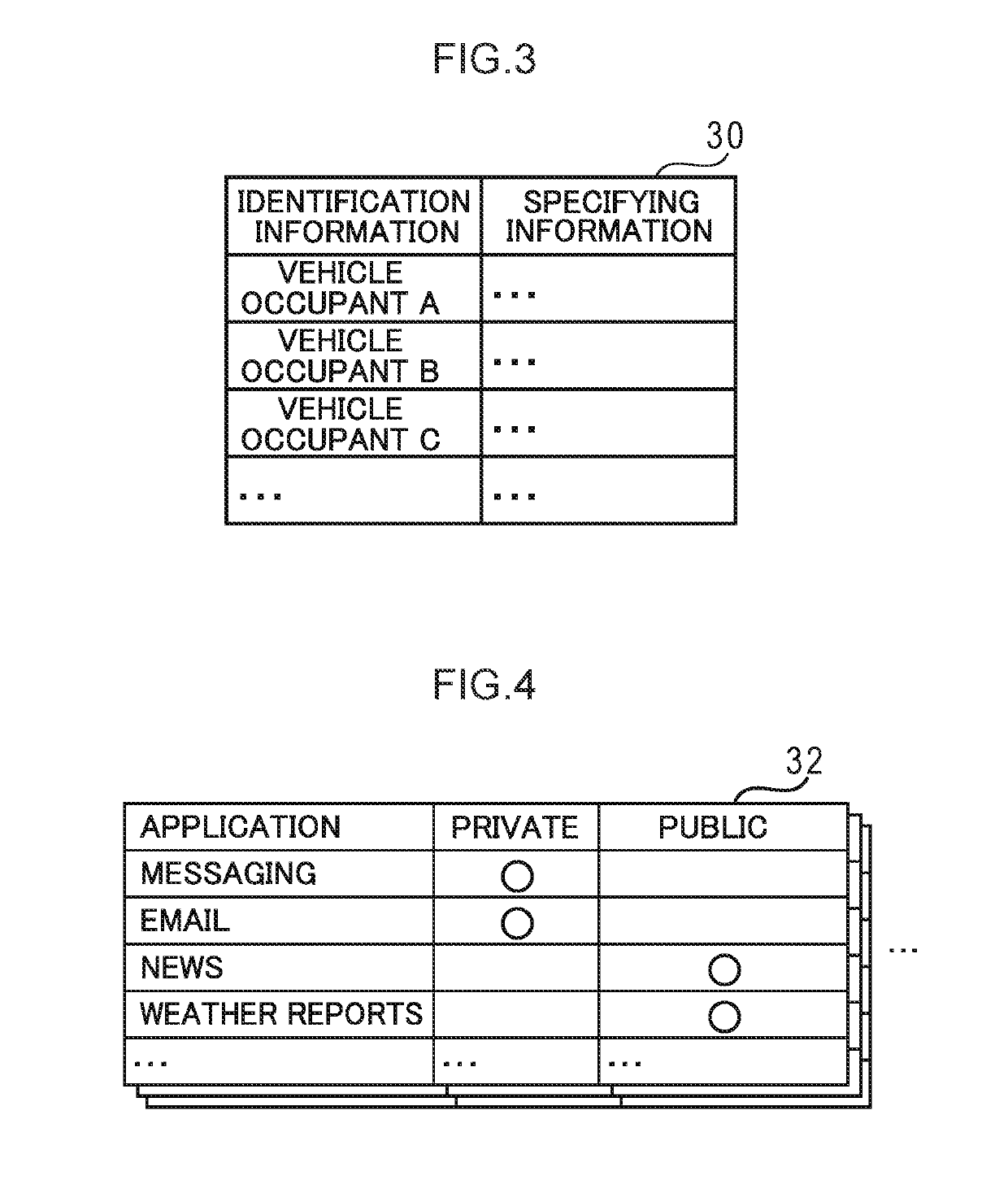
ActiveUS20190184826A1Protect privacyEasy to identifyDashboard fitting arrangementsCharacter and pattern recognitionSpeech outputEngineering
Owner:TOYOTA JIDOSHA KK
Fitting room based on indicating lamp reminding
ActiveCN111425019AProtect privacyPrivacy protectionSpecial buildingVisible signalling systemsEngineeringStructural engineering
The invention discloses a fitting room based on indicating lamp reminding. The fitting room comprises a control shell fixedly arranged underground, a linkage shell is fixedly arranged in a wall body,transmission shells which are located on the upper side of the control shell and fixedly connected with the lower end of the linkage shell are fixedly arranged in the wall body in a front-back symmetrical mode relative to the control shell, a linkage cavity is formed in the linkage shell, an opening assembly is arranged in the linkage cavity, and the opening assembly comprises two sliders which are connected to the inner wall of the lower side of the linkage cavity in a front-back symmetrical and sliding mode relative to the linkage cavity. Opening and closing doors capable of moving front andback are adopted, by reducing the distance between the front side opening and closing door and the rear side opening and closing door, the door closing movement during fitting of a customer is realized, and thus the embarrassing situation caused by entering of other customers is prevented; and an indicating lamp is adopted, when the fitting customer enters the fitting room and steps on a pedal, the indicating lamp can form a loop with a power supply and is powered on to emit light, then the other customers are reminded that the fitting room is occupied, and therefore, the privacy of the fitting customer is further guaranteed.
Owner:JIAXING YIJIANTONG ELECTRICAL APPLIANCE
Intelligent financial payment terminal
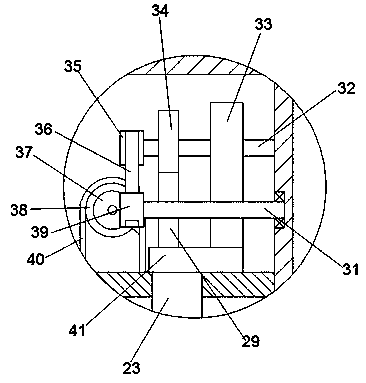
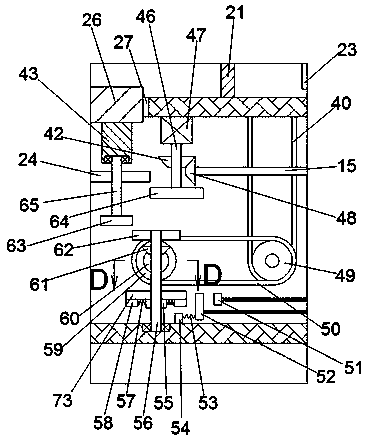
PendingCN112991644AProtect privacyImprove communication stabilityCash registersEmbedded systemData transmission
The invention provides an intelligent financial payment terminal. The terminal comprises a processing module, a payment module and a detachable printer, the processing module and the payment module are in data transmission and transmit exchange data related to payment, the processing module supplies power to the payment module, and the processing module and the detachable printer are in data transmission and transmit printing information data. And the detachable printer prints out the printing information. According to the invention, the problem of single function of the POS machine in the prior art is solved.
Owner:南京宁赛诺智能科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com