Data sensitivity identification method and apparatus
An identification method and identification device technology, applied in the field of data processing, can solve problems such as inaccurate data desensitization strategies, lack of unified judgment rules, and leakage of sensitive data, and achieve the effects of improved security, accurate classification, and accurate sensitivity classification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
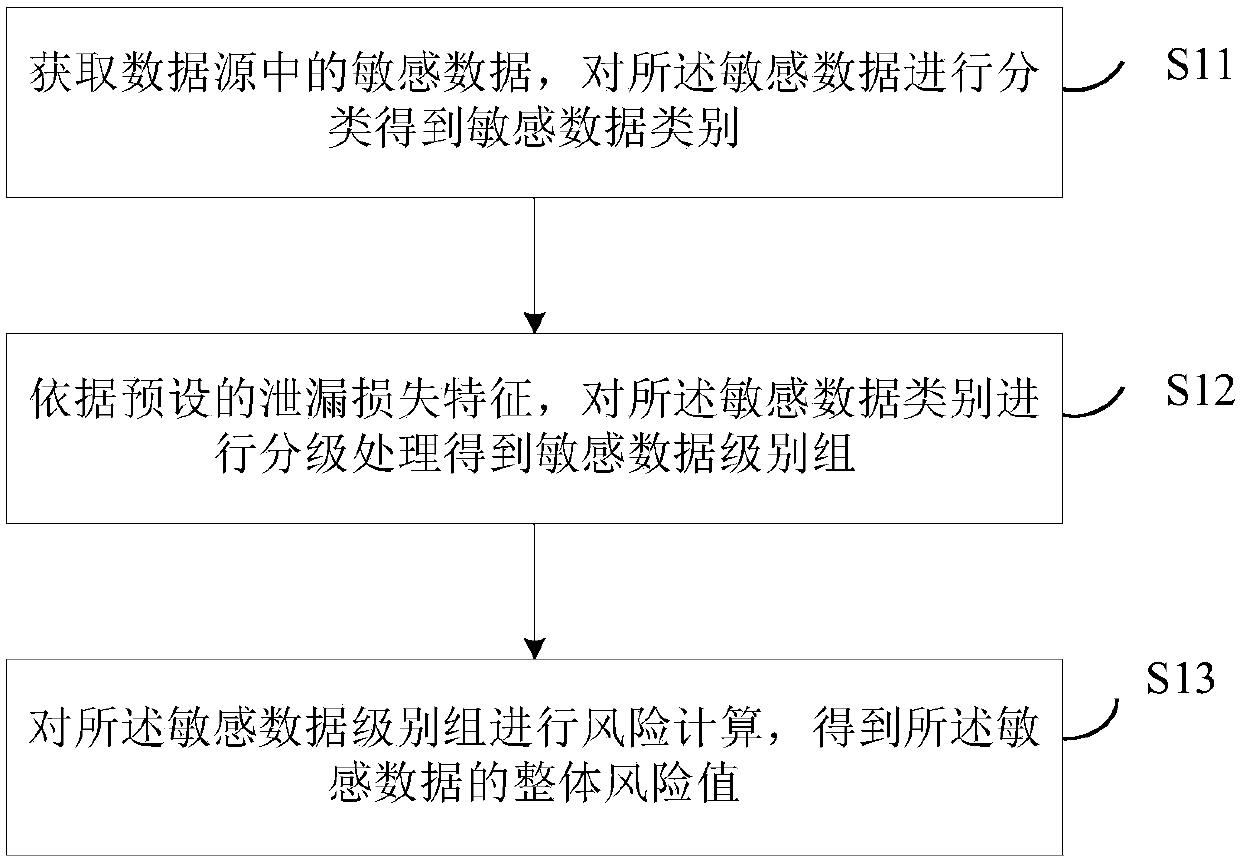
[0050] see figure 1 A data sensitivity identification method provided in Embodiment 1 of the present invention is characterized in that the method includes the following steps:
[0051] S11. Obtain sensitive data in the data source, and classify the sensitive data to obtain the sensitive data category;
[0052] It should be noted that since the sensitive category is the core of the sensitivity classification, it contains data columns with the same leakage hazard characteristics. In the existing process of classifying sensitive categories, people's subjective experience is often used for classification, but the present invention mainly relies on data structure information or data instance information for classification. That is, the process is:
[0053] Obtain sensitive data from data sources;
[0054] When the sensitive data includes data structure information, according to the data structure information and the data structure information in the preset sensitive category, c...
Embodiment 2
[0070] Referring to embodiment one of the present invention and figure 1 The specific process of steps S11 to S13 described in , firstly classify the acquired sensitive data, mainly according to the data structure information and data instance information. Classification results in sensitive subcategories.
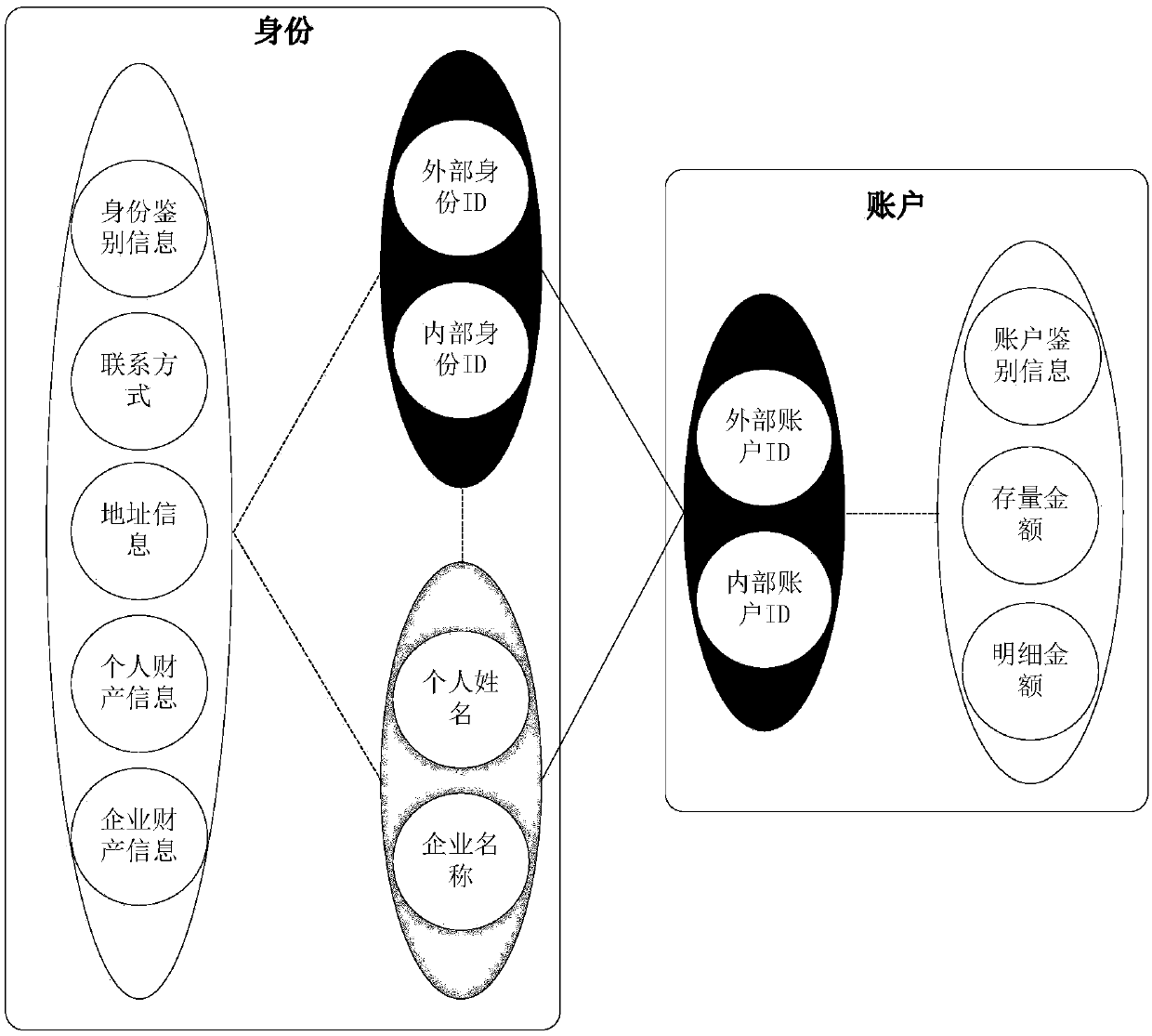
[0071] For example, see Table 1-1 for the main sensitive categories and sensitive subcategories of a commercial bank.
[0072] Table 1-1 Main sensitive categories and sensitive subcategories
[0073]
[0074] Based on Table 1-1, according to the specific requirements of internal data formats of different commercial banks, record the data result characteristics of each sensitive category and sensitive subcategory in the format of Table 1-2, such as data column names, data column types and other data structures information; and the data instance feature is the data instance information contained in the data column.
[0075] Table 1-2 Sensitive category classification f...
Embodiment 3
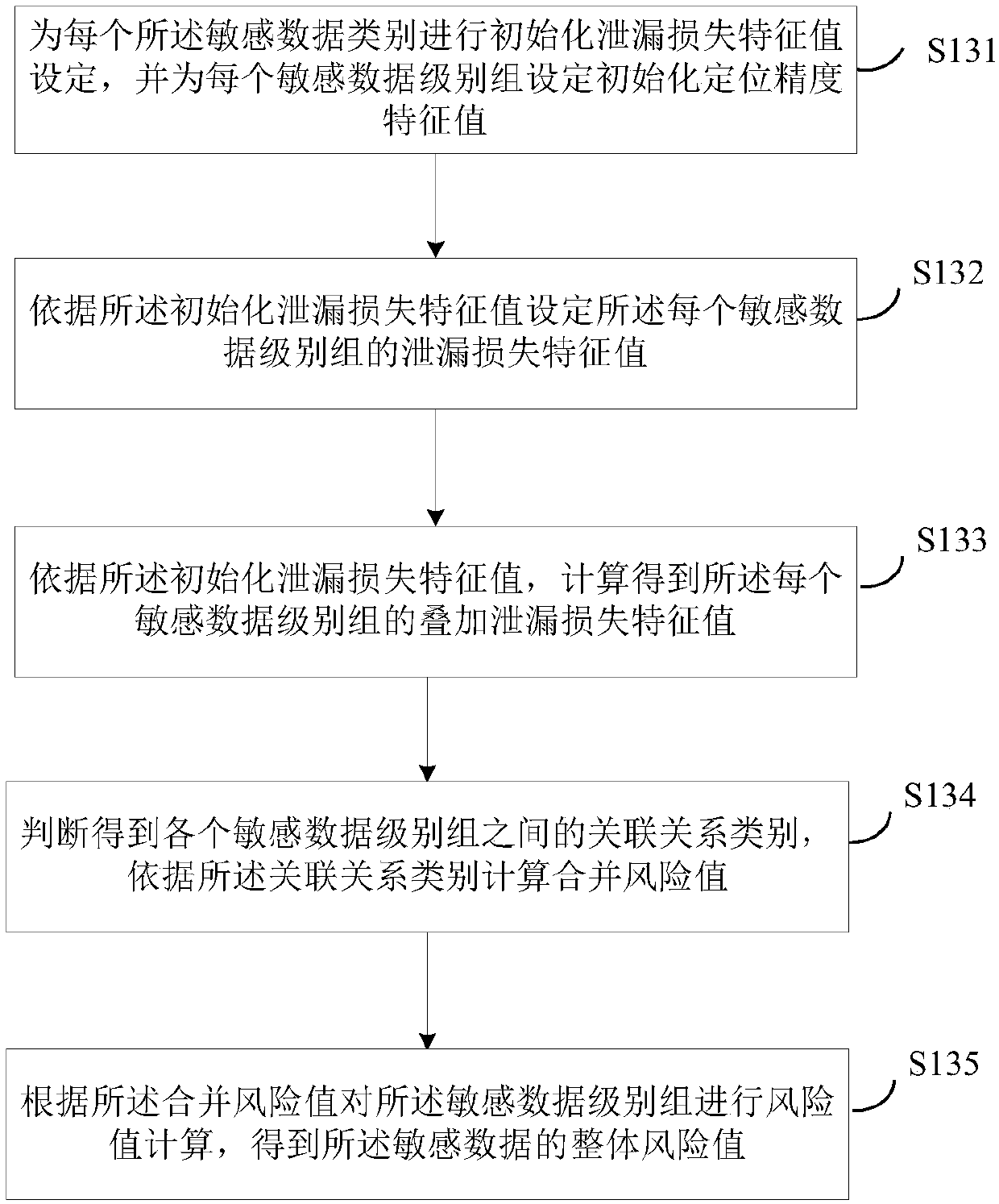
[0112] Corresponding to the data sensitivity identification method disclosed in Embodiment 1 and Embodiment 2 of the present invention, Embodiment 3 of the present invention also provides a data sensitivity identification device, see Figure 4 , the device consists of:
[0113] A classification module 1, configured to obtain sensitive data in a data source, and classify the sensitive data to obtain a sensitive data category;
[0114] A grading module 2, configured to perform grading processing on the sensitive data category to obtain a sensitive data level group according to preset leakage loss characteristics;
[0115] The calculation module 3 is configured to perform risk calculation on the sensitive data level group to obtain the overall risk value of the sensitive data.
[0116] Correspondingly, the method also includes:
[0117] The associated recording module 4 is configured to determine a set of related sensitive data categories according to the sensitive data categor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com