A method for system user to delegate others for security assistance
A system user and client technology, applied in the information field, can solve problems such as client business data security impact, multiple application security risks, system user account and privacy leakage, and achieve the effects of avoiding leakage, ensuring security, and ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solutions in the embodiments of the present invention are clearly and completely described below in conjunction with the drawings in the embodiments of the present invention.
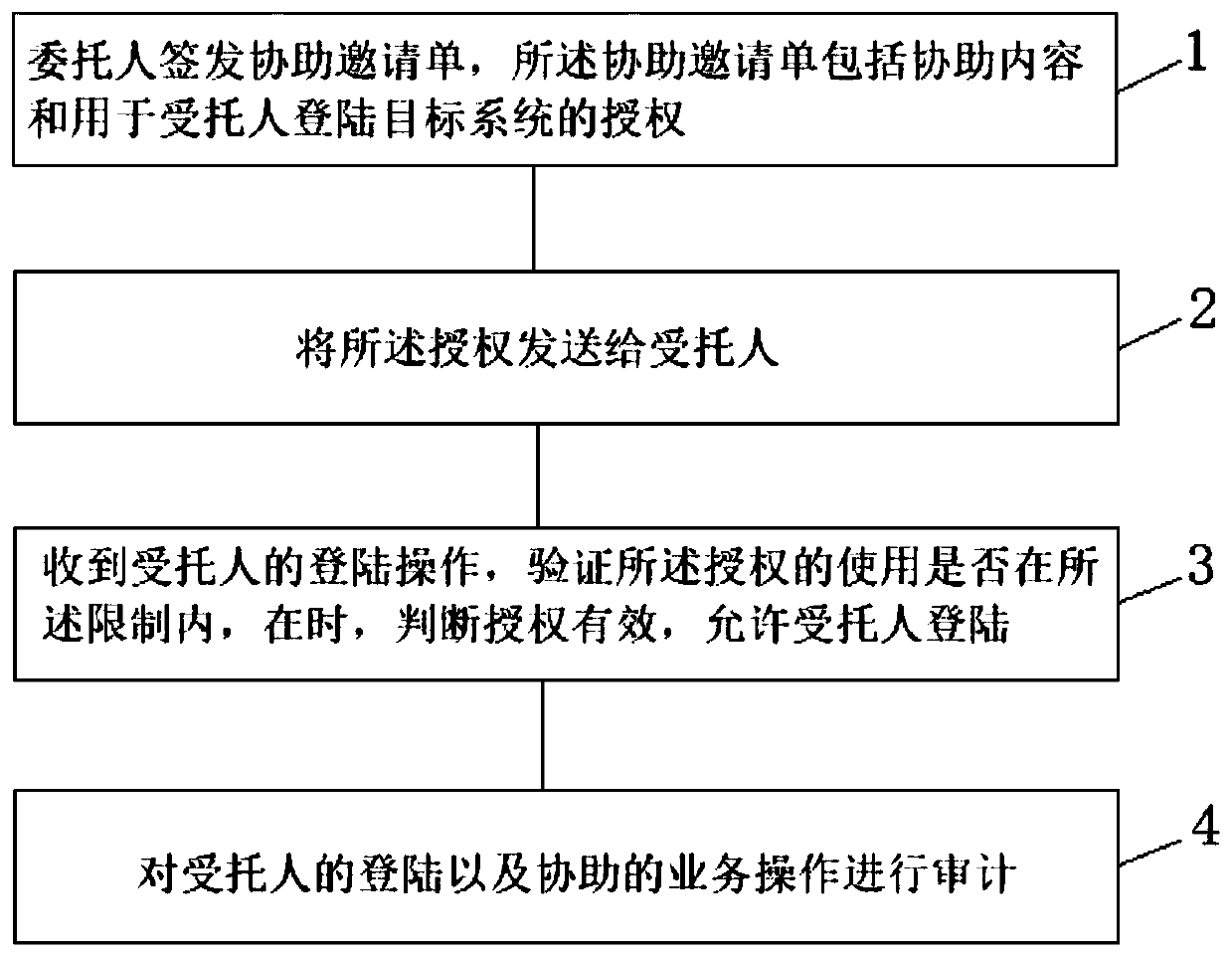
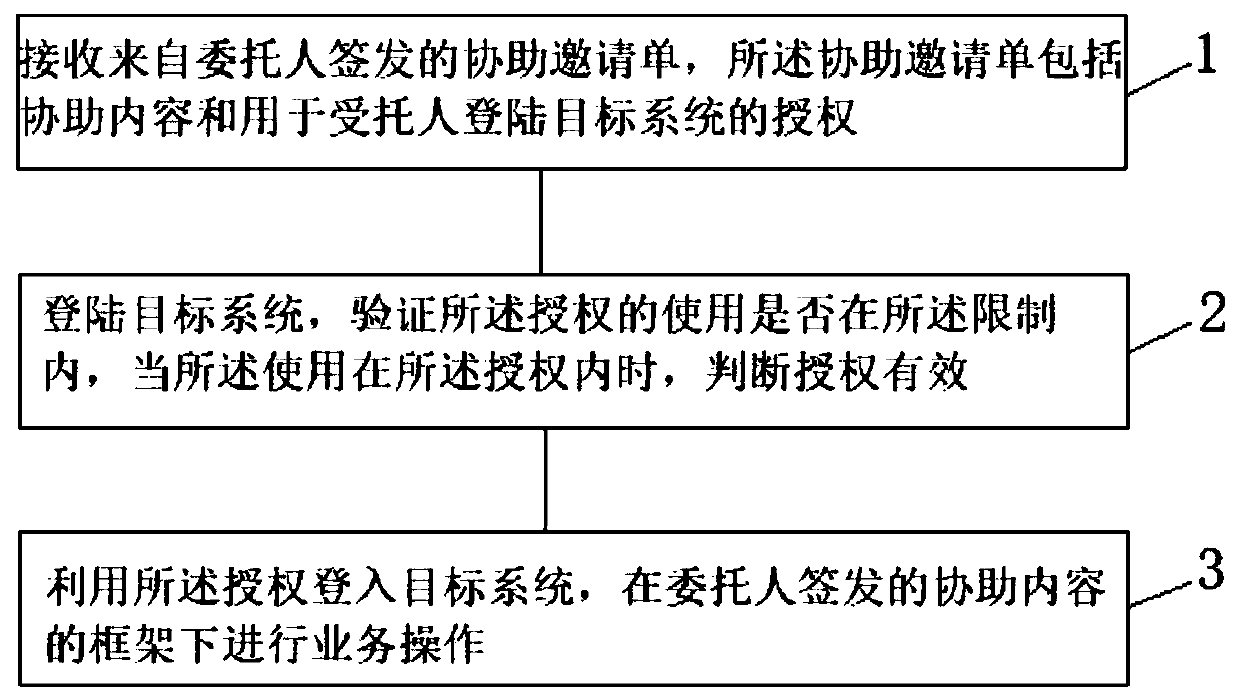
[0025] Such as figure 1 As shown, a method for a system user to entrust others to perform security assistance according to an embodiment of the present invention, the method includes the following steps:
[0026] Step 1: The principal issues an assistance invitation, which includes assistance content and authorization for the trustee to log in to the target system. The assistance content uses role-based access control (RBAC) to implement different assignments of assistance content to different delegates. The assistance content specifically includes assistance topics, available functional modules, available operating functions, accessible business documents, and usage restrictions. , the subject of assistance is a general description of this assistance, and the restrictions include ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com