A separate deployment method for rssp-i security protocol
A technology that separates deployment and security protocols, applied in the field of security communications, can solve problems such as inability to meet different platform structures, and achieve the effect of protocol deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to further illustrate the features of the present invention, please refer to the following detailed description and accompanying drawings of the present invention. The accompanying drawings are for reference and description only, and are not intended to limit the protection scope of the present invention.
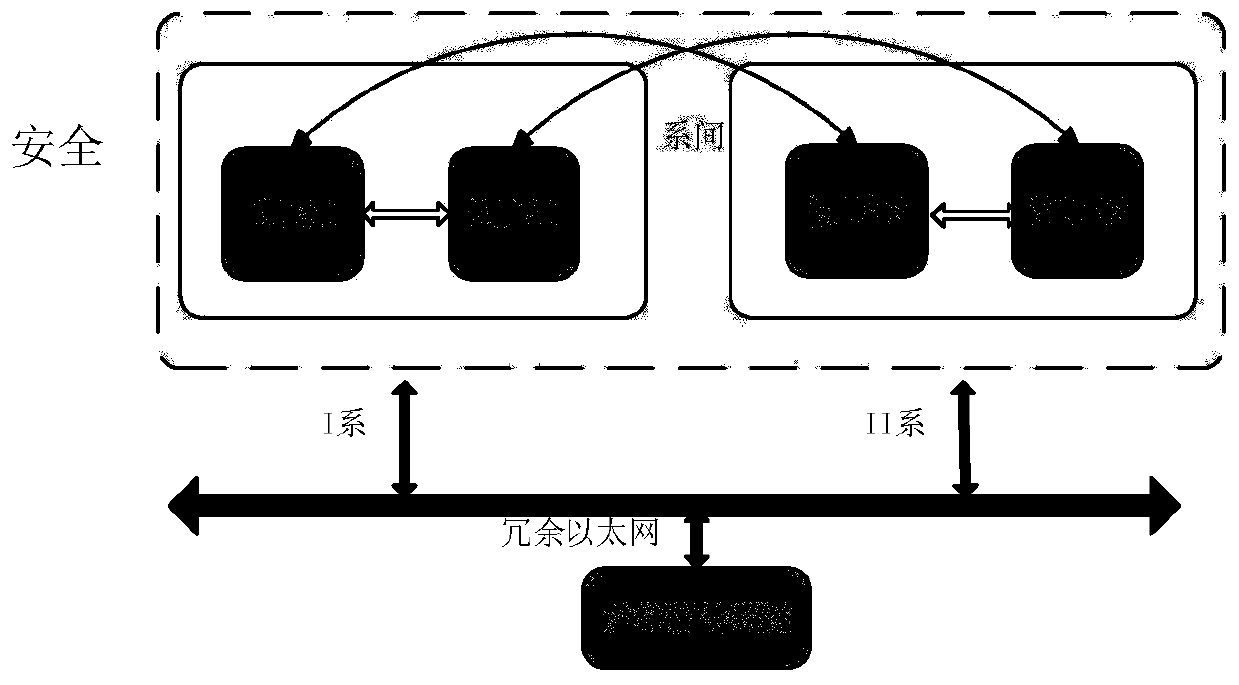
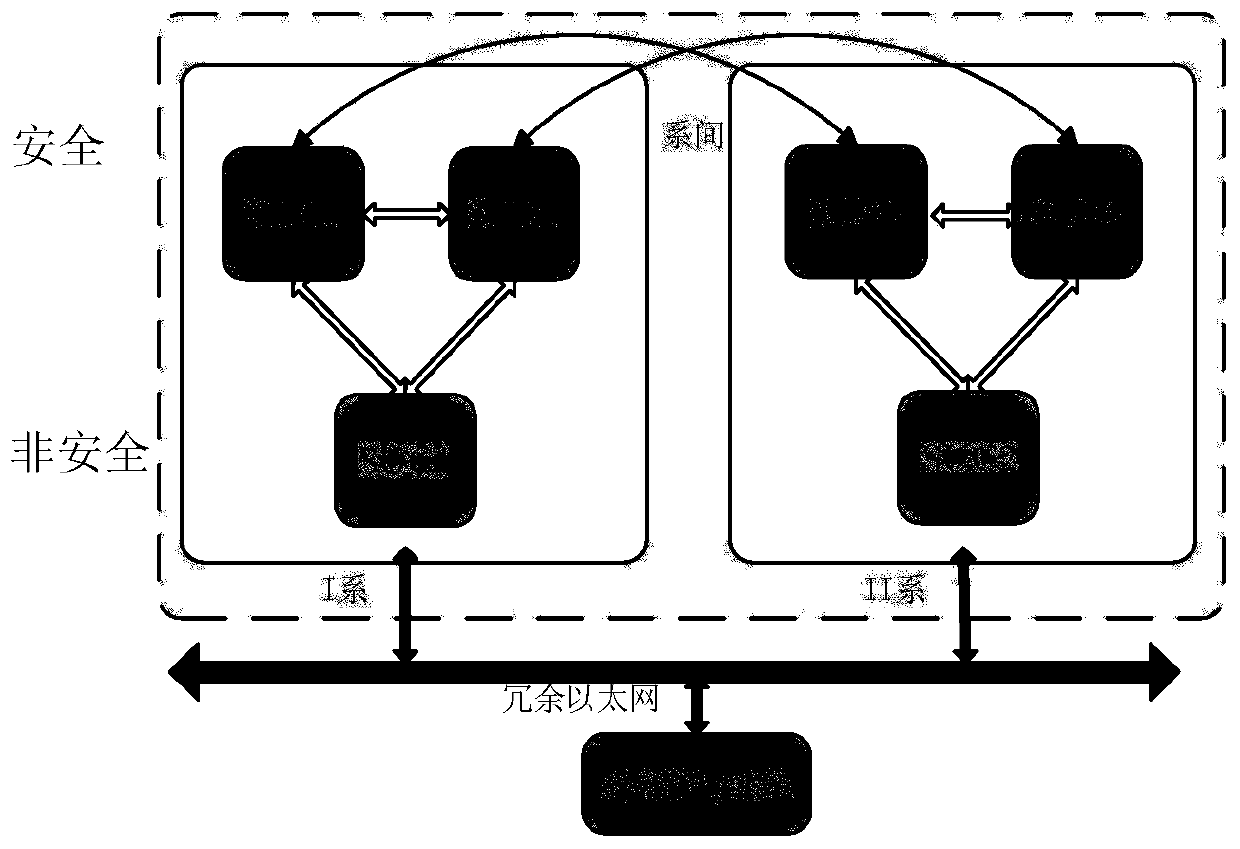
[0029] Such as Figure 3 to Figure 4 As shown, the present embodiment discloses a separate deployment method of RSSP-I security protocol, including the following steps S1 to S2:
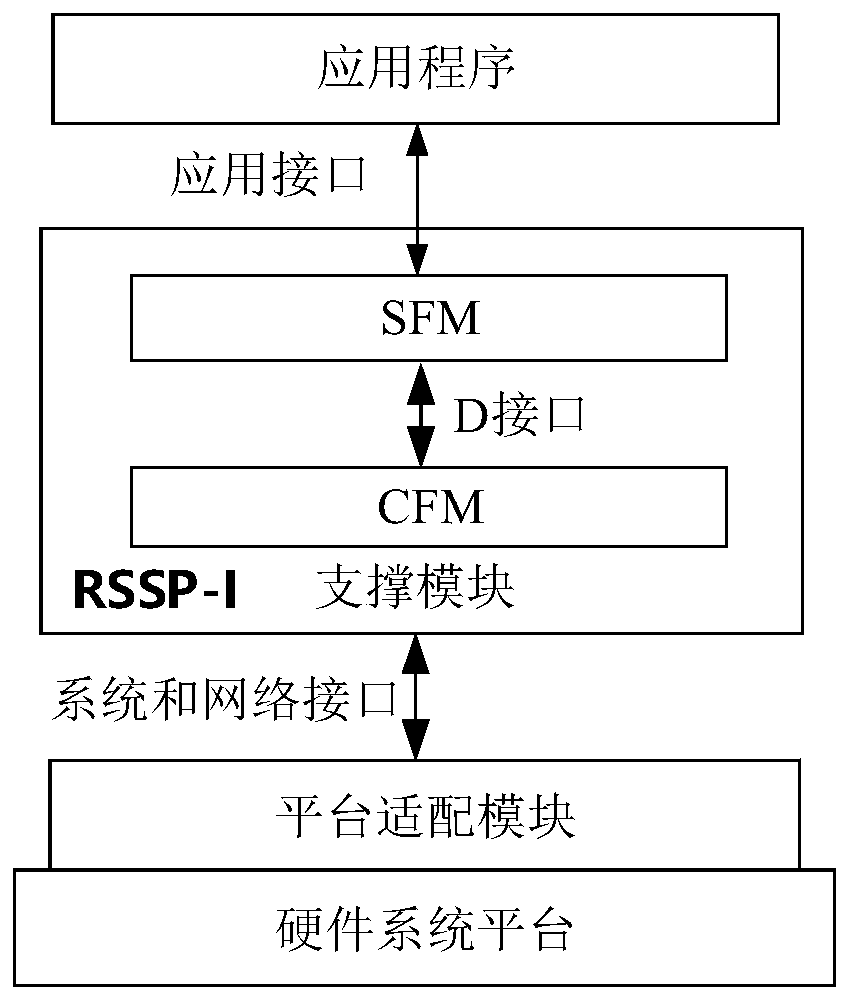
[0030] S1. Adding different adaptation layers to the protocol stack, wherein the adaptation layer includes a D interface adaptation layer, an application adaptation layer, a network adaptation layer and a system adaptation layer;
[0031] S2. Compile all RSSP-I functional modules of the protocol stack into a static logic library and deploy the static logic library to machines A, B, and C by using the corresponding adaptation layer.
[0032] Among them, such as image 3 As shown,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com