Video conference calling method and video conference calling device
A technology of video conferencing and calling method, which is applied in the direction of video conferencing system, usage of multiple keys/algorithms, two-way working system, etc. It can solve the problems of lack of certain security for domestic video conferencing, and achieve the effect of strengthening security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
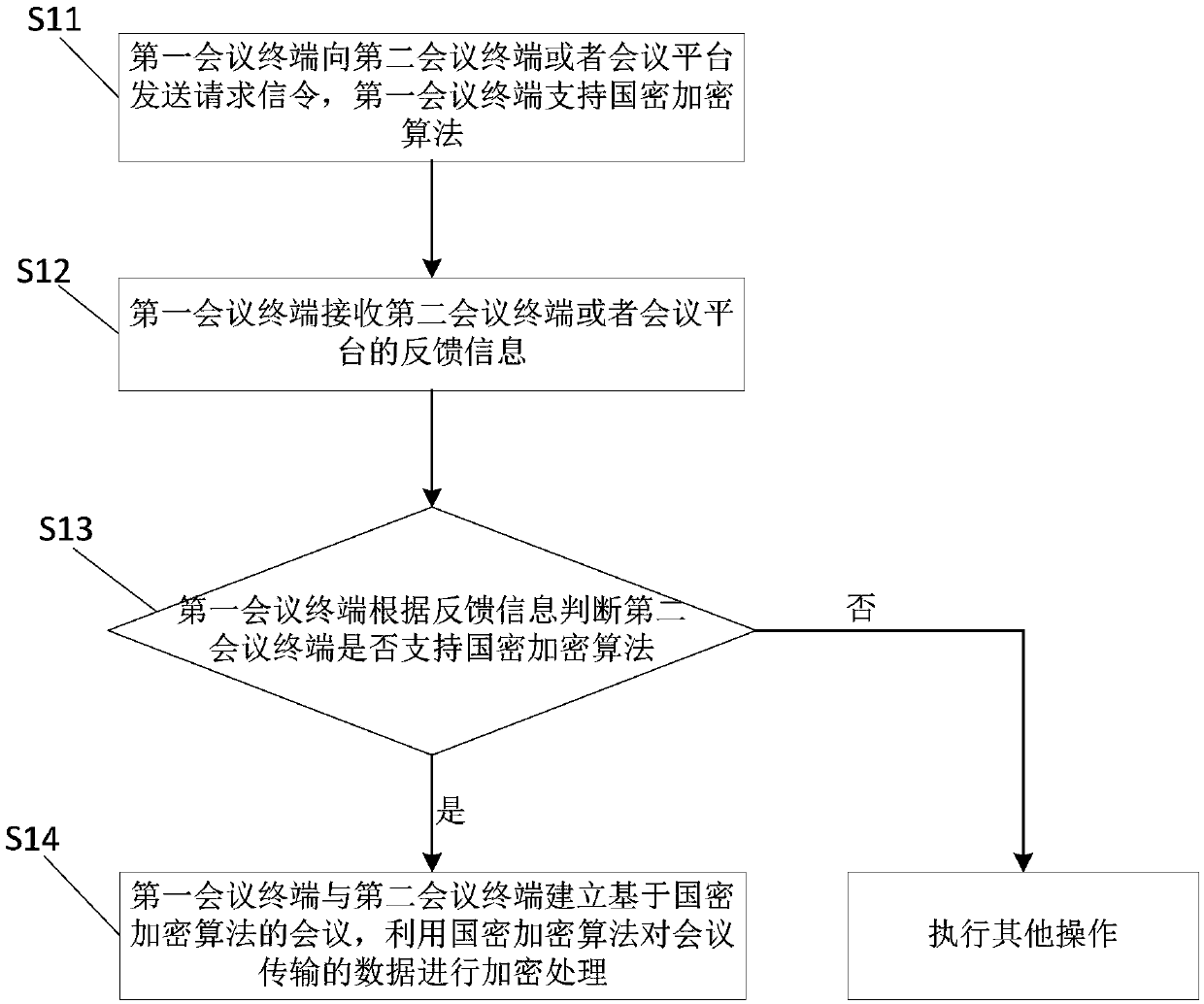
[0075] This embodiment provides a video conference calling method, such as figure 2 As shown, including the following steps:
[0076] Step S11: The first conference terminal sends request signaling to the second conference terminal or the conference platform, and the first conference terminal supports the national secret encryption algorithm.
[0077] The request signaling sent by the first conference terminal is generally H.225 signaling. The so-called first conference terminal supports the national secret encryption algorithm, which means that the H.245 capability set on the first conference terminal side has the OID corresponding to the national secret encryption algorithm registered in the ITU, for example, the SM4 national secret encryption algorithm The corresponding OID is 1.2.156.10197.1.104.
[0078] It should be noted that if the request signaling is sent to the second conference terminal, the request signaling can be H.225SETUP call request signaling, which means that th...
Embodiment 2
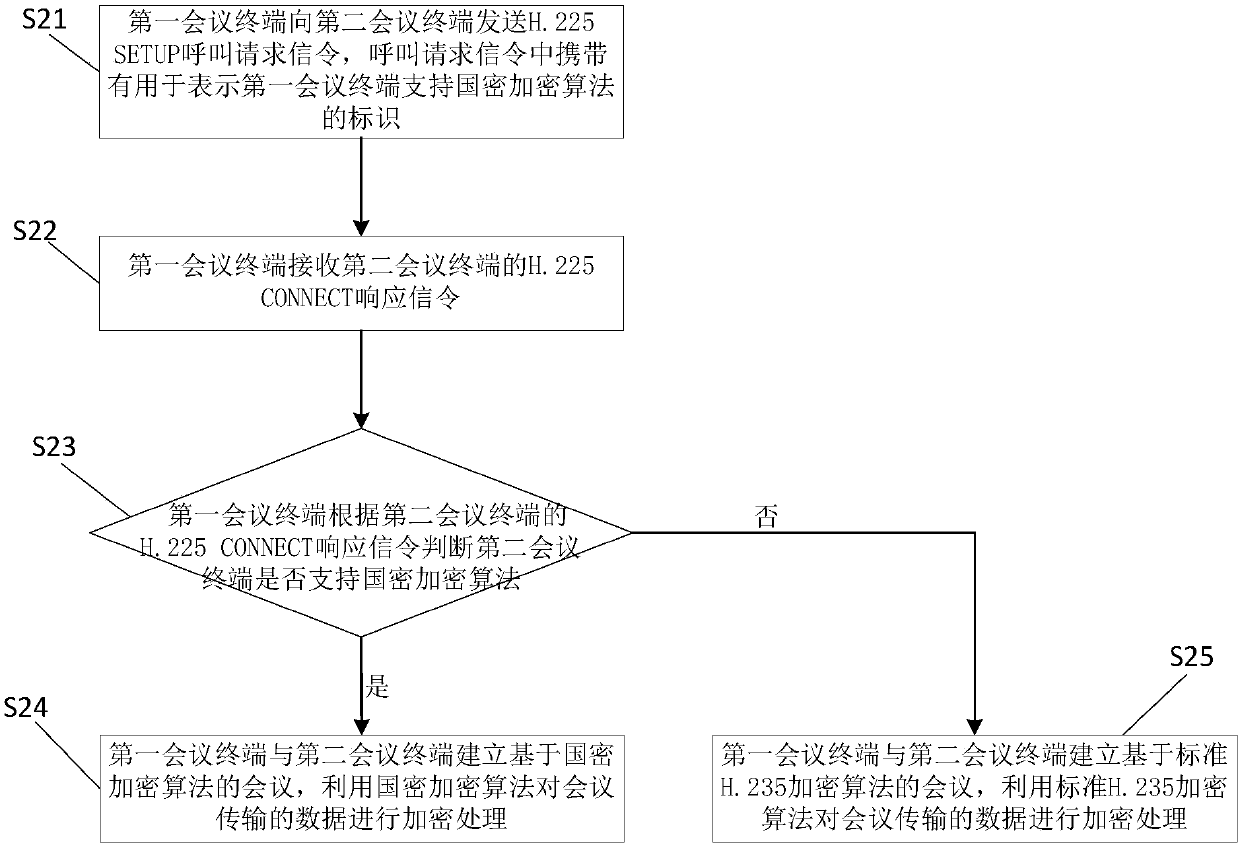
[0089] This embodiment provides a video conference calling method, which is applied to an unregistered first conference terminal and a second conference terminal, and the first conference terminal supports a national secret encryption algorithm. Such as image 3 As shown, including the following steps:
[0090] Step S21: The first conference terminal sends H.225 SETUP call request signaling to the second conference terminal. The call request signaling carries an identifier for indicating that the first conference terminal supports the national secret encryption algorithm.
[0091] The so-called first conference terminal supports the national secret encryption algorithm, which means that the H.245TCS capability on the first conference terminal side has the OID corresponding to the national secret encryption algorithm registered in the ITU, for example, the SM4 national secret encryption algorithm The corresponding OID is 1.2.156.10197.1.104. The identifier used to indicate that the...
Embodiment 3
[0101] This embodiment provides a video conference calling method, which is applied to the first conference terminal and the second conference terminal registered on the conference platform, and both the first conference terminal and the conference platform support the national secret encryption algorithm. Such as Figure 4 As shown, including the following steps:
[0102] Step S31: The first conference terminal sends ARQ query request signaling to the conference platform, and the query request signaling is used to query the address of the second conference terminal.
[0103] Step S32: The first conference terminal receives the ACF feedback information of the conference platform.
[0104] In this embodiment, the ACF feedback information of the conference platform includes the address of the second conference terminal. In addition, when the second conference terminal supports the national secret encryption algorithm, the feedback information also carries a message indicating that the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com