Encryption and decryption method, device and system
A technology of encryption, decryption and ciphertext, applied in the field of communication, which can solve the problem of inability to complete the verification of the initiator device and the responder device.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0095] In order to make the description of the following embodiments clear and concise, a brief introduction of the relevant background is first given:
[0096] 1. Wireless Fidelity (English: wireless-fidelity, abbreviation: Wi-Fi) technology:
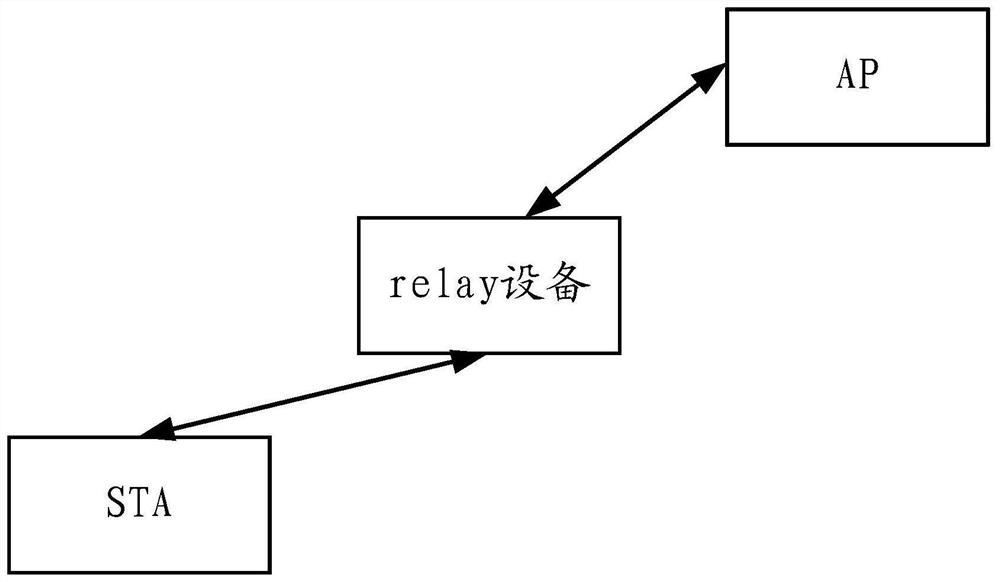
[0097]Wi-Fi technology is a short-range wireless communication technology. The basic standard of the Wi-Fi technology is the 802.11 protocol formulated by the Institute of Electrical and Electronics Engineers (English: institute of electrical and electronics engineers, abbreviation: IEEE). The common structure of Wi-Fi technology is that there is a central node called access point (English: accesspoint, abbreviation: AP), which periodically sends beacon (English: beacon) frames to announce the existence of the network to the outside world, and other nodes It is called a station (English: station, abbreviation: STA). It knows the existence of AP by actively sending a probe request (English: probe request) and then receiving a probe res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com