Judgment and identification method and system for suspicious violent and horrific person based on ontology identity features
A technology of identity characteristics and identification methods, which is applied in the identification method and system field of personnel suspected of violence and terrorism, can solve the problem of not considering the correlation of characteristic variables, and has not yet proposed a research and assessment model (classification and discrimination model) for personnel related to violence and terrorism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be further described in detail below in conjunction with the drawings and specific implementations of the specification.
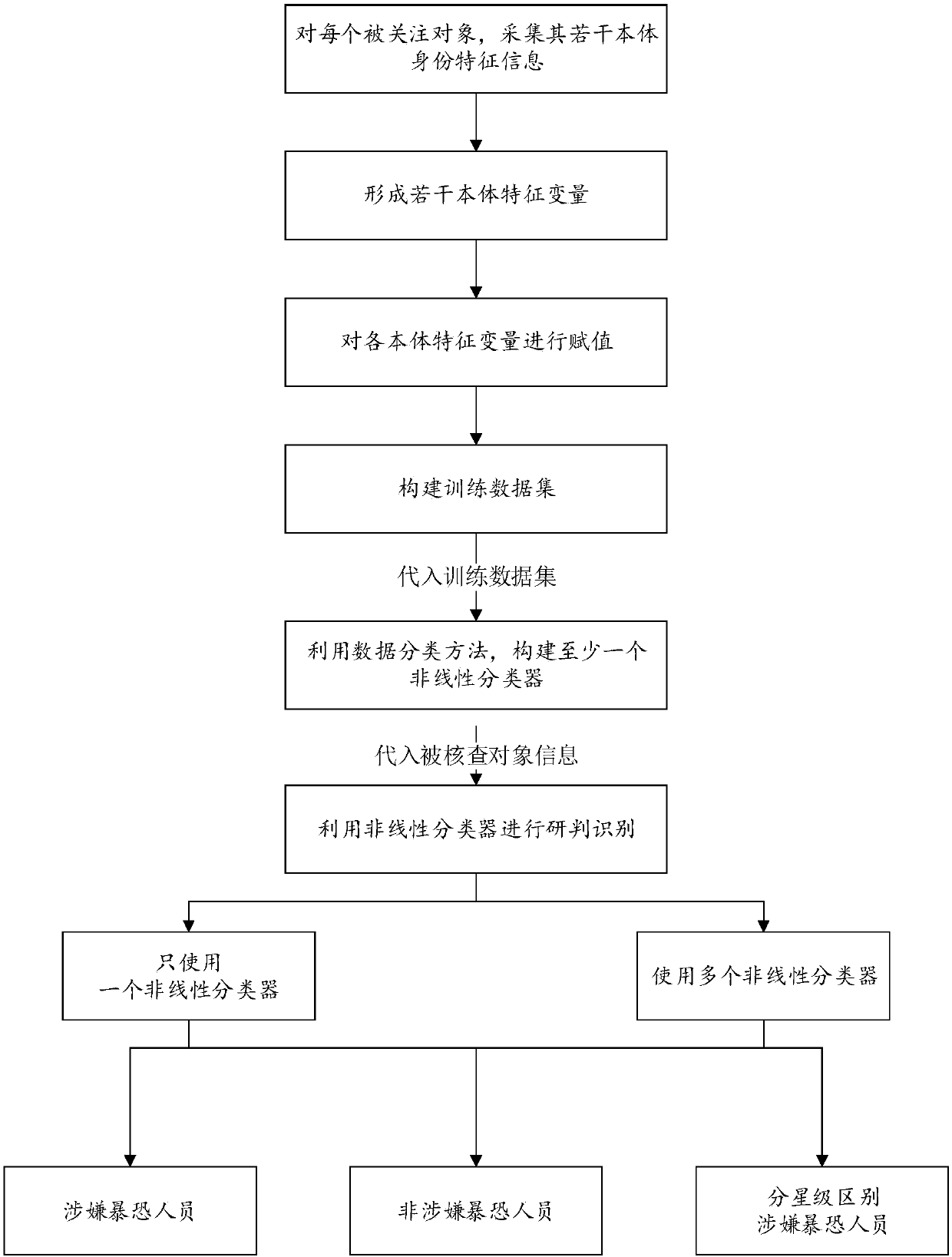
[0060] figure 1 Shows the flow chart of the method for investigating and identifying persons suspected of violent terrorists based on ontology identity features provided in the specific embodiments of the present invention. The method mainly includes:
[0061] (1) For each object of interest, collect several ontology identity feature information, and define them as a corresponding ontology feature variable. The ontology feature variable is called feature variable for short;
[0062] According to research findings, if the identity feature information of the ontology is too little, when the identity feature information of the ontology is converted into feature variables by the dummy variable method, it is not conducive to the analysis and judgment of the possible correlation between the feature variables. However, if the ontology T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com